312-50v13 ECCouncil Certified Ethical Hacker Exam (CEHv13) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ECCouncil 312-50v13 Certified Ethical Hacker Exam (CEHv13) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
During an internal penetration test within a large corporate environment, the red team gains access to an unrestricted network port in a public-facing meeting room. The tester deploys an automated tool that sends thousands of DHCPDISCOVER requests using randomized spoofed MAC addresses. The DHCP server’s lease pool becomes fully depleted, preventing legitimate users from obtaining IP addresses. What type of attack did the penetration tester perform?
What is the common name for a vulnerability disclosure program opened by companies In platforms such as HackerOne?
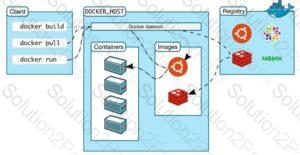
Annie, a cloud security engineer, uses the Docker architecture to employ a client/server model in the application she is working on. She utilizes a component that can process API requests and handle various Docker objects, such as containers, volumes. Images, and networks. What is the component of the Docker architecture used by Annie in the above scenario?
Malware uses Background Intelligent Transfer Service (BITS) to evade detection. Why is BITS attractive to attackers?
During an attempt to perform an SQL injection attack, a certified ethical hacker is focusing on the
identification of database engine type by generating an ODBC error. The ethical hacker, after injecting various payloads, finds that the web application returns a standard, generic error message that does not reveal any detailed database information. Which of the following techniques would the hacker consider next to obtain useful information about the underlying database?
Which of the following is a low-tech way of gaining unauthorized access to systems?
You are analyzing traffic on the network with Wireshark. You want to routinely run a cron job which will run the capture against a specific set of IPs - 192.168.8.0/24. What command would you use?
You suspect a Man-in-the-Middle (MitM) attack inside the network. Which network activity would help confirm this?
Elante company has recently hired James as a penetration tester. He was tasked with performing enumeration on an organization's network. In the process of enumeration, James discovered a service that is accessible to external sources. This service runs directly on port 21.
What is the service enumerated by James in the above scenario?
During a cloud security assessment, it was discovered that a former employee still had access to critical resources months after leaving the organization. Which practice would have most effectively prevented this issue?
Which of these is capable of searching for and locating rogue access points?
An ethical hacker is hired to conduct a comprehensive network scan of a large organization that strongly suspects potential intrusions into their internal systems. The hacker decides to employ a combination of scanning tools to obtain a detailed understanding of the network. Which sequence of actions would provide the most comprehensive information about the network's status?
Which strategy best mitigates session hijacking?
An attacker decided to crack the passwords used by industrial control systems. In this process, he employed a loop strategy to recover these passwords. He used one character at a time to check whether the first character entered is correct; if so, he continued the loop for consecutive characters. If not, he terminated the loop. Furthermore, the attacker checked how much time the device took to finish one complete password authentication process, through which he deduced how many characters entered are correct.
What is the attack technique employed by the attacker to crack the passwords of the industrial control systems?
As a securing consultant, what are some of the things you would recommend to a company to ensure DNS security?
Which of the following tools can be used to perform a zone transfer?
Which algorithm best protects encrypted traffic patterns?
During an IDS audit, you notice numerous alerts triggered by legitimate user activity. What is the most likely cause?
A financial institution's online banking platform is experiencing intermittent downtime caused by a sophisticated DDoS attack that combines SYN floods and HTTP GET floods from a distributed botnet. Standard firewalls and load balancers cannot mitigate the attack without affecting legitimate users. To protect their infrastructure and maintain service availability, which advanced mitigation strategy should the institution implement?
On performing a risk assessment, you need to determine the potential impacts when some of the critical business processes of the company interrupt its service.
What is the name of the process by which you can determine those critical businesses?
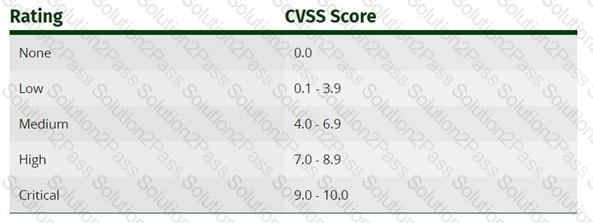
Sam is working as a system administrator In an organization. He captured the principal characteristics of a vulnerability and produced a numerical score to reflect Its severity using CVSS v3.0 to property assess and prioritize the organization's vulnerability management processes. The base score that Sam obtained after performing cvss rating was 4.0. What is the CVSS severity level of the vulnerability discovered by Sam in the above scenario?
