PT0-003 CompTIA PenTest+ Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CompTIA PT0-003 CompTIA PenTest+ Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
During a penetration test, a tester attempts to pivot from one Windows 10 system to another Windows system. The penetration tester thinks a local firewall is blocking connections. Which of the following command-line utilities built into Windows is most likely to disable the firewall?
During an assessment, a penetration tester runs the following command:
dnscmd.exe /config /serverlevelplugindll C:\users\necad-TA\Documents\adduser.dll
Which of the following is the penetration tester trying to achieve?
During an internal penetration test, the tester uses the following command:
C:\ Invoke-mimikatz.ps1 "kerberos::golden /domain:test.local /sid:S-1-5-21-3234... /target: dc01.test.local /service:CIFS /RC4:237749d82... /user:support.test.local /ptt"
Which of the following best describes the tester’s goal when executing this command?
A penetration tester has adversely affected a critical system during an engagement, which could have a material impact on the organization. Which of the following should the penetration tester do to address this issue?
Which of the following will reduce the possibility of introducing errors or bias in a penetration test report?
A penetration tester is performing an assessment focused on attacking the authentication identity provider hosted within a cloud provider. During the reconnaissance phase, the tester finds that the system is using OpenID Connect with OAuth and has dynamic registration enabled. Which of the following attacks should the tester try first?
auth=yYKGORbrpabgr842ajbvrpbptaui42342
When the tester logs in, the server sends only one Set-Cookie header, and the value is exactly the same as shown above. Which of the following vulnerabilities has the tester discovered?
With one day left to complete the testing phase of an engagement, a penetration tester obtains the following results from an Nmap scan:
Not shown: 1670 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.2.3 (CentOS)
3306/tcp open mysql MySQL (unauthorized)
8888/tcp open http lighttpd 1.4.32
Which of the following tools should the tester use to quickly identify a potential attack path?
A penetration tester wants to send a specific network packet with custom flags and sequence numbers to a vulnerable target. Which of the following should the tester use?
A penetration tester is testing a power plant's network and needs to avoid disruption to the grid. Which of the following methods is most appropriate to identify vulnerabilities in the network?
A penetration tester performs a service enumeration process and receives the following result after scanning a server using the Nmap tool:
PORT STATE SERVICE
22/tcp open ssh
25/tcp filtered smtp
111/tcp open rpcbind
2049/tcp open nfs
Based on the output, which of the following services provides the best target for launching an attack?
Which of the following activities should be performed to prevent uploaded web shells from being exploited by others?
Which of the following components should a penetration tester include in an assessment report?
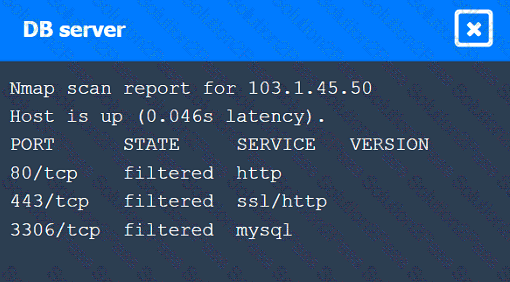
A penetration tester performs several Nmap scans against the web application for a client.
INSTRUCTIONS
Click on the WAF and servers to review the results of the Nmap scans. Then click on
each tab to select the appropriate vulnerability and remediation options.
If at any time you would like to bring back the initial state of the simulation, please
click the Reset All button.
