PAM-CDE-RECERT CyberArk CDE Recertification Free Practice Exam Questions (2025 Updated)
Prepare effectively for your CyberArk PAM-CDE-RECERT CyberArk CDE Recertification certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which keys are required to be present in order to start the PrivateArk Server service?
Which component must be installed on the Vault if Distributed Vaults is used with PSM?
Ad-Hoc Access (formerly Secure Connect) provides the following features. Choose all that apply.
In your organization the “click to connect” button is not active by default.
How can this feature be activated?
The Accounts Feed contains:
A company requires challenge/response multi-factor authentication for PSMP sessions. Which server must you integrate with the CyberArk vault?
Your customer, ACME Corp, wants to store the Safes Data in Drive D instead of Drive C.
Which file should you edit?
Which parameters can be used to harden the Credential Files (CredFiles) while using CreateCredFile Utility? (Choose three.)
You are configuring the vault to send syslog audit data to your organization's SIEM solution. What is a valid value for the SyslogServerProtocol parameter in DBPARM.ini file?
Which SMTP address can be set on the Notification Settings page to re-invoke the ENE setup wizard after the initial Vault installation.
CyberArk implements license limits by controlling the number and types of users that can be provisioned in the vault.
You have been asked to identify the up or down status of Vault services.
Which CyberArk utility can you use to accomplish this task?
In PVWA, you are attempting to play a recording made of a session by user jsmith, but there is no option to “Fast Forward” within the video. It plays and only allows you to skip between commands instead. You are also unable to download the video.
What could be the cause?
Users who have the 'Access Safe without confirmation' safe permission on a safe where accounts are configured for Dual control, still need to request approval to use the account.
Which report shows the accounts that are accessible to each user?
The Privileged Access Management solution provides an out-of-the-box target platform to manage SSH keys, called UNIX Via SSH Keys.
How are these keys managed?
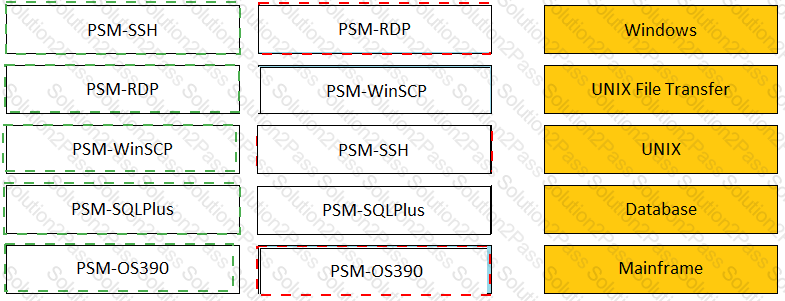
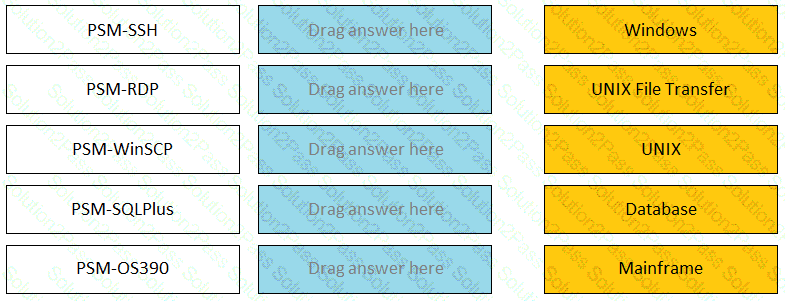
Match the connection component to the corresponding OS/Function.
Which user is automatically added to all Safes and cannot be removed?
Which tools are used during a CPM renaming process?
What is a prerequisite step betore CyberArk can be configured to support RADIUS authentication?