FCP_FGT_AD-7.4 Fortinet FCP - FortiGate 7.4 Administrator Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Fortinet FCP_FGT_AD-7.4 FCP - FortiGate 7.4 Administrator certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A network administrator enabled antivirus and selected an SSL inspection profile on a firewall policy.
When downloading an EICAR test file through HTTP, FortiGate detects the virus and blocks the file. When downloading the same file through HTTPS, FortiGate does not detect the
and does not block the file allowing it to be downloaded.
The administrator confirms that the traffic matches the configured firewall policy.
What are two reasons for the failed virus detection by FortiGate? (Choose two.)
Which method allows management access to the FortiGate CLI without network connectivity?
Which three methods are used by the collector agent for AD polling? (Choose three.)
Refer to the exhibit.
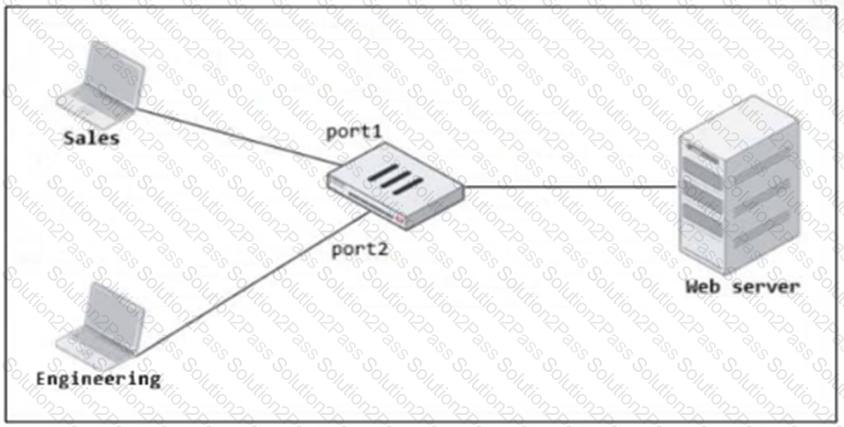
FortiGate has two separate firewall policies for Sales and Engineering to access the same web server with the same security profiles.
Which action must the administrator perform to consolidate the two policies into one?
Refer to the exhibits, which show a diagram of a FortiGate device connected to the network. VIP object configuration, and the firewall policy configuration.
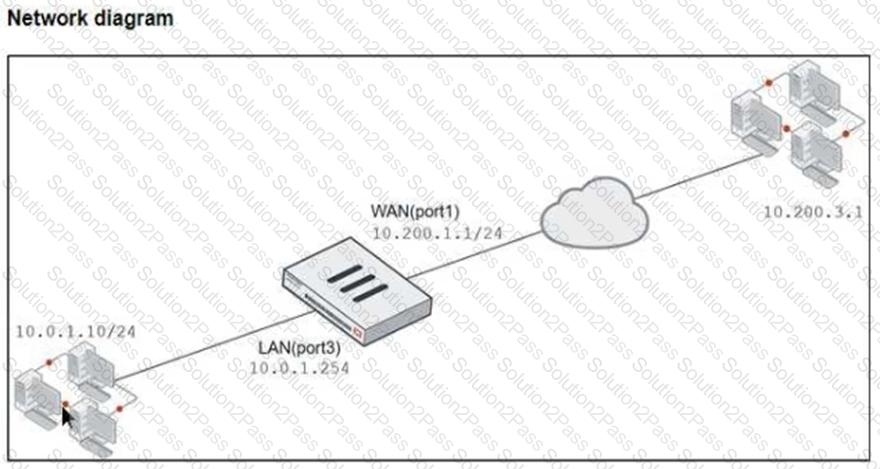
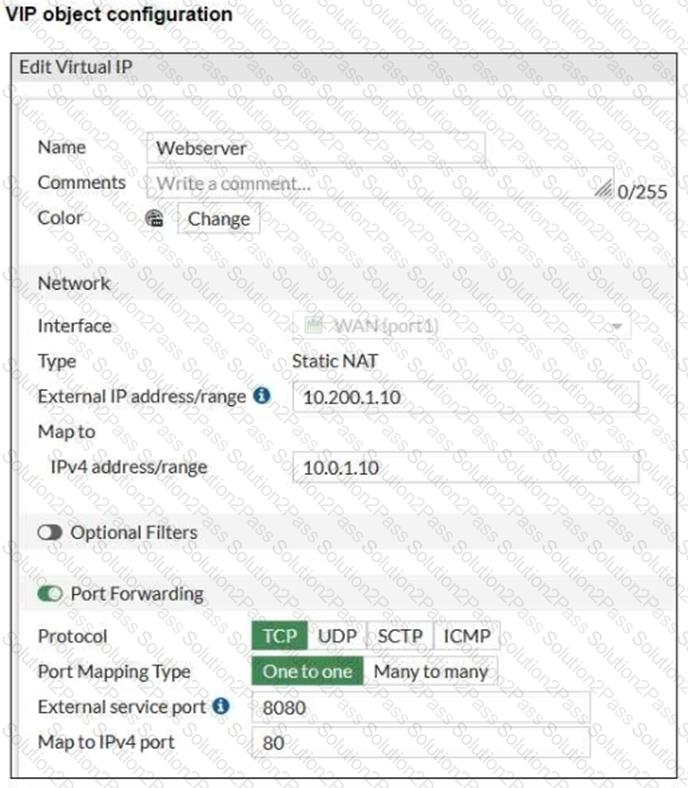

TheWAN (port1)interface has the IP address10.200.1.1/24. TheLAN (port3)interface has the IP address10.0.1.254/24.
