303 F5 BIG-IP ASM Specialist Free Practice Exam Questions (2026 Updated)
Prepare effectively for your F5 303 BIG-IP ASM Specialist certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
On the VCMP system, a BIG-IP host administrator imports a new ISO image into the host's /shared/images folder. The new ISO images that reside on the vCMP host are available for installation on the guest. How should the BIG-IP Administrator install one image from within the guest?
A BIGJP Administrator needs to load a UCS file but must exclude the license file. How should the administrator perform this task?
An LTMSpecialist must reconfigure a BIG-IP LTM system that load balances traffic to web application servers. The application developer inform the LTM Specialist that TLS must be used to communicate
with the application servers.
Which additional profile isrequired as part of virtual server configuration?
One of the two members of a device group has been decommissioned. The BIG-IP Administrator tries to
delete the device group, but is unsuccessful.
Prior to removing the device group, which action should be performed?
Refer to the exhibit.
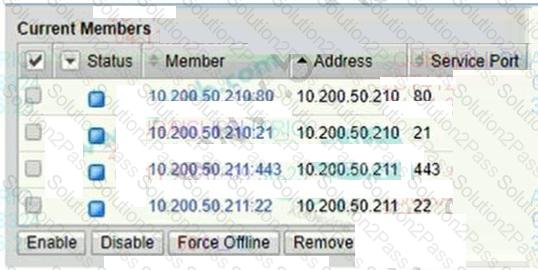
A BIG-IP Administrator needs to configure health monitors for a newly configured server pool named
Pool_B.
Which health monitor settings will ensure that all pool members will be accurately marked as available
or unavailable?
What does the following iRule do?
when CLIENT_ACCEPTED {
if { [matchclass [IP::client_addr] equals WebClient1-Whitelist1] }{
#log local0. "Valid client IP: [IP::client_addr] - forwarding traffic"
#Pool WebClient1
} else {
log local0. "Invalid client IP: [IP::client_addr] - discarding"
discard
}
}
Some users who connect to a busy Virtual Server have connections reset by the BIG-IP system. Pool member resources are NOT a factor in this behavior. What is a possible cause for this behavior?
Refer to the exhibit.
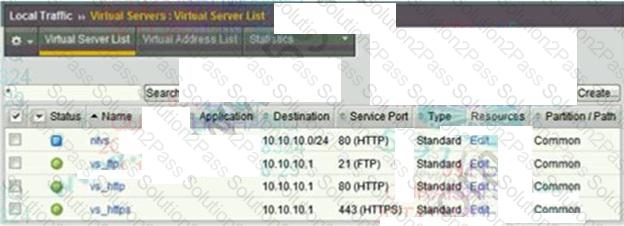
How many nodes are represented on the network map shown?
An LTM is configure an application that isseparated into several subdomains across multiple virtual servers. Many of these subdomains require encryption and could be accessed by anyone on the internet. The configuration must NOT result in SSL warnings to end users.
How should the LTM Specialist configure the SSL profiles for these virtual servers?
