412-79v10 ECCouncil EC-Council Certified Security Analyst (ECSA) V10 Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ECCouncil 412-79v10 EC-Council Certified Security Analyst (ECSA) V10 certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which of the following statement holds true for TCP Operation?
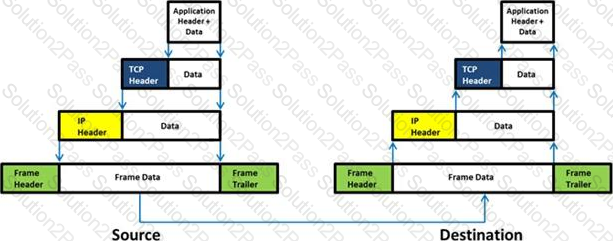
Which of the following has an offset field that specifies the length of the header and data?
Which of the following defines the details of services to be provided for the client’s organization and the list of services required for performing the test in the organization?
The first phase of the penetration testing plan is to develop the scope of the project in consultation with the client. Pen testing test components depend on the client’s operating environment, threat perception, security and compliance requirements, ROE, and budget.
Various components need to be considered for testing while developing the scope of the project.
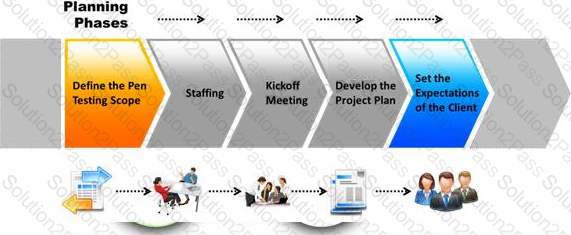
Which of the following is NOT a pen testing component to be tested?
Information gathering is performed to:
i) Collect basic information about the target company and its network
ii) Determine the operating system used, platforms running, web server versions, etc.
iii) Find vulnerabilities and exploits
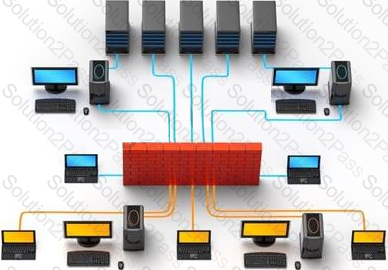
Which of the following pen testing tests yields information about a company’s technology infrastructure?
An antenna is a device that is designed to transmit and receive the electromagnetic waves that are generally called radio waves. Which one of the following types of antenna is developed from waveguide technology?
The SnortMain () function begins by associating a set of handlers for the signals, Snort receives. It does this using the signal () function. Which one of the following functions is used as a programspecific signal and the handler for this calls the DropStats() function to output the current Snort statistics?
What does ICMP Type 3/Code 13 mean?
Traffic on which port is unusual for both the TCP and UDP ports?
Identify the person who will lead the penetration-testing project and be the client point of contact.
Jessica works as systems administrator for a large electronics firm. She wants to scan her network quickly to detect live hosts by using ICMP ECHO Requests. What type of scan is Jessica going to perform?
You are a security analyst performing a penetration tests for a company in the Midwest. After some initial reconnaissance, you discover the IP addresses of some Cisco routers used by the company. You type in the following URL that includes the IP address of one of the routers:
http://172.168.4.131/level/99/exec/show/config
After typing in this URL, you are presented with the entire configuration file for that router. What have you discovered?
Besides the policy implications of chat rooms, Internet Relay Chat (IRC) is frequented by attackers and used as a command and control mechanism. IRC normally uses which one of the following TCP ports?
Which of the following policies helps secure data and protects the privacy of organizational information?
Why is a legal agreement important to have before launching a penetration test?
When setting up a wireless network with multiple access points, why is it important to set each access point on a different channel?
Simon is a former employee of Trinitron XML Inc. He feels he was wrongly terminated and wants to hack into his former company's network. Since Simon remembers some of the server names, he attempts to run the AXFR and IXFR commands using DIG.
What is Simon trying to accomplish here?
You work as an IT security auditor hired by a law firm in Boston to test whether you can gain access to sensitive information about the company clients. You have rummaged through their trash and found very little information.
You do not want to set off any alarms on their network, so you plan on performing passive foot printing against their Web servers. What tool should you use?
Snort, an open source network-based intrusion detection sensor, is the most widely installed NIDS in the world. It can be configured to run in the four modes. Which one of the following modes reads the packets off the network and displays them in a continuous stream on the console (screen)?
Which of the following protocols cannot be used to filter VoIP traffic?
