312-49v10 ECCouncil Computer Hacking Forensic Investigator (CHFI-v10) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ECCouncil 312-49v10 Computer Hacking Forensic Investigator (CHFI-v10) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A computer forensics investigator is inspecting the firewall logs for a large financial institution that has employees working 24 hours a day, 7 days a week.
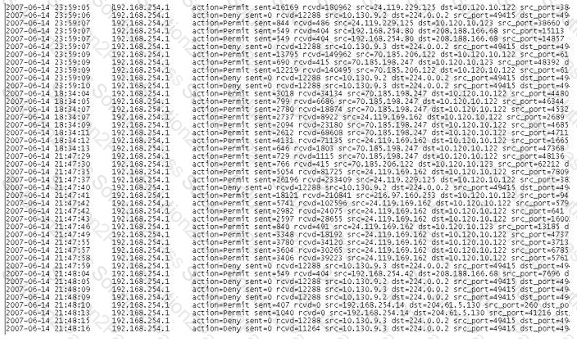
What can the investigator infer from the screenshot seen below?
Before performing a logical or physical search of a drive in Encase, what must be added to the program?
An expert witness is a __________________ who is normally appointed by a party to assist the formulation and preparation of a party’s claim or defense.
All Blackberry email is eventually sent and received through what proprietary RIM-operated mechanism?
What is the primary function of the tool CHKDSK in Windows that authenticates the file system reliability of a volume?
What does the part of the log, “% SEC-6-IPACCESSLOGP”, extracted from a Cisco router represent?
When operating systems mark a cluster as used but not allocated, the cluster is considered as _________
Which of the following Event Correlation Approach checks and compares all the fields systematically and intentionally for positive and negative correlation with each other to determine the correlation across one or multiple fields?
Which of the following file contains the traces of the applications installed, run, or uninstalled from a system?
When a user deletes a file or folder, the system stores complete path including the original filename is a special hidden file called “INFO2” in the Recycled folder. If the INFO2 file is deleted, it is recovered when you ______________________.
Bob works as information security analyst for a big finance company. One day, the anomaly-based intrusion detection system alerted that a volumetric DDOS targeting the main IP of the main web server was occurring. What kind of attack is it?
Your company's network just finished going through a SAS 70 audit. This audit reported that overall, your network is secure, but there are some areas that needs improvement. The major area was SNMP security. The audit company recommended turning off SNMP, but that is not an option since you have so many remote nodes to keep track of. What step could you take to help secure SNMP on your network?
To which phase of the Computer Forensics Investigation Process does the Planning and Budgeting of a Forensics Lab belong?
Tyler is setting up a wireless network for his business that he runs out of his home. He has followed all the directions from the ISP as well as the wireless router manual. He does not have any encryption set and the SSID is being broadcast. On his laptop, he can pick up the wireless signal for short periods of time, but then the connection drops and the signal goes away.
Eventually the wireless signal shows back up, but drops intermittently. What could be Tyler issue with his home wireless network?
Which of the following tool enables data acquisition and duplication?
Madison is on trial for allegedly breaking into her university’s internal network. The police raided her dorm room and seized all of her computer equipment. Madison’s lawyer is trying to convince the judge that the seizure was unfounded and baseless. Under which US Amendment is Madison’s lawyer trying to prove the police violated?
Which of the following Registry components include offsets to other cells as well as the LastWrite time for the key?
Smith, a forensic examiner, was analyzing a hard disk image to find and acquire deleted sensitive files. He stumbled upon a $Recycle.Bin folder in the root directory of the disk. Identify the operating system in use.
Data is striped at a byte level across multiple drives, and parity information is distributed among all member drives.
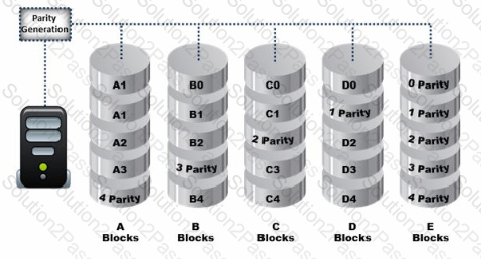
What RAID level is represented here?
Sniffers that place NICs in promiscuous mode work at what layer of the OSI model?
What technique is used by JPEGs for compression?
While looking through the IIS log file of a web server, you find the following entries:

What is evident from this log file?
What type of equipment would a forensics investigator store in a StrongHold bag?
Which of the following tasks DOES NOT come under the investigation phase of a cybercrime forensics investigation case?
Using Internet logging software to investigate a case of malicious use of computers, the investigator comes across some entries that appear odd.
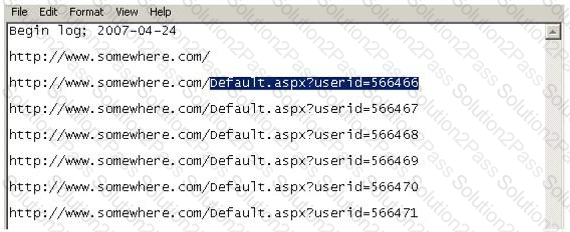
From the log, the investigator can see where the person in question went on the Internet. From the log, it appears that the user was manually typing in different user ID numbers. What technique this user was trying?
What method of copying should always be performed first before carrying out an investigation?
When reviewing web logs, you see an entry for resource not found in the HTTP status code field.
What is the actual error code that you would see in the log for resource not found?
What type of analysis helps to identify the time and sequence of events in an investigation?
Which of the following techniques can be used to beat steganography?
The investigator wants to examine changes made to the system’s registry by the suspect program. Which of the following tool can help the investigator?