-- Exhibit –
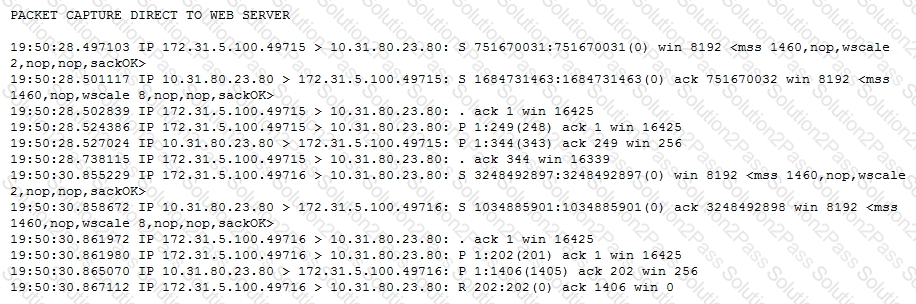
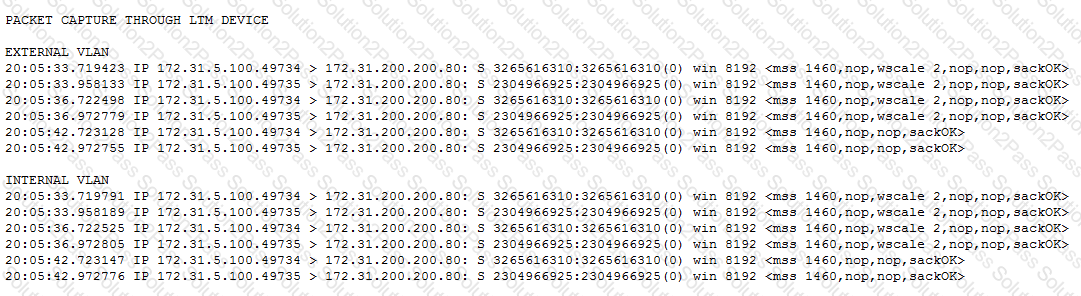
-- Exhibit --
Refer to the exhibits.
Users are able to access the application when connecting directly to the web server but are unsuccessful when connecting to the virtual server. Return traffic bypasses the LTM device using Layer 2 nPath routing.
Which configuration change resolves this problem?
-- Exhibit –
-- Exhibit --
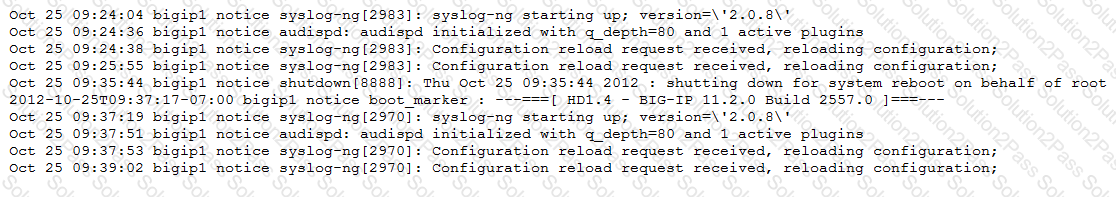
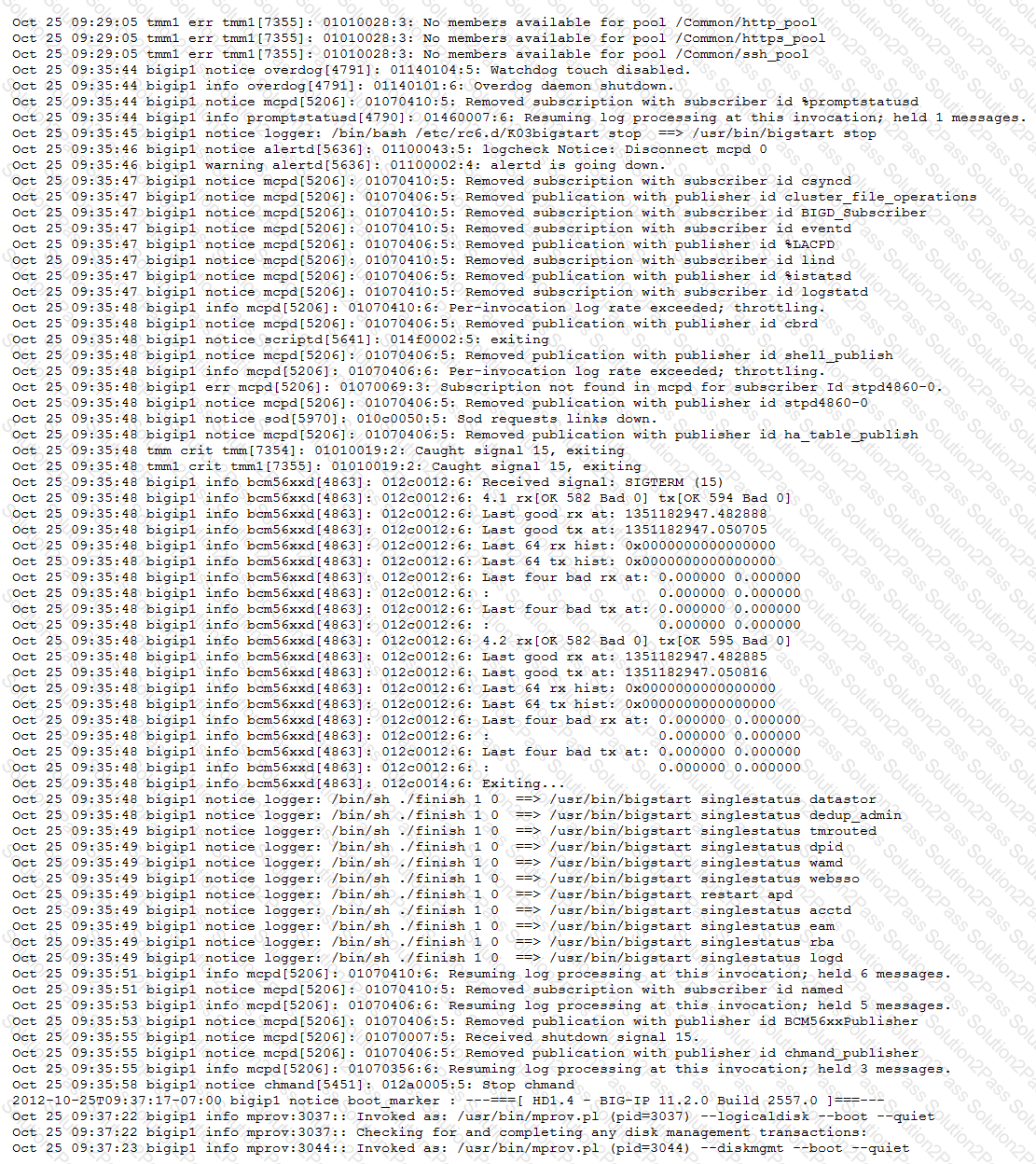
Refer to the exhibits.
An LTM Specialist uses the information in the logs to determine the cause of a failover event in a high-availability (HA) pair.
What caused the failover?
A BIG-IP Administrator runs the initial configuration wizard and learns that the NTP servers were invalid. In which area of the Configuration Utility should the BIG-IP Administrator update the list of configured NTP servers?
An LTM device has a virtual server mapped to www.f5.com with a pool assigned. Users report that when browsing, they are periodically required to re-login to /resources/201.1.7.b.2_l.com. The objects are defined as follows:
Virtual server. Destination 192.168.245.100:443 netmask 255.255.255.0
Persistence: SSL session persistence
Profiles: HTTP/TCP
Which persistence method should the BIG-IP Administrator apply to resolve this issue?
Refer to the exhibit

A connection is being established to IP 1.1.1.1 on port 8080.
Which virtual server will handle the connection?
A BIG-IP Administrator needs to check the memory utilization on a BIG-IP system. Which two methods can the UIG IP Administrator use? (Choose two.)
A BIG IP device delivers the online shopping website https://shop.example.com. Two pool members handle the traffic. An iRule directs requests with the hip parameter "environment=development" to a third pool member for a staging environment.
Which combination of profiles is needed at minimum?
The BIG-IP Administrator needs to perform a BIG-IP device upgrade to the latest version of TMOS. Where can the administrator obtain F5 documentation on upgrade requirements?
An application is configured on an LTM device:
Virtual server: 10.0.0.1:80 (VLAN vlan301)
SNAT IP: 10.0.0.1
Pool members: 10.0.1.1:8080, 10.0.1.2:8080, 10.0.1.3:8080 (VLAN vlan302)
Which packet capture should the LTM Specialist perform on the LTM device command line interface to capture only client traffic specifically for this virtual server?
A virtual server with SNAT automap enabled selects pool member 10.20.0.10.443 for the server-side flow. The client side flow source IP is 192.168.0.10 .

