312-50v13 ECCouncil Certified Ethical Hacker Exam (CEHv13) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ECCouncil 312-50v13 Certified Ethical Hacker Exam (CEHv13) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A company’s online service is under a multi-vector DoS attack using SYN floods and HTTP GET floods. Firewalls and IDS cannot stop the outage. What advanced defense should the company implement?
Attackers persisted by modifying legitimate system utilities and services. What key step helps prevent similar threats?
Which social engineering attack involves impersonating a coworker or authority figure to extract confidential information?
You are a cybersecurity analyst at a global banking corporation and suspect a backdoor attack due to abnormal outbound traffic during non-working hours, unexplained reboots, and modified system files. Which combination of measures would be most effective to accurately identify and neutralize the backdoor while ensuring system integrity?
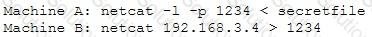
An attacker runs the netcat tool to transfer a secret file between two hosts.
He is worried about information being sniffed on the network.
How would the attacker use netcat to encrypt the information before transmitting onto the wire?
During a high-stakes engagement, a penetration tester abuses MS-EFSRPC to force a domain controller to authenticate to an attacker-controlled server. The tester captures the NTLM hash and relays it to AD CS to obtain a certificate granting domain admin privileges. Which network-level hijacking technique is illustrated?
A company’s policy requires employees to perform file transfers using protocols which encrypt traffic. You suspect some employees are still performing file transfers using unencrypted protocols because the employees do not like changes. You have positioned a network sniffer to capture traffic from the laptops used by employees in the data ingest department. Using Wireshark to examine the captured traffic, which command can be used as display filter to find unencrypted file transfers?
A multinational organization is implementing a security upgrade for its corporate wireless infrastructure. The current WPA2-Personal configuration relies on a shared passphrase, which the IT team finds difficult to rotate and manage securely across hundreds of employee devices. To enhance security and scalability, the organization decides to migrate to WPA2-Enterprise. The new setup must allow for centralized control of user authentication, support certificate-based identity verification, and ensure that each authenticated client is assigned a unique session encryption key to prevent key reuse and limit the blast radius of potential breaches.
Which component is essential for enabling this centralized, certificate-based authentication with unique key generation per session in a WPA2-Enterprise environment?
Abel, a cloud architect, uses container technology to deploy applications/software including all its dependencies, such as libraries and configuration files, binaries, and other resources that run independently from other processes in the cloud environment. For the containerization of applications, he follows the five-tier container technology architecture. Currently. Abel is verifying and validating image contents, signing images, and sending them to the registries. Which of the following tiers of the container technology architecture Is Abel currently working in?
A post-breach forensic investigation revealed that a known vulnerability in Apache Struts was to blame for the Equifax data breach that affected 143 million customers. A fix was available from the software vendor for several months prior 10 the Intrusion. This Is likely a failure in which of the following security processes?
Which scenario best describes a slow, stealthy scanning technique?
The company ABC recently contracts a new accountant. The accountant will be working with the financial statements. Those financial statements need to be approved by the CFO and then they will be sent to the accountant but the CFO is worried because he wants to be sure that the information sent to the accountant was not modified once he approved it. Which of the following options can be useful to ensure the integrity of the data?
A senior executive receives a personalized email titled “Annual Performance Review 2024.” The email includes a malicious PDF that installs a backdoor when opened. The message appears to originate from the CEO and uses official company branding. Which phishing technique does this scenario best illustrate?
You perform a FIN scan and observe that many ports do not respond to FIN packets. How should these results be interpreted?
You need a tool that can do network intrusion prevention and intrusion detection, function as a network sniffer, and record network activity. What tool would you most likely select?
A vulnerability has a score of 9.8. What does this rating help explain?
DHCP snooping is a great solution to prevent rogue DHCP servers on your network. Which security feature on switchers leverages the DHCP snooping database to help prevent man-in-the-middle attacks?
MX record priority increases as the number increases. (True/False.)
Which wireless security protocol replaces the personal pre-shared key (PSK) authentication with Simultaneous Authentication of Equals (SAE) and is therefore resistant to offline dictionary attacks?
