312-50v13 ECCouncil Certified Ethical Hacker Exam (CEHv13) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ECCouncil 312-50v13 Certified Ethical Hacker Exam (CEHv13) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Peter extracts the SIDs list from a Windows 2000 Server machine using the hacking tool "SIDExtractor". Here is the output of the SIDs:

[Image showing multiple user accounts with their Security Identifiers (SIDs)]
From the above list identify the user account with System Administrator privileges.
An LDAP directory can be used to store information similar to a SQL database. LDAP uses a _____ database structure instead of SQL’s _____ structure. Because of this, LDAP has difficulty representing many-to-one relationships.
Multiple internal workstations and IoT devices are compromised and transmitting large volumes of traffic to numerous external targets under botnet control. Which type of denial-of-service attack best describes this situation?
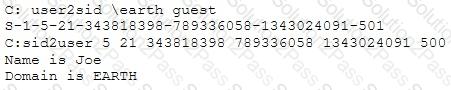
What did the following commands determine?
[Image Output of USER2SID and SID2USER showing that SID ending in -500 corresponds to user Joe on domain EARTH]
When you are getting information about a web server, it is very important to know the HTTP Methods (GET, POST, HEAD, PUT, DELETE, TRACE) that are available because there are two critical methods (PUT and DELETE). PUT can upload a file to the server and DELETE can delete a file from the server. You can detect all these methods (GET, POST, HEAD, DELETE, PUT, TRACE) using NMAP script engine. What Nmap script will help you with this task?
A penetration tester targets a WPA2-PSK wireless network. The tester captures the handshake and wants to speed up cracking the pre-shared key. Which approach is most effective?
A global fintech company receives extortion emails threatening a severe DDoS attack unless ransom is paid. The attacker briefly launches an HTTP flood to demonstrate capability. The attack uses incomplete POST requests that overload application-layer resources, causing performance degradation. The attacker reinforces their demand with a second threat email. What type of DDoS attack is being carried out?
Under what conditions does a secondary name server request a zone transfer from a primary name server?
A BLE attack captured LL_ENC_REQ and LL_ENC_RSP packets but not the LTK. What is the next step?
The collection of potentially actionable, overt, and publicly available information is known as
A penetration tester is testing a web application's product search feature, which takes user input and queries the database. The tester suspects inadequate input sanitization. What is the best approach to confirm the presence of SQL injection?
What is the proper response for a NULL scan if the port is open?
An Android device has an unpatched permission-handling flaw and updated antivirus. What is the most effective undetected exploitation approach?
Which regulation defines security and privacy controls for Federal information systems and organizations?
Which of the following LM hashes represent a password of less than 8 characters? (Choose two.)
jane, an ethical hacker. Is testing a target organization's web server and website to identity security loopholes. In this process, she copied the entire website and its content on a local drive to view the complete profile of the site's directory structure, file structure, external links, images, web pages, and so on. This information helps jane map the website's directories and gain valuable information. What is the attack technique employed by Jane in the above scenario?
Clark, a professional hacker, attempted to perform a Btlejacking attack using an automated tool, Btlejack, and hardware tool, micro:bit. This attack allowed Clark to hijack, read, and export sensitive information shared between connected devices. To perform this attack, Clark executed various btlejack commands. Which of the following commands was used by Clark to hijack the connections?
During a physical penetration test simulating a social engineering attack, a threat actor walks into the lobby of a target organization dressed as a field technician from a known external vendor. Carrying a fake ID badge and referencing a known company name, the attacker confidently claims they’ve been dispatched to perform a routine server room upgrade. Using internal-sounding terminology and referencing real employee names gathered via OSINT, the individual conveys urgency. The receptionist, recognizing the vendor name and the convincing language, allows access without verifying the credentials.
Louis, a professional hacker, had used specialized tools or search engines to encrypt all his browsing activity and navigate anonymously to obtain sensitive/hidden information about official government or federal databases. After gathering the information, he successfully performed an attack on the target government organization without being traced. Which of the following techniques is described in the above scenario?
A DDOS attack is performed at layer 7 to take down web infrastructure. Partial HTTP requests are sent to the web infrastructure or applications. Upon receiving a partial request, the target servers opens multiple connections and keeps waiting for the requests to complete.