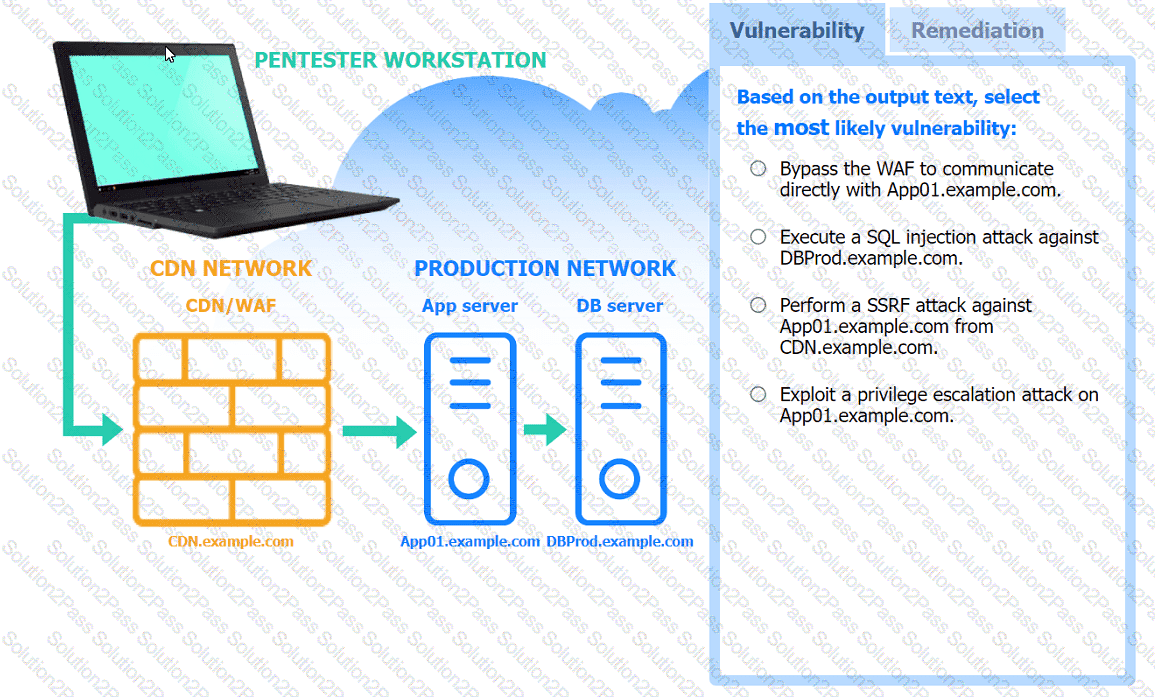
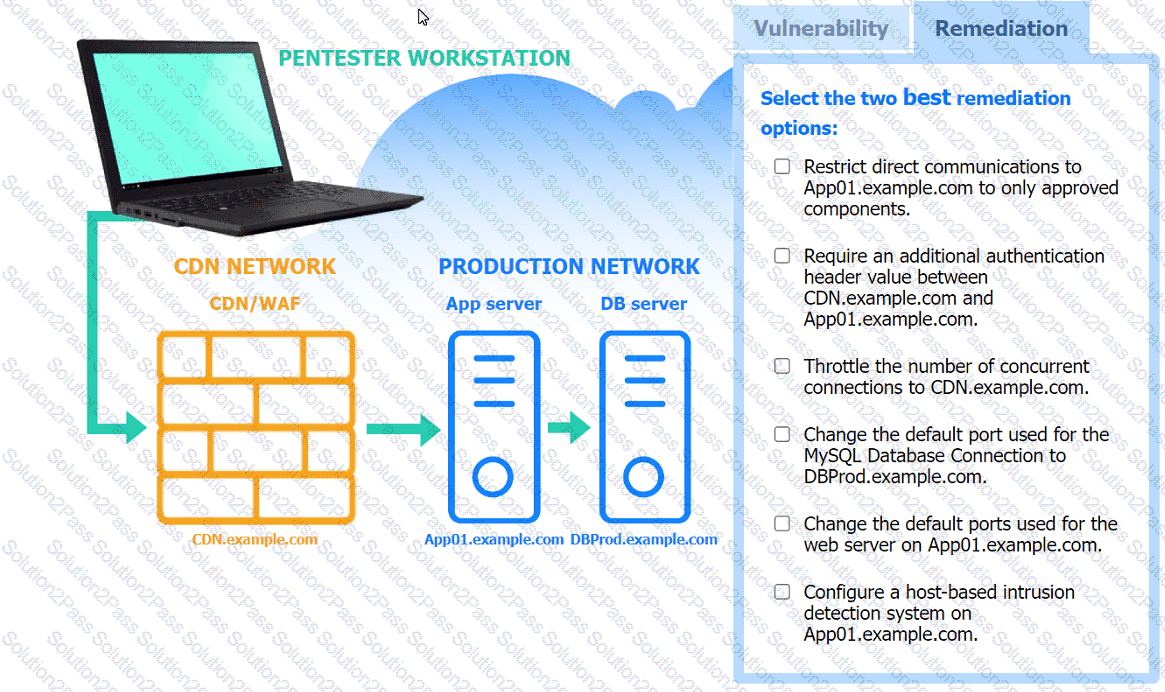
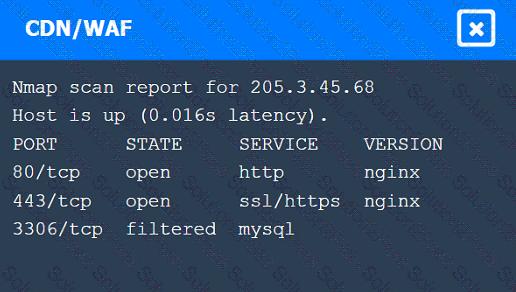
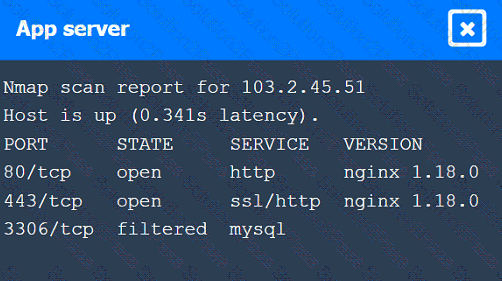
A penetration tester identifies the URL for an internal administration application while following DevOps team members on their commutes. Which of the following attacks did the penetration tester most likely use?
While performing an internal assessment, a tester uses the following command:
crackmapexec smb 192.168.1.0/24 -u user.txt -p Summer123@
Which of the following is the main purpose of the command?
A penetration tester cannot complete a full vulnerability scan because the client's WAF is blocking communications. During which of the following activities should the penetration tester discuss this issue with the client?
A penetration tester attempts to obtain the preshared key for a client's wireless network. Which of the following actions will most likely aid the tester?
