312-50 ECCouncil Certified Ethical Hacker Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ECCouncil 312-50 Certified Ethical Hacker Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which property ensures that a hash function will not produce the same hashed value for two different messages?
The precaution of prohibiting employees from bringing personal computing devices into a facility is what type of security control?
When analyzing the IDS logs, the system administrator noticed an alert was logged when the external router was accessed from the administrator's computer to update the router configuration. What type of an alert is this?
Low humidity in a data center can cause which of the following problems?
Which of the following cryptography attack methods is usually performed without the use of a computer?
One way to defeat a multi-level security solution is to leak data via
What is the main difference between a “Normal” SQL Injection and a “Blind” SQL Injection vulnerability?
A newly discovered flaw in a software application would be considered which kind of security vulnerability?
Which of the following examples best represents a logical or technical control?
What is the most secure way to mitigate the theft of corporate information from a laptop that was left in a hotel room?
Firewalk has just completed the second phase (the scanning phase) and a technician receives the output shown below. What conclusions can be drawn based on these scan results?

A security policy will be more accepted by employees if it is consistent and has the support of
There are several ways to gain insight on how a cryptosystem works with the goal of reverse engineering the process. A term describes when two pieces of data result in the same value is?
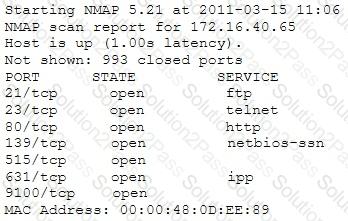
A penetration tester is conducting a port scan on a specific host. The tester found several ports opened that were confusing in concluding the Operating System (OS) version installed. Considering the NMAP result below, which of the following is likely to be installed on the target machine by the OS?
When discussing passwords, what is considered a brute force attack?
You have successfully compromised a machine on the network and found a server that is alive on the same network. You tried to ping it but you didn't get any response back.
What is happening?
An IT employee got a call from one of our best customers. The caller wanted to know about the company's network infrastructure, systems, and team. New opportunities of integration are in sight for both company and customer. What should this employee do?
You want to do an ICMP scan on a remote computer using hping2. What is the proper syntax?
A specific site received 91 ICMP_ECHO packets within 90 minutes from 47 different sites.
77 of the ICMP_ECHO packets had an ICMP ID:39612 and Seq:57072. 13 of the ICMP_ECHO packets had an ICMP ID:0 and Seq:0. What can you infer from this information?
Your company was hired by a small healthcare provider to perform a technical assessment on the network.
What is the best approach for discovering vulnerabilities on a Windows-based computer?