If the host10.200.3.1sends a TCP SYN packet on port 8080 to10.200.1.10, what will the source address, destination address, and destination port of the packet be at the time FortiGate forwards the packet to the destination?
Refer to the exhibit, which shows an SD-WAN zone configuration on the FortiGate GUI.
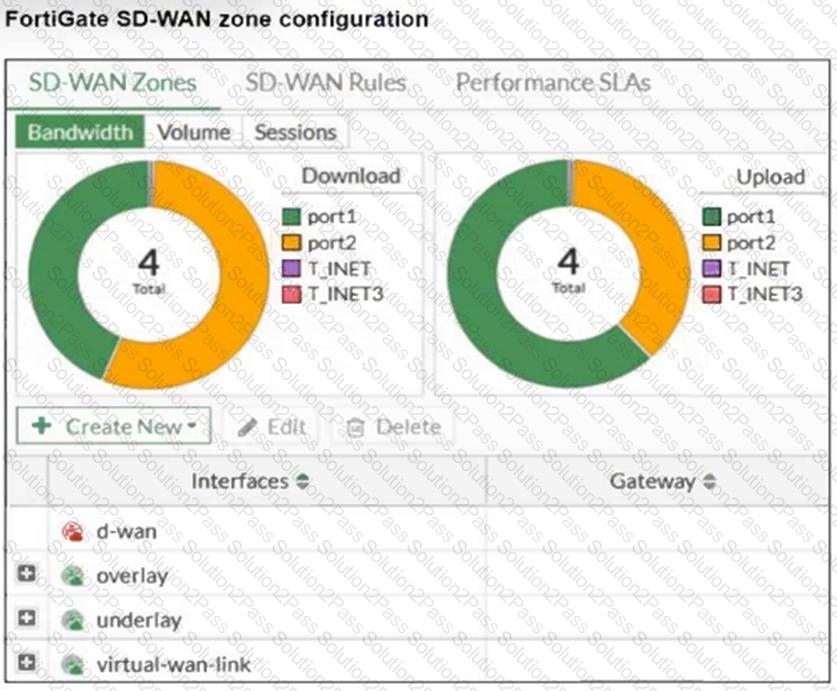
Based on the exhibit, which statement is true?
An administrator is configuring an IPsec VPN between site A and site В. The Remote Gateway setting in both sites has been configured as Static IP Address.
For site A, the local quick mode selector is 192.168.1.0/24 and the remote quick mode selector is 192.168.2.0/24.
Which subnet must the administrator configure for the local quick mode selector for site B?
Refer to the exhibit.