A penetration tester gains shell access to a Windows host. The tester needs to permanently turn off protections in order to install additional payload. Which of the following commands is most appropriate?
A penetration tester completes a scan and sees the following output on a host:
bash
Copy code
Nmap scan report for victim (10.10.10.10)
Host is up (0.0001s latency)
PORT STATE SERVICE
161/udp open|filtered snmp
445/tcp open microsoft-ds
3389/tcp open microsoft-ds
Running Microsoft Windows 7
OS CPE: cpe:/o:microsoft:windows_7_sp0
The tester wants to obtain shell access. Which of the following related exploits should the tester try first?
 A screenshot of a computer Description automatically generated
A screenshot of a computer Description automatically generated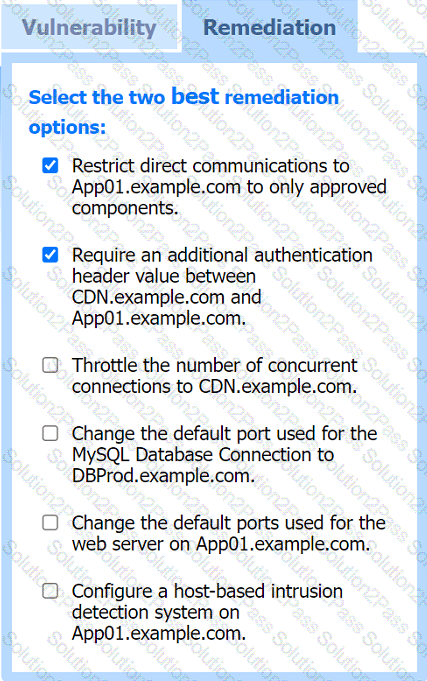 A screenshot of a computer screen Description automatically generated
A screenshot of a computer screen Description automatically generated