Which source IP should be expected inthe server-side connection?
Which three HTTP headers allow an application server to determine the client's language compatibility, browser, operating system type, and compression compatibility? (Choose three.)
An LTM Specialist is tasked with ensuring that the syslogs for the LTM device are sent to a remote syslog server.
The following is an extract from the config file detailing the node and monitor that the LTM device is using for the
remote syslog server:
monitor
Syslog_15002 {
defaults from udp
dest *:15002
}
node 91.223.45.231 {
monitor Syslog_15002
screen RemoteSYSLOG
}
There seem to be problems communicating with the remote syslog server. However, the pool monitor shows that the remote server is up.
The network department has confirmed that there are no firewall rules or networking issues preventing the LTM device from
communicating with the syslog server. The department responsible for the remote syslog server indicates that there may
be problems with the syslog server. The LTM Specialist checks the BIG-IP LTM logs for errors relating to the remote syslog
server. None are found. The LTM Specialist does a tcpdump:
tcpdump -nn port 15002, with the following results:
21:28:36.395543 IP 192.168.100.100.44772 > 91.223.45.231.15002: UDP, length 19
21:28:36.429073 IP 192.168.100.100.39499 > 91.223.45.231.15002: UDP, length 169
21:28:36.430714 IP 192.168.100.100.39499 > 91.223.45.231.15002: UDP, length 181
21:28:36.840524 IP 192.168.100.100.39499 > 91.223.45.231.15002: UDP, length 169
21:28:36.846547 IP 192.168.100.100.39499 > 91.223.45.231.15002: UDP, length 181
21:28:39.886343 IP 192.168.100.100.39499 > 91.223.45.231.15002: UDP, length 144
NotE. 192.168.100.100 is the self IP of the LTM device.
Why are there no errors for the remote syslog server in the log files?
-- Exhibit –
-- Exhibit --
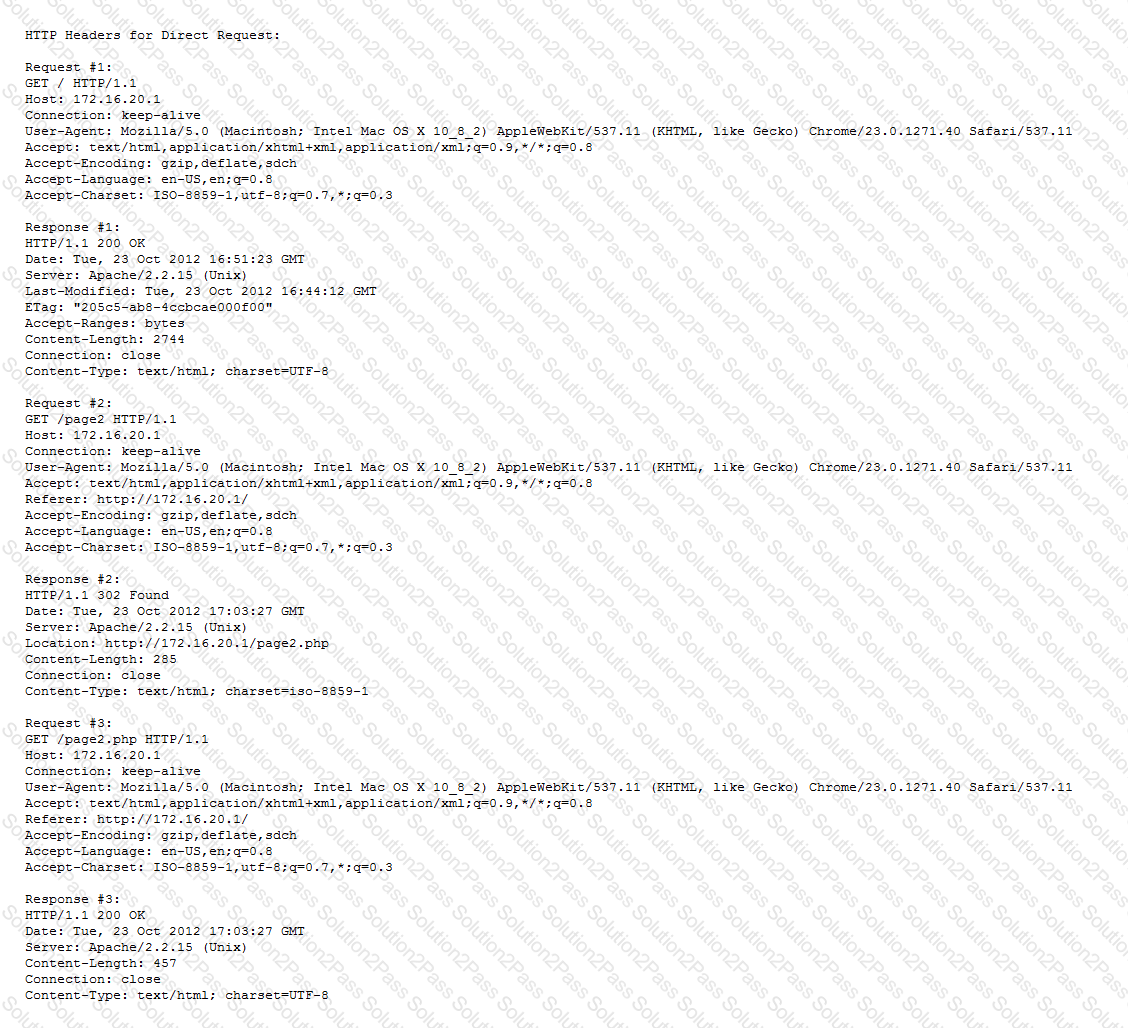
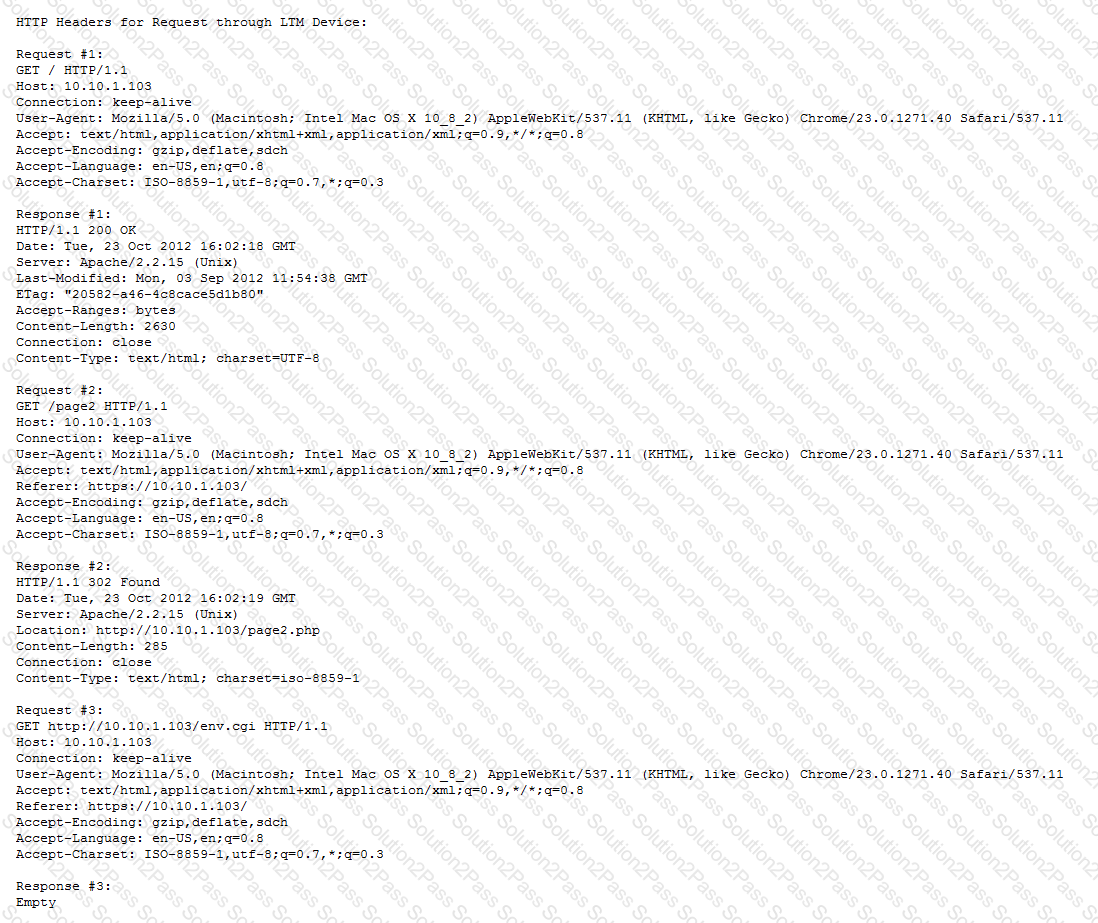
Refer to the exhibits.