Which of the following antennas is commonly used in communications for a frequency band of 10 MHz to VHF and UHF?
While performing a security audit of a web application, an ethical hacker discovers a potential vulnerability.
The application responds to logically incorrect queries with detailed error messages that divulge the underlying database's structure. The ethical hacker decides to exploit this vulnerability further. Which type of SQL Injection attack is the ethical hacker likely to use?
Which of the following DoS tools is used to attack target web applications by starvation of available sessions on the web server? The tool keeps sessions at halt using never-ending POST transmissions and sending an arbitrarily large content-length header value.
These hackers have limited or no training and know how to use only basic techniques or tools. What kind of hackers are we talking about?
Robert, a professional hacker, is attempting to execute a fault injection attack on a target IoT device. In this process, he injects faults into the power supply that can be used for remote execution, also causing the skipping of key instructions. He also injects faults into the clock network used for delivering a synchronized signal across the chip.
Which of the following types of fault injection attack is performed by Robert in the above scenario?
Steve, a scientist who works in a governmental security agency, developed a technological solution to identify people based on walking patterns and implemented this approach to a physical control access.
A camera captures people walking and identifies the individuals using Steve’s approach.
After that, people must approximate their RFID badges. Both the identifications are required to open the door. In this case, we can say:
A red team operator wants to obtain credentials from a Windows machine without touching LSASS memory due to security controls and Credential Guard. They use SSPI to generate NetNTLM responses in the logged-in user context and collect those responses for offline cracking. Which attack technique is being used?
An experienced cyber attacker has created a fake Linkedin profile, successfully impersonating a high-ranking official from a well-established company, to execute a social engineering attack. The attacker then connected with other employees within the organization, receiving invitations to exclusive corporate events and gaining
access to proprietary project details shared within the network. What advanced social engineering technique has the attacker primarily used to exploit the system and what is the most likely immediate threat to the organization?
You are a penetration tester working to test the user awareness of the employees of the client xyz. You harvested two employees' emails from some public sources and are creating a client-side backdoor to send it to the employees via email. Which stage of the cyber kill chain are you at?
As a budding cybersecurity enthusiast, you have set up a small lab at home to learn more about wireless
network security. While experimenting with your home Wi-Fi network, you decide to use a well-known
hacking tool to capture network traffic and attempt to crack the Wi-Fi password. However, despite many
attempts, you have been unsuccessful. Your home Wi-Fi network uses WPA2 Personal with AES encryption.
Why are you finding it difficult to crack the Wi-Fi password?
A large e-commerce organization is planning to implement a vulnerability assessment solution to enhance its security posture. They require a solution that imitates the outside view of attackers, performs well-organized inference-based testing, scans automatically against continuously updated databases, and supports multiple networks. Given these requirements, which type of vulnerability assessment solution would be most appropriate?
A penetration tester discovers that a web application uses unsanitized user input to dynamically generate file paths. The tester identifies that the application is vulnerable to Remote File Inclusion (RFI). Which action should the tester take to exploit this vulnerability?
Which of the following program infects the system boot sector and the executable files at the same time?
Which iOS jailbreaking technique patches the kernel during the device boot so that it becomes jailbroken after each successive reboot?
Mary found a high vulnerability during a vulnerability scan and notified her server team. After analysis, they sent her proof that a fix to that issue had already been applied. The vulnerability that Marry found is called what?
in the Common Vulnerability Scoring System (CVSS) v3.1 severity ratings, what range does medium vulnerability fall in?
A zone file consists of which of the following Resource Records (RRs)?
A city’s power management system relies on SCADA infrastructure. Recent anomalies include inconsistent sensor readings and intermittent outages. Security analysts suspect a side-channel attack designed to extract sensitive information covertly from SCADA devices. Which investigative technique would best confirm this type of attack?
During a security assessment of a cloud-hosted application using SOAP-based web services, a red team operator intercepts a valid SOAP request, duplicates the signed message body, inserts it into the same envelope, and forwards it. Due to improper validation, the server accepts the duplicated body and executes unauthorized code. What type of attack does this represent?