312-49v9 ECCouncil Computer Hacking Forensic Investigator (v9) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ECCouncil 312-49v9 Computer Hacking Forensic Investigator (v9) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
During an investigation, an employee was found to have deleted harassing emails that were sent to someone else. The company was using Microsoft Exchange and had message tracking enabled. Where could the investigator search to find the message tracking log file on the Exchange server?
Where are files temporarily written in Unix when printing?
Which of the following tool enables data acquisition and duplication?
A forensics investigator needs to copy data from a computer to some type of removable media so he can examine the information at another location. The problem is that the data is around 42GB in size. What type of removable media could the investigator use?
What feature of Decryption Collection allows an investigator to crack a password as quickly as possible?
Which of the following tool captures and allows you to interactively browse the traffic on a network?
Harold is a computer forensics investigator working for a consulting firm out of Atlanta Georgia. Harold is called upon to help with a corporate espionage case in Miami Florida. Harold assists in the investigation by pulling all the data from the computers allegedly used in the illegal activities. He finds that two suspects in the company where stealing sensitive corporate information and selling it to competing companies. From the email and instant messenger logs recovered, Harold has discovered that the two employees notified the buyers by writing symbols on the back of specific stop signs. This way, the buyers knew when and where to meet with the alleged suspects to buy the stolen material. What type of steganography did these two suspects use?
Jack Smith is a forensics investigator who works for Mason Computer Investigation Services. He is investigating a computer that was infected by Ramen Virus.
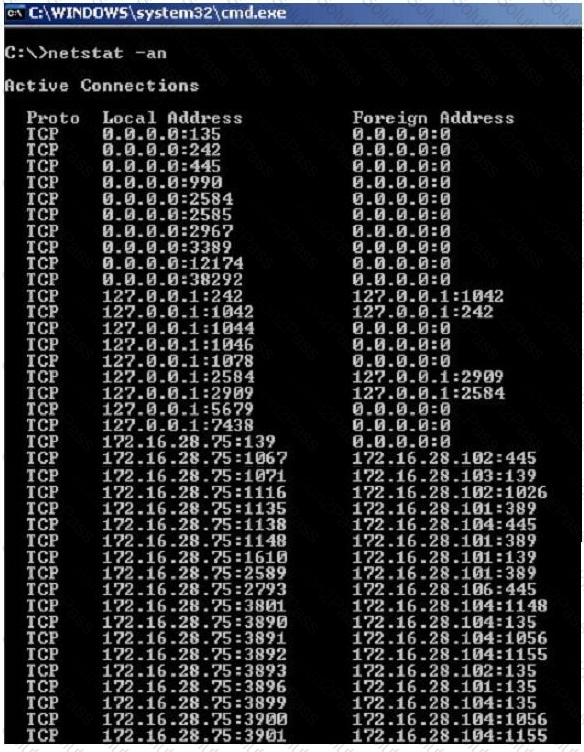
He runs the netstat command on the machine to see its current connections. In the following screenshot, what do the 0.0.0.0 IP addresses signify?
While presenting his case to the court, Simon calls many witnesses to the stand to testify. Simon decides to call Hillary Taft, a lay witness, to the stand. Since Hillary is a lay witness, what field would she be considered an expert in?
Which of the following tool creates a bit-by-bit image of an evidence media?
In Steganalysis, which of the following describes a Known-stego attack?
Billy, a computer forensics expert, has recovered a large number of DBX files during the forensic investigation of a laptop. Which of the following email clients can he use to analyze the DBX files?
A computer forensics investigator is inspecting the firewall logs for a large financial institution that has employees working 24 hours a day, 7 days a week.
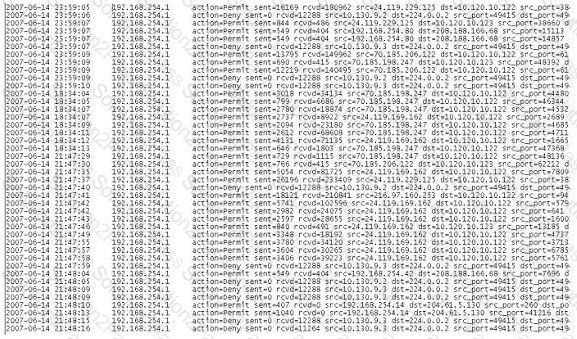
What can the investigator infer from the screenshot seen below?
Before performing a logical or physical search of a drive in Encase, what must be added to the program?
Which password cracking technique uses every possible combination of character sets?
Cylie is investigating a network breach at a state organization in Florida. She discovers that the intruders were able to gain access into the company firewalls by overloading them with IP packets. Cylie then discovers through her investigation that the intruders hacked into the company phone system and used the hard drives on their PBX system to store shared music files. What would this attack on the company PBX system be called?
Which network attack is described by the following statement? "At least five Russian major banks came under a continuous hacker attack, although online client services were not disrupted. The attack came from a wide-scale botnet involving at least 24,000 computers, located in 30 countries."
Paraben Lockdown device uses which operating system to write hard drive data?
When searching through file headers for picture file formats, what should be searched to find a JPEG file in hexadecimal format?
What will the following Linux command accomplish?
dd if=/dev/mem of=/home/sam/mem.bin bs=1024
Davidson Trucking is a small transportation company that has three local offices in Detroit Michigan. Ten female employees that work for the company have gone to an attorney reporting that male employees repeatedly harassed them and that management did nothing to stop the problem. Davidson has employee policies that outline all company guidelines, including awareness on harassment and how it will not be tolerated. When the case is brought to court, whom should the prosecuting attorney call upon for not upholding company policy?
Which of the following files stores information about a local Google Drive installation such as User email ID, Local Sync Root Path, and Client version installed?
All Blackberry email is eventually sent and received through what proprietary RIM-operated mechanism?
Which of the following options will help users to enable or disable the last access time on a system running Windows 10 OS?
Jacky encrypts her documents using a password. It is known that she uses her daughter’s year of birth as part of the password. Which password cracking technique would be optimal to crack her password?
When operating systems mark a cluster as used but not allocated, the cluster is considered as _________
