EC0-350 ECCouncil Ethical Hacking and Countermeasures V8 Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ECCouncil EC0-350 Ethical Hacking and Countermeasures V8 certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
You are a Administrator of Windows server. You want to find the port number for POP3. What file would you find the information in and where?
Select the best answer.
Which of the following tools are used for enumeration? (Choose three.)
When Jason moves a file via NFS over the company's network, you want to grab a copy of it by sniffing. Which of the following tool accomplishes this?
Sniffing is considered an active attack.
Exhibit:
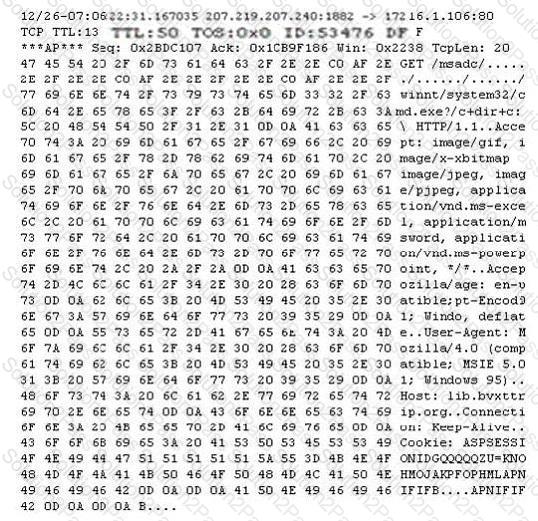
Study the following log extract and identify the attack.
Ethereal works best on ____________.
An attacker runs netcat tool to transfer a secret file between two hosts.
Machine A: netcat -l -p 1234 < secretfile
Machine B: netcat 192.168.3.4 > 1234
He is worried about information being sniffed on the network. How would the attacker use netcat to encrypt the information before transmitting onto the wire?
Which of the following represents the initial two commands that an IRC client sends to join an IRC network?
Study the snort rule given below:
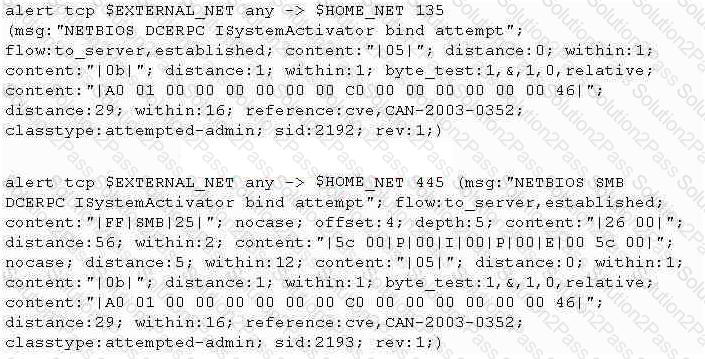
From the options below, choose the exploit against which this rule applies.
What do Trinoo, TFN2k, WinTrinoo, T-Sight, and Stracheldraht have in common?
Which of the following is not considered to be a part of active sniffing?
In the following example, which of these is the "exploit"?
Today, Microsoft Corporation released a security notice. It detailed how a person could bring down the Windows 2003 Server operating system, by sending malformed packets to it. They detailed how this malicious process had been automated using basic scripting. Even worse, the new automated method for bringing down the server has already been used to perform denial of service attacks on many large commercial websites.
Select the best answer.
E-mail scams and mail fraud are regulated by which of the following?
In the context of password security, a simple dictionary attack involves loading a dictionary file (a text file full of dictionary words) into a cracking application such as L0phtCrack or John the Ripper, and running it against user accounts located by the application. The larger the word and word fragment selection, the more effective the dictionary attack is. The brute force method is the most inclusive, although slow. It usually tries every possible letter and number combination in its automated exploration.
If you would use both brute force and dictionary methods combined together to have variation of words, what would you call such an attack?
Null sessions are un-authenticated connections (not using a username or password.) to an NT or 2000 system. Which TCP and UDP ports must you filter to check null sessions on your network?
A network admin contacts you. He is concerned that ARP spoofing or poisoning might occur on his network. What are some things he can do to prevent it?
Select the best answers.
Which type of attack is port scanning?
Exhibit:
ettercap –NCLzs --quiet
What does the command in the exhibit do in “Ettercap”?
ARP poisoning is achieved in _____ steps
What tool can crack Windows SMB passwords simply by listening to network traffic?
Select the best answer.
Exhibit:
Based on the following extract from the log of a compromised machine, what is the hacker really trying to steal?
Which of the following statements about a zone transfer correct?(Choose three.
Which tool/utility can help you extract the application layer data from each TCP connection from a log file into separate files?