A customer requests to offload SSL for an internal website. The front page of the website loads correctly; however, selecting links on the page fails.
How should the LTM Specialist fix the issue?
Where does a LTM Specialist view all of the objects that are part of a deployed iApp?
-- Exhibit –
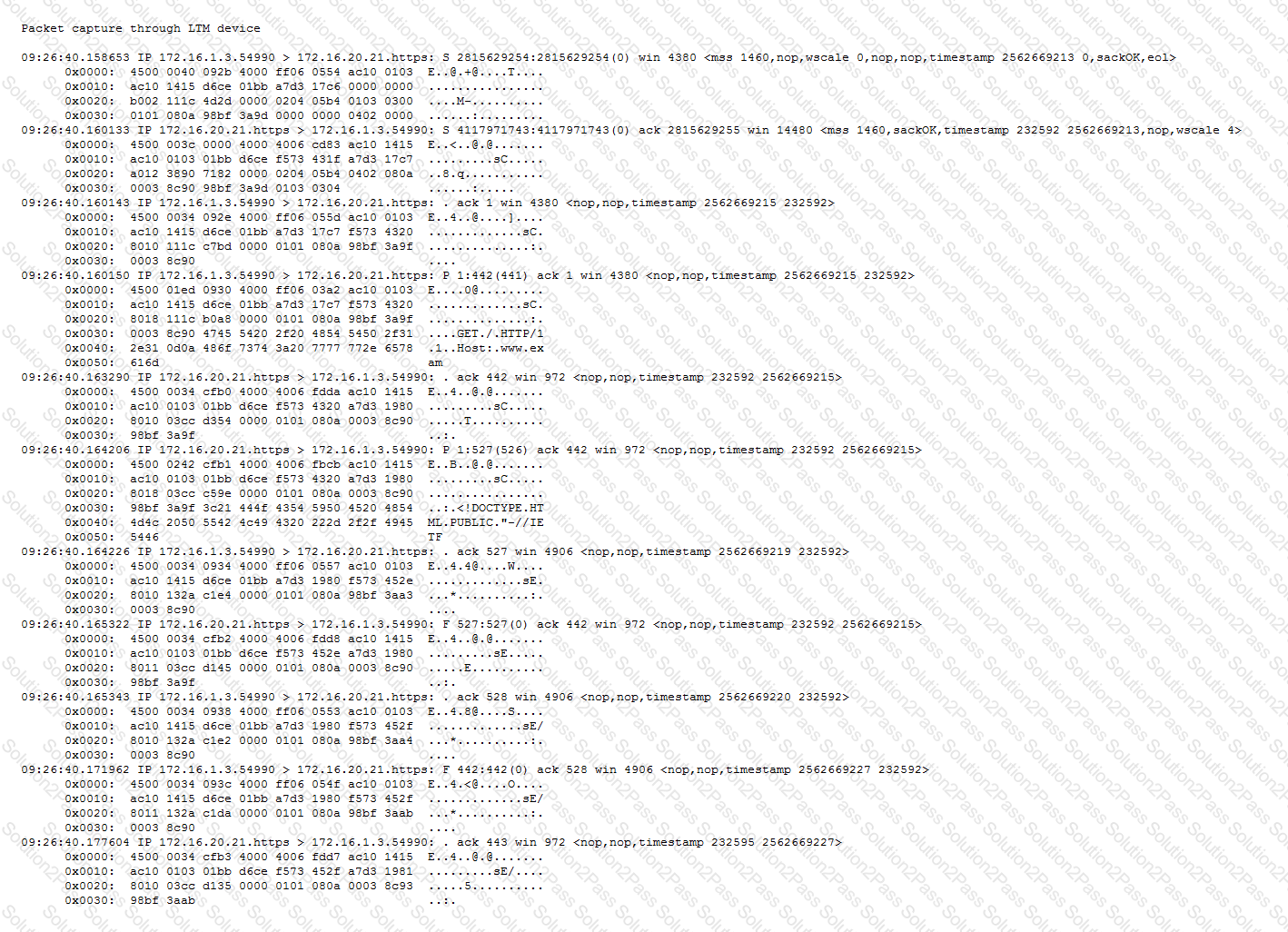
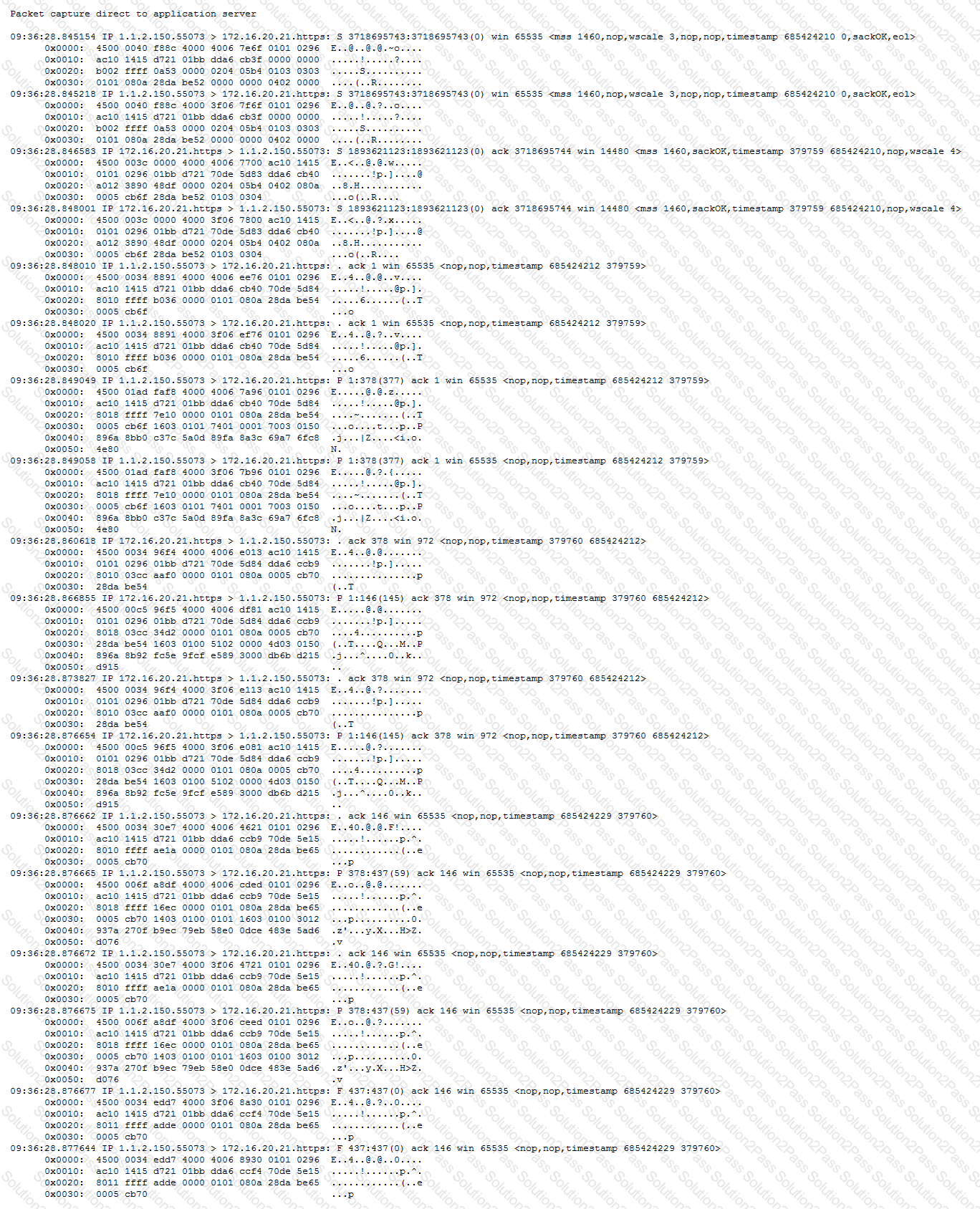
-- Exhibit --
Refer to the exhibits.
An LTM Specialist has configured a virtual server to distribute connections to a pool of application servers and to offload SSL processing. The application fails to work as expected when connecting to the virtual server. It does work when clients connect directly to the application. Two packet captures were taken at the application server.
What is the root cause of the problem?
A web developer has created a custom HTTP call to a backend application. The HTTP headers being sent by the HTTP call are:
GET / HTTP/1.1
User-Agent: MyCustomApp (v1.0)
Accept: text/html
Cache-Control: no-cache
Connection: keep-alive
CookiE. somecookie=1
