312-50 ECCouncil Certified Ethical Hacker Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ECCouncil 312-50 Certified Ethical Hacker Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A company is using Windows Server 2003 for its Active Directory (AD). What is the most efficient way to crack the passwords for the AD users?
After gaining access to the password hashes used to protect access to a web based application, knowledge of which cryptographic algorithms would be useful to gain access to the application?
A hacker searches in Google for filetype:pcf to find Cisco VPN config files. Those files may contain connectivity passwords that can be decoded with which of the following?
What statement is true regarding LM hashes?
A hacker is attempting to use nslookup to query Domain Name Service (DNS). The hacker uses the nslookup interactive mode for the search. Which command should the hacker type into the command shell to request the appropriate records?
A hacker is attempting to see which ports have been left open on a network. Which NMAP switch would the hacker use?
Which statement is TRUE regarding network firewalls preventing Web Application attacks?
A large company intends to use Blackberry for corporate mobile phones and a security analyst is assigned to evaluate the possible threats. The analyst will use the Blackjacking attack method to demonstrate how an attacker could circumvent perimeter defenses and gain access to the corporate network. What tool should the analyst use to perform a Blackjacking attack?
In order to show improvement of security over time, what must be developed?
Bluetooth uses which digital modulation technique to exchange information between paired devices?
Which of the following programs is usually targeted at Microsoft Office products?
Which of the following is an application that requires a host application for replication?
Which of the following can the administrator do to verify that a tape backup can be recovered in its entirety?
Which of the following describes the characteristics of a Boot Sector Virus?
Which of the following is a hardware requirement that either an IDS/IPS system or a proxy server must have in order to properly function?
Least privilege is a security concept that requires that a user is
Which of the following is a detective control?
What information should an IT system analysis provide to the risk assessor?
A company has publicly hosted web applications and an internal Intranet protected by a firewall. Which technique will help protect against enumeration?
A Security Engineer at a medium-sized accounting firm has been tasked with discovering how much information can be obtained from the firm's public facing web servers. The engineer decides to start by using netcat to port 80.
The engineer receives this output:
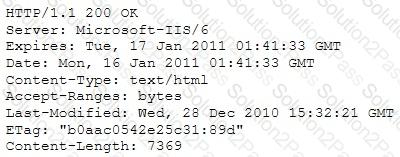
Which of the following is an example of what the engineer performed?
