PAM-DEF CyberArk Defender - PAM Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CyberArk PAM-DEF CyberArk Defender - PAM certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
You are creating a shared safe for the help desk.
What must be considered regarding the naming convention?
Which of the following are secure options for storing the contents of the Operator CD, while still allowing the contents to be accessible upon a planned Vault restart? (Choose three.)
A user needs to view recorded sessions through the PVWA.
Without giving auditor access, which safes does a user need access to view PSM recordings? (Choose two.)
A Logon Account can be specified in the Master Policy.
What is the chief benefit of PSM?
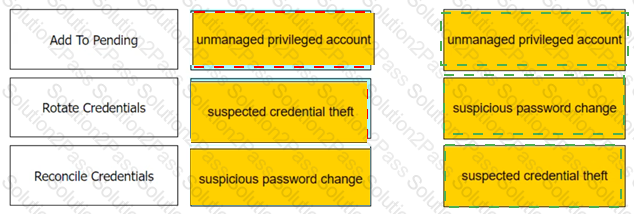
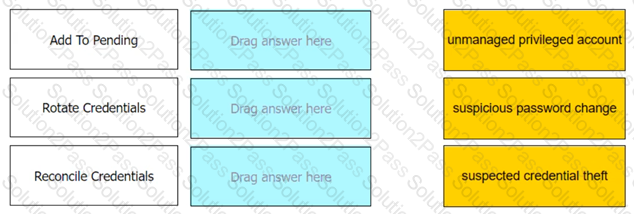
Match each automatic remediation to the correct PTA security event.
What is the configuration file used by the CPM scanner when scanning UNIX/Linux devices?
What does the Export Vault Data (EVD) utility do?
To ensure all sessions are being recorded, a CyberArk administrator goes to the master policy and makes configuration changes.
Which configuration is correct?
You created a new platform by duplicating the out-of-box Linux through the SSH platform.
Without any change, which Text Recorder Type(s) will the new platform support? (Choose two.)
All of your Unix root passwords are stored in the safe UnixRoot. Dual control is enabled for some of the accounts in that safe. The members of the AD group UnixAdmins need to be able to use the show, copy, and connect buttons on those passwords at any time without confirmation. The members of the AD group Operations Staff need to be able to use the show, copy and connect buttons on those passwords on an emergency basis, but only with the approval of a member of Operations Managers never need to be able to use the show, copy or connect buttons themselves.
Which safe permission do you need to grant Operations Staff? Check all that apply.