SY0-701 CompTIA Security+ Exam 2025 Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CompTIA SY0-701 CompTIA Security+ Exam 2025 certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A new security regulation was announced that will take effect in the coming year. A company must comply with it to remain in business. Which of the following activities should the company perform next?
Which of the following would a security administrator use to comply with a secure baseline during a patch update?
Which of the following can a security director use to prioritize vulnerability patching within a company's IT environment?
A client demands at least 99.99% uptime from a service provider's hosted security services. Which of the following documents includes the information the service provider should return to the client?
A security administrator recently reset local passwords and the following values were recorded in the system:
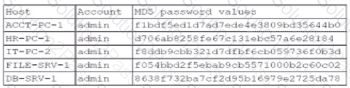
Which of the following in the security administrator most likely protecting against?
Which of the following strategies most effectively protects sensitive data at rest in a database?
An organization’s internet-facing website was compromised when an attacker exploited a buffer overflow. Which of the following should the organization deploy to best protect against similar attacks in the future?
Which of the following involves an attempt to take advantage of database misconfigurations?
Which of the following phases of an incident response involves generating reports?
A company decides to purchase an insurance policy. Which of the following risk management strategies is this company implementing?
Which of the following allows for the attribution of messages to individuals?
A financial institution would like to store its customer data m the cloud but still allow the data to be accessed and manipulated while encrypted. Doing so would prevent the cloud service provider from being able to decipher the data due to its sensitivity. The financial institution Is not concerned about computational overheads and slow speeds. Which of the following cryptographic techniques would best meet the requirement?
A security administrator would like to protect data on employees’ laptops. Which of the following encryption techniques should the security administrator use?
Which of the following should an organization focus on the most when making decisions about vulnerability prioritization?
The private key for a website was stolen, and a new certificate has been issued. Which of the following needs to be updated next?
The marketing department set up its own project management software without telling the appropriate departments. Which of the following describes this scenario?
A penetration test identifies that an SMBvl Is enabled on multiple servers across an organization. The organization wants to remediate this vulnerability in the most efficient way possible. Which of the following should the organization use for this purpose?
Which of the following is a common data removal option for companies that want to wipe sensitive data from hard drives in a repeatable manner but allow the hard drives to be reused?
An organization wants a third-party vendor to do a penetration test that targets a specific device. The organization has provided basic information about the device. Which of the following best describes this kind of penetration test?
A company asks a vendor to help its internal red team with a penetration test without providing too much detail about the infrastructure. Which of the following penetration testing methods does this scenario describe?
Prior to implementing a design change, the change must go through multiple steps to ensure that it does not cause any security issues. Which of the following is most likely to be one of those steps?
An administrator is Investigating an incident and discovers several users’ computers were Infected with malware after viewing files mat were shared with them. The administrator discovers no degraded performance in the infected machines and an examination of the log files does not show excessive failed logins. Which of the following attacks Is most likely the cause of the malware?
Which of the following is a primary security concern for a company setting up a BYOD program?
Which of the following should be deployed on an externally facing web server in order to establish an encrypted connection?
A group of developers has a shared backup account to access the source code repository. Which of the following is the best way to secure the backup account if there is an SSO failure?
Which of the following best describe a penetration test that resembles an actual external attach?
Which of the following would help ensure a security analyst is able to accurately measure the overall risk to an organization when a new vulnerability is disclosed?
A Chief Information Officer wants to ensure that network devices cannot connect to the public internet and the local network to directly perform firmware updates. The IT team must manually perform the update process by using a portable device. Which of the following architecture types best fits this description?
Which of the following should an internal auditor check for first when conducting an audit of the organization's risk management program?
Which of the following describes the difference between encryption and hashing?
