PT0-003 CompTIA PenTest+ Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CompTIA PT0-003 CompTIA PenTest+ Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Before starting an assessment, a penetration tester needs to scan a Class B IPv4 network for open ports in a short amount of time. Which of the following is the best tool for this task?
During a security assessment, a penetration tester gains access to an internal server and manipulates some data to hide its presence. Which of the following is the best way for the penetration tester to hide the activities performed?
A penetration tester is conducting a wireless security assessment for a client with 2.4GHz and 5GHz access points. The tester places a wireless USB dongle in the laptop to start capturing WPA2 handshakes. Which of the following steps should the tester take next?
A penetration tester obtains a regular domain user's set of credentials. The tester wants to attempt a dictionary attack by creating a custom word list based on the Active Directory password policy. Which of the following tools should the penetration tester use to retrieve the password policy?
A penetration tester has been asked to conduct a blind web application test against a customer's corporate website. Which of the following tools would be best suited to perform this assessment?
A penetration tester is trying to execute a post-exploitation activity and creates the follow script:
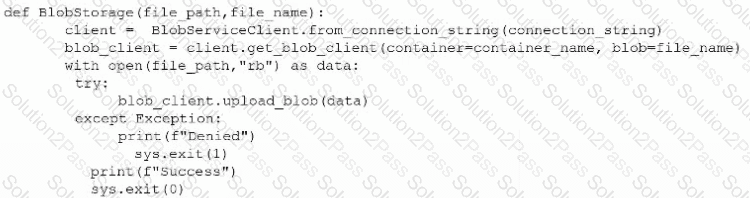
Which of the following best describes the tester's objective?
During a security assessment for an internal corporate network, a penetration tester wants to gain unauthorized access to internal resources by executing an attack that uses software to disguise itself as legitimate software. Which of the following host-based attacks should the tester use?
A penetration tester wants to create a malicious QR code to assist with a physical security assessment. Which of the following tools has the built-in functionality most likely needed for this task?
A penetration tester is conducting reconnaissance on a target network. The tester runs the following Nmap command: nmap -sv -sT -p - 192.168.1.0/24. Which of the following describes the most likely purpose of this scan?
A penetration tester wants to use the following Bash script to identify active servers on a network:
1 network_addr="192.168.1"
2 for h in {1..254}; do
3 ping -c 1 -W 1 $network_addr.$h > /dev/null
4 if [ $? -eq 0 ]; then
5 echo "Host $h is up"
6 else
7 echo "Host $h is down"
8 fi
9 done
Which of the following should the tester do to modify the script?
Which of the following OT protocols sends information in cleartext?
A penetration tester performs an assessment on the target company's Kubernetes cluster using kube-hunter. Which of the following types of vulnerabilities could be detected with the tool?
During a penetration test, the tester uses a vulnerability scanner to collect information about any possible vulnerabilities that could be used to compromise the network. The tester receives the results and then executes the following command:
snmpwalk -v 2c -c public 192.168.1.23
Which of the following is the tester trying to do based on the command they used?
During an engagement, a penetration tester wants to enumerate users from Linux systems by using finger and rwho commands. However, the tester realizes these commands alone will not achieve the desired result. Which of the following is the best tool to use for this task?
Which of the following components of a penetration test report most directly contributes to prioritizing remediations?
An internal penetration tester is on site assessing network access for company-owned mobile devices. Which of the following would be the best tool to identify the available networks?
While conducting a peer review for a recent assessment, a penetration tester finds the debugging mode is still enabled for the production system. Which of the following is most likely responsible for this observation?
A penetration tester discovers a deprecated directory in which files are accessible to anyone. Which of the following would most likely assist the penetration tester in finding sensitive information without raising suspicion?
During an assessment, a penetration tester runs the following command:
setspn.exe -Q /
Which of the following attacks is the penetration tester preparing for?
A penetration tester discovers evidence of an advanced persistent threat on the network that is being tested. Which of the following should the tester do next?