The backend server is responding with the following:
HTTP/1.1 400 Bad Request
DatE. Wed, 20 Jul 2012 17:22:41 GMT
Connection: close
Why is the HTTP web server responding with a HTTP 400 Bad Request?
-- Exhibit –
-- Exhibit --
Refer to the exhibit.
Which step should an LTM Specialist take to utilize AVR?
A virtual server is configured to handle https traffic. The clientssl profile is configured to use a2048-bit RSA key. Due to security requirements, is the LTM Specialist needs to use a 4096-bit RSA key in the future.
What two effects will this change have on the BIG-IP device? (Choose two)
An LTM device has a virtual server configured as a Performance Layer 4 virtual listening on 0.0.0.0:0 to perform routing of packets to an upstream router. The client machine at IP address 192.168.0.4 is attempting to contact a host upstream of the LTM device on IP address 10.0.0.99.
The network flow is asymmetrical, and the following TCP capture displays:
# tcpdump -nnni 0.0 'host 192.168.0.4 and host 10.0.0.99'
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on 0.0, link-type EN10MB (Ethernet), capture size 96 bytes
05:07:55.499954 IP 192.168.0.4.35345 > 10.0.0.99.443: S 3205656213:3205656213(0) ack 3267995082 win 1480
05:07:55.499983 IP 10.0.0.99.443 > 192.168.0.4.35345: R 1:1(0) ack 1 win 0
05:07:56.499960 IP 192.168.0.4.35345 > 10.0.0.99.443: S 3205656213:3205656213(0) ack 3267995082 win 1480
05:07:56.499990 IP 10.0.0.99.443 > 192.168.0.4.35345: R 1:1(0) ack 1 win 0
4 packets captured
Which option within the fastL4 profile needs to be enabled by the LTM Specialist to prevent the LTM device from rejecting the flow?
An LTM HTTP pool has an associated monitor that sends a string equal to 'GET /test.html'.
Which two configurations could an LTM Specialist implement to allow server administrators to disable their pool member servers without logging into the LTM device? (Choose two.)
A BIG-IP Administrator needs to configure the BIG-IP system to perform load balancing for FTP servers
running passive mode FTP.
How should the administrator configure the Virtual Server to perform this load balancing?