Given the complexities of an organization’s network infrastructure, a threat actor has exploited an unidentified vulnerability, leading to a major data breach. As a Certified Ethical Hacker (CEH), you are tasked with enhancing
the organization's security stance. To ensure a comprehensive security defense, you recommend a certain security strategy. Which of the following best represents the strategy you would likely suggest and why?
A tester evaluates a login form that constructs SQL queries using unsanitized user input. By submitting 1 OR 'T'='T'; --, the tester gains unauthorized access to the application. What type of SQL injection has occurred?
Which definition among those given below best describes a covert channel?
While scanning with Nmap, Patin found several hosts which have the IP ID of incremental sequences. He then decided to conduct: nmap -Pn -p- -si kiosk.adobe.com www.riaa.com. kiosk.adobe.com is the host with incremental IP ID sequence. What is the purpose of using "-si" with Nmap?
A penetration tester alters the "file" parameter in a web application (e.g., view?file=report.txt) to ../../../../etc/passwd and successfully accesses restricted system files. What attack method does this scenario illustrate?
During LDAP-based enumeration, you observe that some critical information cannot be retrieved. What is the most likely reason?
John, a security analyst working for an organization, found a critical vulnerability on the organization's LAN that allows him to view financial and personal information about the rest of the employees. Before reporting the vulnerability, he examines the information shown by the vulnerability for two days without disclosing any information to third parties or other internal employees. He does so out of curiosity about the other employees and may take advantage of this information later.
What would John be considered as?
How can you determine if an LM hash you extracted contains a password that is less than 8 characters long?
A penetration tester is hired by a company to assess its vulnerability to social engineering attacks targeting its IT department. The tester decides to use a sophisticated pretext involving technical jargon and insider information to deceive employees into revealing their network credentials. What is the most effective social engineering technique the tester should employ to maximize the chances of obtaining valid credentials without raising suspicion?
Alice needs to send a confidential document to her coworker. Bryan. Their company has public key infrastructure set up. Therefore. Alice both encrypts the message and digitally signs it. Alice uses_______to encrypt the message, and Bryan uses__________to confirm the digital signature.
Multiple failed login attempts using expired tokens are followed by successful access with a valid token. What is the most likely attack scenario?
A web application returns generic error messages. The analyst submits AND 1=1 and AND 1=2 and observes different responses. What type of injection is being tested?
During a covert red team engagement, a penetration tester is tasked with identifying live hosts in a target organization’s internal subnet (10.0.0.0/24) without triggering intrusion detection systems (IDS). To remain undetected, the tester opts to use the command nmap -sn -PE 10.0.0.0/24, which results in several "Host is up" responses, even though the organization’s IDS is tuned to detect high-volume scans. After the engagement, the client reviews the logs and is surprised that the scan was not flagged. What allowed the scan to complete without triggering alerts?
Which best describes the role of a penetration tester?
Which of the following is the primary goal of ethical hacking?
An organization has automated the operation of critical infrastructure from a remote location. For this purpose, all the industrial control systems are connected to the Internet. To empower the manufacturing process, ensure the reliability of industrial networks, and reduce downtime and service disruption, the organization deckled to install an OT security tool that further protects against security incidents such as cyber espionage, zero-day attacks, and malware. Which of the following tools must the organization employ to protect its critical infrastructure?
You have retrieved the raw hash values from a Windows 2000 Domain Controller. Using social engineering, you come to know that they are enforcing strong passwords. Passwords must be at least 8 characters and use 3 of the 4 categories (lowercase, uppercase, numbers, special characters). With your knowledge of likely user habits, what would be the fastest type of password cracking attack to run against these hash values?
John, a professional hacker, targeted an organization that uses LDAP for accessing distributed directory services. He used an automated tool to anonymously query the IDAP service for sensitive information such as usernames. addresses, departmental details, and server names to launch further attacks on the target organization.
What is the tool employed by John to gather information from the IDAP service?
Upon establishing his new startup, Tom hired a cloud service provider (CSP) but was dissatisfied with their service and wanted to move to another CSP.
What part of the contract might prevent him from doing so?
Which of the following is a command line packet analyzer similar to GUI-based Wireshark?
A penetration tester needs to identify open ports and services on a target network without triggering the organization's intrusion detection systems, which are configured to detect high-volume traffic and common scanning techniques. To achieve stealth, the tester decides to use a method that spreads out the scan over an extended period. Which scanning technique should the tester employ to minimize the risk of detection?