Which attack is being described here?
A payload causes a significant delay in response without visible output when testing an Oracle-backed application. What SQL injection technique is being used?
A payload drops a database table by injecting ; DROP TABLE users; --. What SQL injection method was used?
Richard, an attacker, targets an MNC. In this process, he uses a footprinting technique to gather as much information as possible. Using this technique, he gathers domain information such as the target domain name, contact details of its owner, expiry date, and creation date. With this information, he creates a map of the organization's network and misleads domain owners with social engineering to obtain internal details of its network.
What type of footprinting technique is employed by Richard?
As a part of an ethical hacking exercise, an attacker is probing a target network that is suspected to employ various honeypot systems for security. The attacker needs to detect and bypass these honeypots without alerting the target. The attacker decides to utilize a suite of techniques. Which of the following techniques would NOT assist in detecting a honeypot?
joe works as an it administrator in an organization and has recently set up a cloud computing service for the organization. To implement this service, he reached out to a telecom company for providing Internet connectivity and transport services between the organization and the cloud service provider, in the NIST cloud deployment reference architecture, under which category does the telecom company fall in the above scenario?
Study the snort rule given below and interpret the rule:
alert tcp any any --> 192.168.1.0/24 111 (content:"|00 01 86 a5|"; msg: "mountd access";)
A penetration tester is tasked with compromising a company’s wireless network, which uses WPA2-PSK encryption. The tester wants to capture the WPA2 handshake and crack the pre-shared key. What is the most appropriate approach to achieve this?
How can rainbow tables be defeated?
You work for Acme Corporation as Sales Manager. The company has tight network security restrictions. You are trying to steal data from the company's Sales database (Sales.xls) and transfer them to your home computer. Your company filters and monitors traffic that leaves from the internal network to the Internet. How will you achieve this without raising suspicion?
What do Trinoo, TFN2k, WinTrinoo, T-Sight, and Stacheldraht have in common?
A penetration tester is tasked with gathering information about the subdomains of a target organization's website. The tester needs a versatile and efficient solution for the task. Which of the following options would be the most effective method to accomplish this goal?
In ethical hacking, what is black box testing?
A penetration tester is tasked with identifying vulnerabilities on a web server running outdated software. The server hosts several web applications and is protected by a basic firewall. Which technique should the tester use to exploit potential server vulnerabilities?
Which access control mechanism allows for multiple systems to use a central authentication server (CAS) that permits users to authenticate once and gain access to multiple systems?
You are the chief cybersecurity officer at CloudSecure Inc., and your team is responsible for securing a cloudbased application that handles sensitive customer data. To ensure that the data is protected from breaches, you
have decided to implement encryption for both data-at-rest and data-in-transit. The development team suggests using SSL/TLS for securing data in transit. However, you want to also implement a mechanism to detect if the data was tampered with during transmission. Which of the following should you propose?
As a cybersecurity professional, you are responsible for securing a high-traffic web application that uses MySQL as its backend database. Recently, there has been a surge of unauthorized login attempts, and you suspect that a seasoned black-hat hacker is behind them. This hacker has shown proficiency in SQL Injection and
appears to be using the 'UNION' SQL keyword to trick the login process into returning additional data.
However, your application's security measures include filtering special characters in user inputs, a method usually effective against such attacks. In this challenging environment, if the hacker still intends to exploit this SQL Injection vulnerability, which strategy is he most likely to employ?
Which of the following best describes the role of a penetration tester?
Ricardo has discovered the username for an application in his targets environment. As he has a limited amount of time, he decides to attempt to use a list of common passwords he found on the Internet. He compiles them into a list and then feeds that list as an argument into his password-cracking application, what type of attack is Ricardo performing?
A Certified Ethical Hacker (CEH) is given the task to perform an LDAP enumeration on a target system. The system is secured and accepts connections only on secure LDAP. The CEH uses Python for the enumeration process. After successfully installing LDAP and establishing a connection with the target, he attempts to fetch details like the domain name and naming context but is unable to receive the expected response. Considering the circumstances, which of the following is the most plausible reason for this situation?
Which patch management strategy is most effective?
