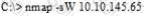ECSAv10 ECCouncil EC-Council Certified Security Analyst (ECSA) v10 : Penetration Testing Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ECCouncil ECSAv10 EC-Council Certified Security Analyst (ECSA) v10 : Penetration Testing certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
NO: 72
You work as an IT security auditor hired by a law firm in Boston to test whether you can gain access to sensitive information about the company clients. You have rummaged through their trash and found very little information.
You do not want to set off any alarms on their network, so you plan on performing passive foot printing against their Web servers. What tool should you use?
In the TCP/IP model, the transport layer is responsible for reliability and flow control from source to the destination. TCP provides the mechanism for flow control by allowing the sending and receiving hosts to communicate.
A flow control mechanism avoids the problem with a transmitting host overflowing the buffers in the receiving host.
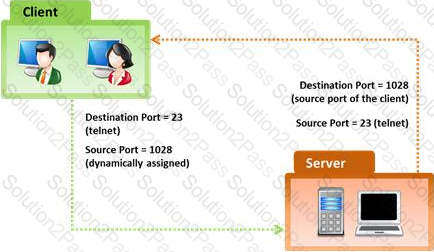
Which of the following statement holds true for TCP Operation?
Which one of the following is a useful formatting token that takes an int * as an argument, and writes the number of bytes already written, to that location?
You setup SNMP in multiple offices of your company. Your SNMP software manager is not receiving data from other offices like it is for your main office. You suspect that firewall changes are to blame.
What ports should you open for SNMP to work through Firewalls.
(Select 2)
Tyler is setting up a wireless network for his business that he runs out of his home. He has followed all the directions from the ISP as well as the wireless router manual. He does not have any encryption set and the SSID is being broadcast.
On his laptop, he can pick up the wireless signal for short periods of time, but then the connection drops and the signal goes away. Eventually the wireless signal shows back up, but drops intermittently.
What could be Tyler issue with his home wireless network?
Harold wants to set up a firewall on his network but is not sure which one would be the most appropriate. He knows he needs to allow FTP traffic to one of the servers on his network, but he wants to only allow FTP-PUT.
Which firewall would be most appropriate for Harold?
Which of the following has an offset field that specifies the length of the header and data?
Logs are the record of the system and network activities. Syslog protocol is used for delivering log information across an IP network. Syslog messages can be sent via which one of the following?
Wireshark is a network analyzer. It reads packets from the network, decodes them, and presents them in an easy-to-understand format. Which one of the following is the command-line version of Wireshark, which can be used to capture the live packets from the wire or to read the saved capture files?
Which of the following approaches to vulnerability assessment relies on the administrator providing baseline of system configuration and then scanning continuously without incorporating any information found at the time of scanning?

The term social engineering is used to describe the various tricks used to fool people (employees, business partners, or customers) into voluntarily giving away information that would not normally be known to the general public.

What is the criminal practice of social engineering where an attacker uses the telephone system in an attempt to scam the user into surrendering private information?
What is the following command trying to accomplish?
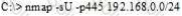
Which of the following is not the SQL injection attack character?
Internet Control Message Protocol (ICMP) messages occur in many situations, such as whenever a datagram cannot reach the destination or the gateway does not have the buffering capacity to forward a datagram. Each ICMP message contains three fields: type, code, and checksum.
Different types of Internet Control Message Protocols (ICMPs) are identified by a type and code field.

Which of the following ICMP messages will be generated if the destination port is not reachable?
Which one of the following log analysis tools is used for analyzing the server’s log files?
By default, the TFTP server listens on UDP port 69. Which of the following utility reports the port status of target TCP and UDP ports on a local or a remote computer and is used to troubleshoot TCP/IP connectivity issues?
Identify the correct formula for Return on Investment (ROI).
Traffic on which port is unusual for both the TCP and UDP ports?
What operating system would respond to the following command?