312-39 ECCouncil Certified SOC Analyst (CSA) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ECCouncil 312-39 Certified SOC Analyst (CSA) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
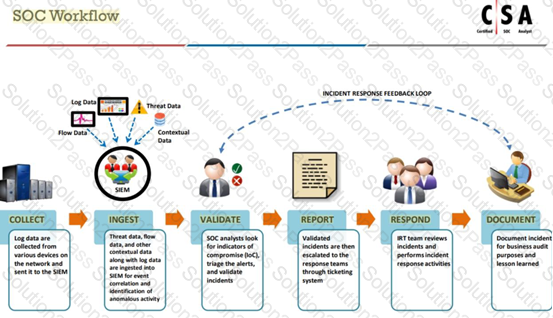
What is the correct sequence of SOC Workflow?
Which of the following steps of incident handling and response process focus on limiting the scope and extent of an incident?
Which of the following formula represents the risk levels?
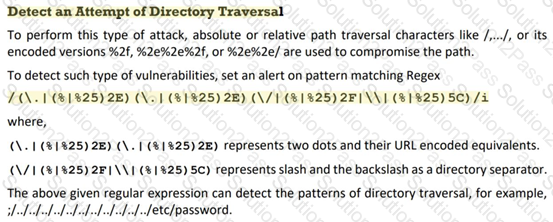
John, a SOC analyst, while monitoring and analyzing Apache web server logs, identified an event log matching Regex /(\.|(%|%25)2E)(\.|(%|%25)2E)(\/|(%|%25)2F|\\|(%|%25)5C)/i.
What does this event log indicate?
Which encoding replaces unusual ASCII characters with "%" followed by the character’s two-digit ASCII code expressed in hexadecimal?
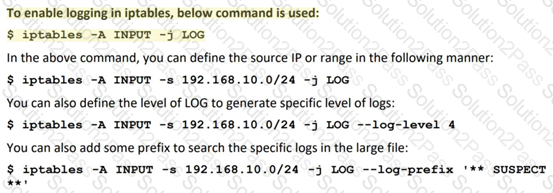
Which of the following command is used to enable logging in iptables?
According to the Risk Matrix table, what will be the risk level when the probability of an attack is very high, and the impact of that attack is major?
NOTE: It is mandatory to answer the question before proceeding to the next one.
Which of the following attack inundates DHCP servers with fake DHCP requests to exhaust all available IP addresses?
Jane, a security analyst, while analyzing IDS logs, detected an event matching Regex /((\%3C)|<)((\%69)|i|(\% 49))((\%6D)|m|(\%4D))((\%67)|g|(\%47))[^\n]+((\%3E)|>)/|.
What does this event log indicate?
Properly applied cyber threat intelligence to the SOC team help them in discovering TTPs.
What does these TTPs refer to?