EC0-350 ECCouncil Ethical Hacking and Countermeasures V8 Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ECCouncil EC0-350 Ethical Hacking and Countermeasures V8 certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Peter is a Network Admin. He is concerned that his network is vulnerable to a smurf attack. What should Peter do to prevent a smurf attack?
Select the best answer.
Which of the following is most effective against passwords?
Select the Answer:
On a backdoored Linux box there is a possibility that legitimate programs are modified or trojaned. How is it possible to list processes and uids associated with them in a more reliable manner?
____________ will let you assume a users identity at a dynamically generated web page or site.
Exhibit:
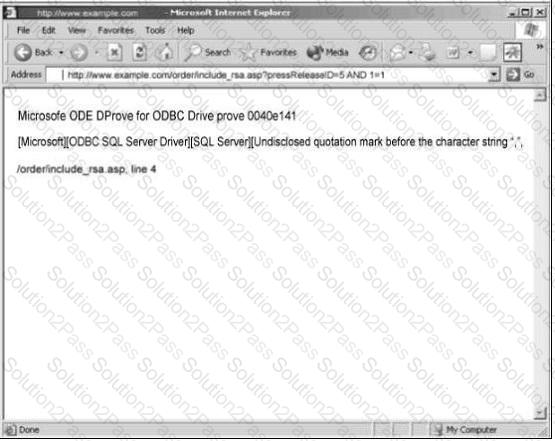
You are conducting pen-test against a company’s website using SQL Injection techniques. You enter “anuthing or 1=1-“ in the username filed of an authentication form. This is the output returned from the server.
What is the next step you should do?
To scan a host downstream from a security gateway, Firewalking:
Which of the following wireless technologies can be detected by NetStumbler? (Select all that apply)
This kind of attack will let you assume a users identity at a dynamically generated web page or site:
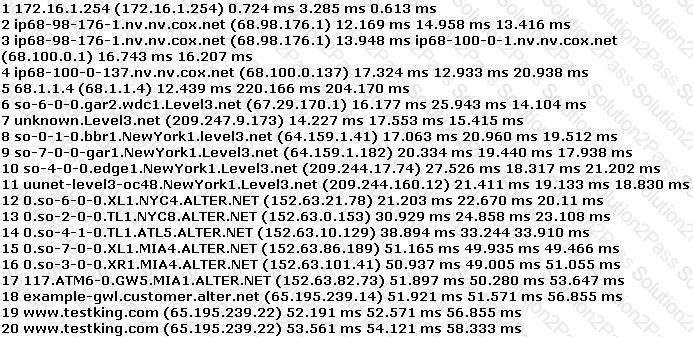
You have performed the traceroute below and notice that hops 19 and 20 both show the same IP address.
What can be inferred from this output?
Windump is the windows port of the famous TCPDump packet sniffer available on a variety of platforms. In order to use this tool on the Windows platform you must install a packet capture library.
What is the name of this library?
Rebecca is a security analyst and knows of a local root exploit that has the ability to enable local users to use available exploits to gain root privileges. This vulnerability exploits a condition in the Linux kernel within the execve() system call. There is no known workaround that exists for this vulnerability. What is the correct action to be taken by Rebecca in this situation as a recommendation to management?
Rebecca has noted multiple entries in her logs about users attempting to connect on ports that are either not opened or ports that are not for public usage. How can she restrict this type of abuse by limiting access to only specific IP addresses that are trusted by using one of the built-in Linux Operating System tools?
What is a sheepdip?
Why do you need to capture five to ten million packets in order to crack WEP with AirSnort?
Neil is closely monitoring his firewall rules and logs on a regular basis. Some of the users have complained to Neil that there are a few employees who are visiting offensive web site during work hours, without any consideration for others. Neil knows that he has an up-to-date content filtering system and such access should not be authorized. What type of technique might be used by these offenders to access the Internet without restriction?
Which of the following best describes session key creation in SSL?
RC4 is known to be a good stream generator. RC4 is used within the WEP standard on wireless LAN. WEP is known to be insecure even if we are using a stream cipher that is known to be secured.
What is the most likely cause behind this?
Peter is a Linux network admin. As a knowledgeable security consultant, he turns to you to look for help on a firewall. He wants to use Linux as his firewall and use the latest freely available version that is offered. What do you recommend?
Select the best answer.
