PAM-DEF CyberArk Defender - PAM Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CyberArk PAM-DEF CyberArk Defender - PAM certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A newly created platform allows users to access a Linux endpoint. When users click to connect, nothing happens.
Which piece of the platform is missing?
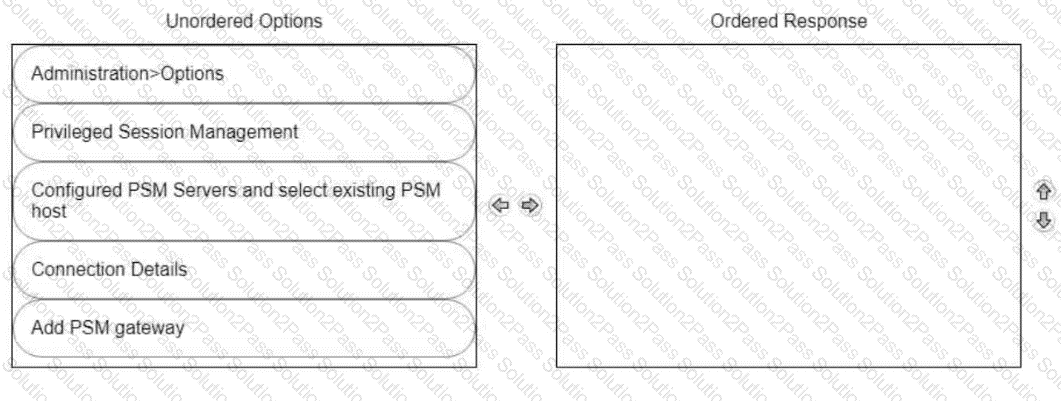
A new HTML5 Gateway has been deployed in your organization.
Where do you configure the PSM to use the HTML5 Gateway?
Which of the following statements are NOT true when enabling PSM recording for a target Windows server? (Choose all that apply)
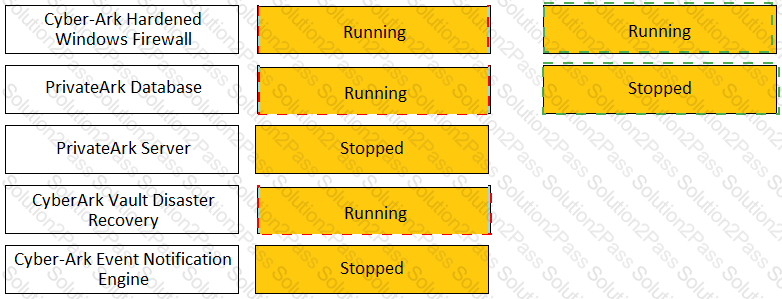
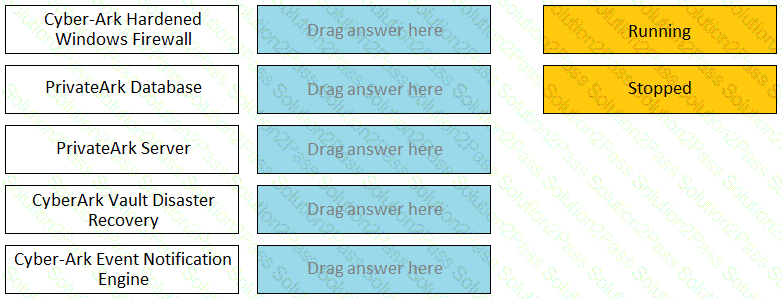
Match the Status of Service on a DR Vault to what is displayed when it is operating normally in Replication mode.
If the AccountUploader Utility is used to create accounts with SSH keys, which parameter do you use to set the full or relative path of the SSH private key file that will be attached to the account?
Which Cyber Are components or products can be used to discover Windows Services or Scheduled Tasks that use privileged accounts? Select all that apply.
What is the purpose of the PrivateArk Database service?
Which processes reduce the risk of credential theft? (Choose two.)
Before failing back to the production infrastructure after a DR exercise, what must you do to maintain audit history during the DR event?
It is possible to restrict the time of day, or day of week that a [b]verify[/b] process can occur
Which onboarding method would you use to integrate CyberArk with your accounts provisioning process?
Which methods can you use to add a user directly to the Vault Admin Group? (Choose three.)
Which permissions are needed for the Active Directory user required by the Windows Discovery process?
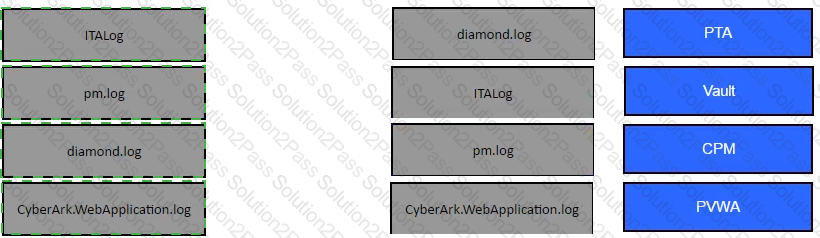
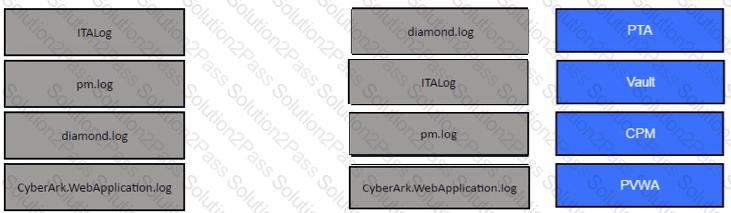
Match the log file name with the CyberArk Component that generates the log.

The Accounts Feed contains:
CyberArk recommends implementing object level access control on all Safes.
You are onboarding an account that is not supported out of the box.
What should you do first to obtain a platform to import?
In the Private Ark client, how do you add an LDAP group to a CyberArk group?
You are troubleshooting a PVWA slow response.
Which log files should you analyze first? (Choose two.)
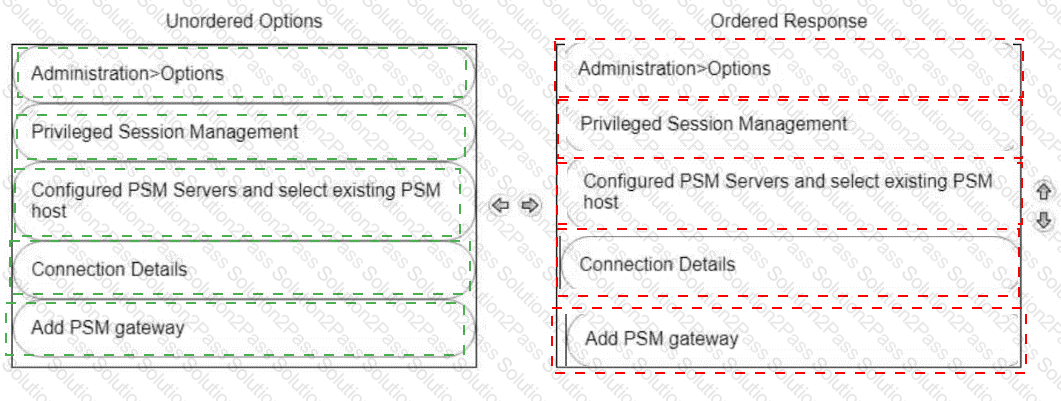
A new HTML5 Gateway has been deployed in your organization.
From the PVWA, arrange the steps to configure a PSM host to use the HTML5 Gateway in the correct sequence.