312-50 ECCouncil Certified Ethical Hacker Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ECCouncil 312-50 Certified Ethical Hacker Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A penetration tester was hired to perform a penetration test for a bank. The tester began searching for IP ranges owned by the bank, performing lookups on the bank's DNS servers, reading news articles online about the bank, watching what times the bank employees come into work and leave from work, searching the bank's job postings (paying special attention to IT related jobs), and visiting the local dumpster for the bank's corporate office. What phase of the penetration test is the tester currently in?
John the Ripper is a technical assessment tool used to test the weakness of which of the following?
A bank stores and processes sensitive privacy information related to home loans. However, auditing has never been enabled on the system. What is the first step that the bank should take before enabling the audit feature?
Passive reconnaissance involves collecting information through which of the following?
A covert channel is a channel that
The following is part of a log file taken from the machine on the network with the IP address of 192.168.1.106:
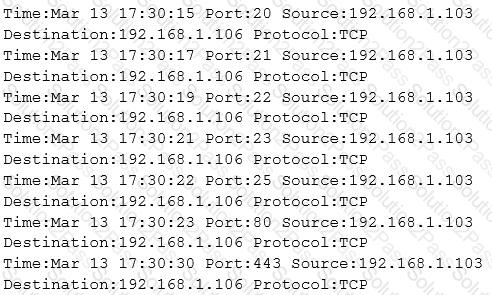
What type of activity has been logged?
Which of the following is a component of a risk assessment?
When utilizing technical assessment methods to assess the security posture of a network, which of the following techniques would be most effective in determining whether end-user security training would be beneficial?
Which of the following lists are valid data-gathering activities associated with a risk assessment?
WPA2 uses AES for wireless data encryption at which of the following encryption levels?
A circuit level gateway works at which of the following layers of the OSI Model?
A security analyst is performing an audit on the network to determine if there are any deviations from the security policies in place. The analyst discovers that a user from the IT department had a dial-out modem installed. Which security policy must the security analyst check to see if dial-out modems are allowed?
When creating a security program, which approach would be used if senior management is supporting and enforcing the security policy?
Which type of antenna is used in wireless communication?
A Network Administrator was recently promoted to Chief Security Officer at a local university. One of employee's new responsibilities is to manage the implementation of an RFID card access system to a new server room on campus. The server room will house student enrollment information that is securely backed up to an off-site location.
During a meeting with an outside consultant, the Chief Security Officer explains that he is concerned that the existing security controls have not been designed properly. Currently, the Network Administrator is responsible for approving and issuing RFID card access to the server room, as well as reviewing the electronic access logs on a weekly basis.
Which of the following is an issue with the situation?
During a penetration test, a tester finds a target that is running MS SQL 2000 with default credentials. The tester assumes that the service is running with Local System account. How can this weakness be exploited to access the system?
What technique is used to perform a Connection Stream Parameter Pollution (CSPP) attack?
The use of alert thresholding in an IDS can reduce the volume of repeated alerts, but introduces which of the following vulnerabilities?
An attacker uses a communication channel within an operating system that is neither designed nor intended to transfer information. What is the name of the communications channel?
During a penetration test, the tester conducts an ACK scan using NMAP against the external interface of the DMZ firewall. NMAP reports that port 80 is unfiltered. Based on this response, which type of packet inspection is the firewall conducting?
