101 F5 Application Delivery Fundamentals Free Practice Exam Questions (2026 Updated)
Prepare effectively for your F5 101 Application Delivery Fundamentals certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A certificate chain can be used for which purpose?
A client is transmitting a large amount of data to a server During this process, the server sets the window size to zero What is the likely cause of this issue?
ARP provides translation between which two address types?
Which OSI layer provides reliable transmission of frames between adjacent nodes and is built on top of the provides reliable transmission of frames adjacent nodes and is built on top of the Physical layer?
A BIG IP Administrator reviews the Virtual Server configuration and sees the object status represented by a blue square tor an unknown status.How should the administrator change the unknown status?
An administrator is designing a remote host connection using an ICMP based network troubleshooting utility and receive an ICMP error diagram with the following error code.
11. Times exceeded
What does this mean?
Which TransportLayer Security (TLS) extension can be used to enable a single virtual server to serve multiple HTTPS websites in different can be used to enable a single virtual server to server domains?
A BIG-IP Administrator needs to upgrade an HA pair to a more recent TMOS version. The administrator is unsure if the BlG-IP is currently supported How should the administrator verity that the HA pair is under a valid support contract?
A BIG-P Administrator needs to upload a qkview view to evaluate software upgrade options.
Which service should be used?
A BIG-IP Administrator needs a solution to tunnel traffic and transmit encrypted connections over the Internet using only a standard browser and common ports and protocols. Which solution should the administrator select?
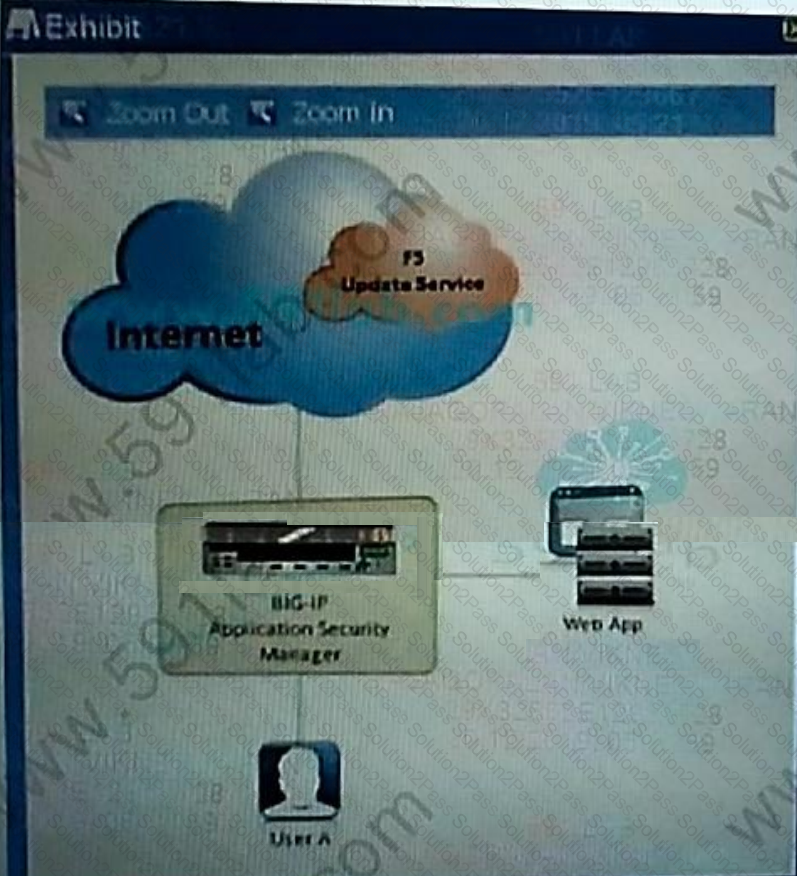
BIG-IP ASM is requesting automatic signature updates from the F5 update service
Who is considered the server in this communication?
An administrator deploys a site in which the load balancer only sees the ingress traffic from the client All egress traffic from the server bypasses the load balancer.
Which type of solution is this?
An administrator needs to connect a new device to a switched network. The interconnect must be both redundant and combined bandwidth than a single link Which low-level protocol will help facilitate this?
What is the primary function of a certificate authority?
A BIG IP virtual Server with an IP address of 10.100.43.108 must be available to public internet users. Which technology should be used to achieve this task?
Which protocol could be used to provide AAA Accounting?
A BIG-IP Administrator is trying to send traffic to a server on the same subnet and sees an incomplete in the BIG-IP devices ARP table. What could cause the incomplete status?
An administrator configures a default gateway for the host. What is the purpose of a default gateway?
What is used to establish trust relationships between BIG-IP devices?
Which two protocol are used for the retrieval of email? (Choose two)
