312-49v9 ECCouncil Computer Hacking Forensic Investigator (v9) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ECCouncil 312-49v9 Computer Hacking Forensic Investigator (v9) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Steven has been given the task of designing a computer forensics lab for the company he works for. He has found documentation on all aspects of how to design a lab except the number of exits needed. How many exits should Steven include in his design for the computer forensics lab?
Which of the following acts as a network intrusion detection system as well as network intrusion prevention system?
Given the drive dimensions as follows and assuming a sector has 512 bytes, what is the capacity of the described hard drive?
22,164 cylinders/disk
80 heads/cylinder
63 sectors/track
When marking evidence that has been collected with the aa/ddmmyy/nnnn/zz format, what does the nnn denote?
How will you categorize a cybercrime that took place within a CSP’s cloud environment?
Which of the following Event Correlation Approach checks and compares all the fields systematically and intentionally for positive and negative correlation with each other to determine the correlation across one or multiple fields?
A picture file is recovered from a computer under investigation. During the investigation process, the file is enlarged 500% to get a better view of its contents. The picture quality is not degraded at all from this process. What kind of picture is this file. What kind of picture is this file?
The investigator wants to examine changes made to the system’s registry by the suspect program. Which of the following tool can help the investigator?
Ivanovich, a forensics investigator, is trying to extract complete information about running processes from a system. Where should he look apart from the RAM and virtual memory?
Which network attack is described by the following statement?
“At least five Russian major banks came under a continuous hacker attack, although online client services were not disrupted. The attack came from a wide-scale botnet involving at least 24,000 computers, located in 30 countries.”
In the following directory listing,
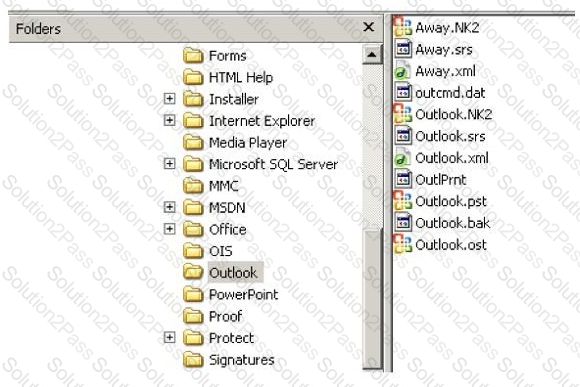
Which file should be used to restore archived email messages for someone using Microsoft Outlook?
What type of analysis helps to identify the time and sequence of events in an investigation?
An investigator is searching through the firewall logs of a company and notices ICMP packets that are larger than 65,536 bytes. What type of activity is the investigator seeing?
Which of the following is a list of recently used programs or opened files?
Under confession, an accused criminal admitted to encrypting child pornography pictures and then hiding them within other pictures. What technique did the accused criminal employ?
NTFS has reduced slack space than FAT, thus having lesser potential to hide data in the slack space. This is because:
When using an iPod and the host computer is running Windows, what file system will be used?
Microsoft Security IDs are available in Windows Registry Editor. The path to locate IDs in Windows 7 is:
Which program is the bootloader when Windows XP starts up?
Julie is a college student majoring in Information Systems and Computer Science. She is currently writing an essay for her computer crimes class. Julie paper focuses on white-collar crimes in America and how forensics investigators investigate the cases. Julie would like to focus the subject. Julie would like to focus the subject of the essay on the most common type of crime found in corporate America. What crime should Julie focus on?
Smith, as a part his forensic investigation assignment, seized a mobile device. He was asked to recover the Subscriber Identity Module (SIM card) data in the mobile device. Smith found that the SIM was protected by a Personal Identification Number (PIN) code, but he was also aware that people generally leave the PIN numbers to the defaults or use easily guessable numbers such as 1234. He made three unsuccessful attempts, which blocked the SIM card. What can Jason do in this scenario to reset the PIN and access SIM data?
What type of attack sends spoofed UDP packets (instead of ping packets) with a fake source address to the IP broadcast address of a large network?
Which forensic investigating concept trails the whole incident from how the attack began to how the victim was affected?
What is one method of bypassing a system BIOS password?
John is working as a computer forensics investigator for a consulting firm in Canada. He is called to seize a computer at a local web caf purportedly used as a botnet server. John thoroughly scans the computer and finds nothing that would lead him to think the computer was a botnet server. John decides to scan the virtual memory of the computer to possibly find something he had missed. What information will the virtual memory scan produce?
Richard is extracting volatile data from a system and uses the command doskey/history. What is he trying to extract?
What is the slave device connected to the secondary IDE controller on a Linux OS referred to?
Casey has acquired data from a hard disk in an open source acquisition format that allows her to generate compressed or uncompressed image files. What format did she use?
What is the smallest physical storage unit on a hard drive?
What stage of the incident handling process involves reporting events?
