312-49v10 ECCouncil Computer Hacking Forensic Investigator (CHFI-v10) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ECCouncil 312-49v10 Computer Hacking Forensic Investigator (CHFI-v10) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What is the framework used for application development for iOS-based mobile devices?
Smith, an employee of a reputed forensic investigation firm, has been hired by a private organization to investigate a laptop that is suspected to be involved in the hacking of the organization’s DC server. Smith wants to find all the values typed into the Run box in the Start menu. Which of the following registry keys will Smith check to find the above information?
Rusty, a computer forensics apprentice, uses the command nbtstat –c while analyzing the network information in a suspect system. What information is he looking for?
If the partition size is 4 GB, each cluster will be 32 K. Even if a file needs only 10 K, the entire 32 K will be allocated, resulting in 22 K of ________.
Which of the following file system uses Master File Table (MFT) database to store information about every file and directory on a volume?
Which of the following files contains the traces of the applications installed, run, or uninstalled from a system?
The Apache server saves diagnostic information and error messages that it encounters while processing requests. The default path of this file is usr/local/apache/logs/error.log in Linux. Identify the Apache error log from the following logs.
What does the Rule 101 of Federal Rules of Evidence states?
Which of these Windows utility help you to repair logical file system errors?
What is the name of the first reserved sector in File allocation table?
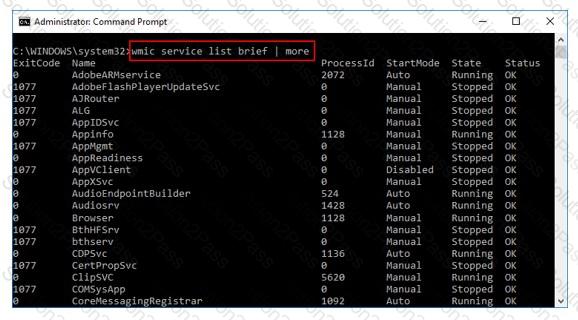
What is the investigator trying to view by issuing the command displayed in the following screenshot?
Which U.S. law sets the rules for sending emails for commercial purposes, establishes the minimum requirements for commercial messaging, gives the recipients of emails the right to ask the senders to stop emailing them, and spells out the penalties in case the above said rules are violated?
Sheila is a forensics trainee and is searching for hidden image files on a hard disk. She used a forensic investigation tool to view the media in hexadecimal code for simplifying the search process. Which of the following hex codes should she look for to identify image files?
Which among the following web application threats is resulted when developers expose various internal implementation objects, such as files, directories, database records, or key-through references?
Which command line tool is used to determine active network connections?
During forensics investigations, investigators tend to collect the system time at first and compare it with UTC. What does the abbreviation UTC stand for?
Which rule requires an original recording to be provided to prove the content of a recording?
Which of the following reports are delivered under oath to a board of directors/managers/panel of the jury?
What encryption technology is used on Blackberry devices Password Keeper?
What stage of the incident handling process involves reporting events?
Which network attack is described by the following statement? "At least five Russian major banks came under a continuous hacker attack, although online client services were not disrupted. The attack came from a wide-scale botnet involving at least 24,000 computers, located in 30 countries."
Daryl, a computer forensics investigator, has just arrived at the house of an alleged computer hacker. Daryl takes pictures and tags all computer and peripheral equipment found in the house. Daryl packs all the items found in his van and takes them back to his lab for further examination. At his lab, Michael his assistant helps him with the investigation. Since Michael is still in training, Daryl supervises all of his work very carefully. Michael is not quite sure about the procedures to copy all the data off the computer and peripheral devices. How many data acquisition tools should Michael use when creating copies of the evidence for the investigation?
This type of testimony is presented by someone who does the actual fieldwork and does not offer a view in court.
When marking evidence that has been collected with the aa/ddmmyy/nnnn/zz format, what does the nnn denote?
Charles has accidentally deleted an important file while working on his Mac computer. He wants to recover the deleted file as it contains some of his crucial business secrets. Which of the following tool will help Charles?
A master boot record (MBR) is the first sector (“sector zero”) of a data storage device. What is the size of MBR?
When carrying out a forensics investigation, why should you never delete a partition on a dynamic disk?
What type of flash memory card comes in either Type I or Type II and consumes only five percent of the power required by small hard drives?
Where are files temporarily written in Unix when printing?
If a PDA is seized in an investigation while the device is turned on, what would be the proper procedure?