Ron has configured his network to provide strong perimeter security. As part of his network architecture, he has included a host that is fully exposed to attack. The system is on the public side of the demilitarized zone, unprotected by a firewall or filtering router. What would you call such a host?
What is Hunt used for?
There are two types of honeypots- high and low interaction. Which of these describes a low interaction honeypot? Select the best answers.
What is the name of the software tool used to crack a single account on Netware Servers using a dictionary attack?
A Buffer Overflow attack involves:
Bubba has just accessed he preferred ecommerce web site and has spotted an item that he would like to buy. Bubba considers the price a bit too steep. He looks at the source code of the webpage and decides to save the page locally, so that he can modify the page variables. In the context of web application security, what do you think Bubba has changes?
Virus Scrubbers and other malware detection program can only detect items that they are aware of. Which of the following tools would allow you to detect unauthorized changes or modifications of binary files on your system by unknown malware?
Statistics from cert.org and other leading security organizations has clearly showed a steady rise in the number of hacking incidents perpetrated against companies.
What do you think is the main reason behind the significant increase in hacking attempts over the past years?
Look at the following SQL query.
SELECT * FROM product WHERE PCategory='computers' or 1=1--'
What will it return? Select the best answer.
Most NIDS systems operate in layer 2 of the OSI model. These systems feed raw traffic into a detection engine and rely on the pattern matching and/or statistical analysis to determine what is malicious. Packets are not processed by the host's TCP/IP stack allowing the NIDS to analyze traffic the host would otherwise discard. Which of the following tools allows an attacker to intentionally craft packets to confuse pattern-matching NIDS systems, while still being correctly assembled by the host TCP/IP stack to render the attack payload?
John has a proxy server on his network which caches and filters web access. He shuts down all unnecessary ports and services. Additionally, he has installed a firewall (Cisco PIX) that will not allow users to connect to any outbound ports. Jack, a network user has successfully connected to a remote server on port 80 using netcat. He could in turn drop a shell from the remote machine. Assuming an attacker wants to penetrate John's network, which of the following options is he likely to choose?
Ivan is auditing a corporate website. Using Winhex, he alters a cookie as shown below.
Before Alteration: Cookie: lang=en-us; ADMIN=no; y=1 ; time=10:30GMT ;
After Alteration: Cookie: lang=en-us; ADMIN=yes; y=1 ; time=12:30GMT ;
What attack is being depicted here?
Bob is a very security conscious computer user. He plans to test a site that is known to have malicious applets, code, and more. Bob always make use of a basic Web Browser to perform such testing.
Which of the following web browser can adequately fill this purpose?
What is GINA?
Fingerprinting an Operating System helps a cracker because:
Which of the following LM hashes represent a password of less than 8 characters? (Select 2)
Which DNS resource record can indicate how long any "DNS poisoning" could last?
Which of the following is the primary objective of a rootkit?
Exhibit:

The following is an entry captured by a network IDS.You are assigned the task of analyzing this entry. You notice the value 0x90, which is the most common NOOP instruction for the Intel processor. You figure that the attacker is attempting a buffer overflow attack. You also notice "/bin/sh" in the ASCII part of the output. As an analyst what would you conclude about the attack?
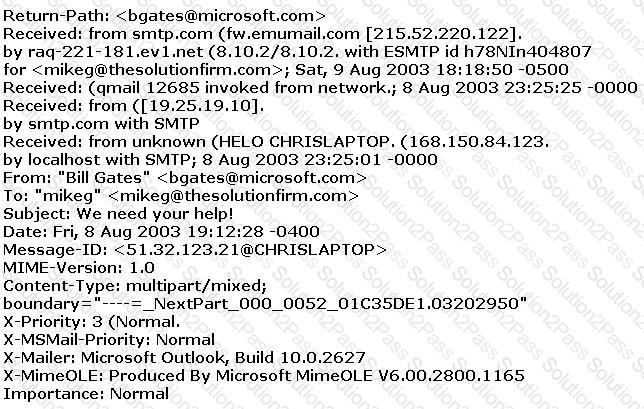
The follows is an email header. What address is that of the true originator of the message?
Which of the following display filters will you enable in Ethereal to view the three-way handshake for a connection from host 192.168.0.1?
What file system vulnerability does the following command take advantage of?
type c:\anyfile.exe > c:\winnt\system32\calc.exe:anyfile.exe