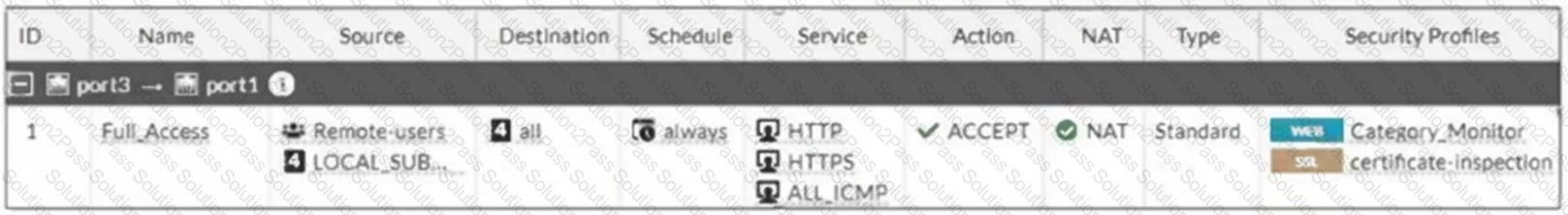
FortiGate is configured for firewall authentication. When attempting to access an external website, the user is not presented with a login prompt.
What is the most likely reason for this situation?
The HTTP inspection process in web filtering follows a specific order when multiple features are enabled in the web filter profile.
Which order must FortiGate use when the web filter profile has features such as safe search enabled?
A network administrator wants to set up redundant IPsec VPN tunnels on FortiGate by using two IPsec VPN tunnels and static routes.
All traffic must be routed through the primary tunnel when both tunnels are up. The secondary tunnel must be used only if the primary tunnel goes down. In addition, FortiGate should be able to detect a dead tunnel to speed up tunnel failover.
Which two key configuration changes must the administrator make on FortiGate to meet the requirements? (Choose two.)
What are two features of the NGFW profile-based mode? (Choose two.)
Which statement is correct regarding the use of application control for inspecting web applications?
An administrator configured a FortiGate to act as a collector for agentless polling mode.
What must the administrator add to the FortiGate device to retrieve AD user group information?
Which two features of IPsec IKEv1 authentication are supported by FortiGate? (Choose two.)
Which three statements explain a flow-based antivirus profile? (Choose three.)
Refer to the exhibits.
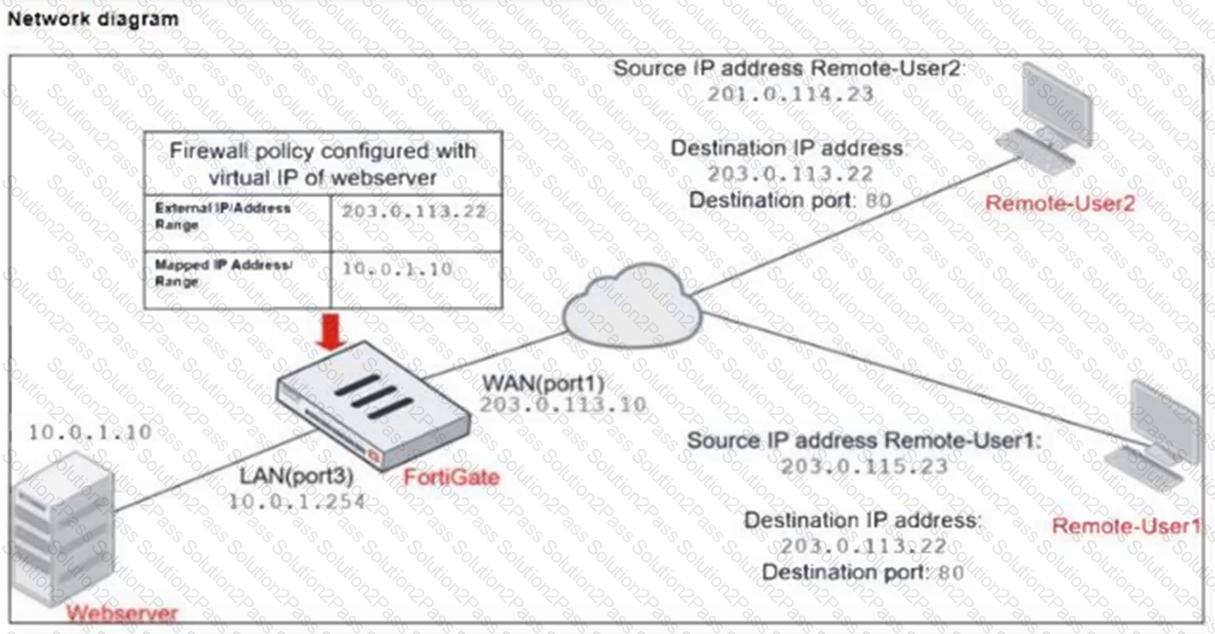
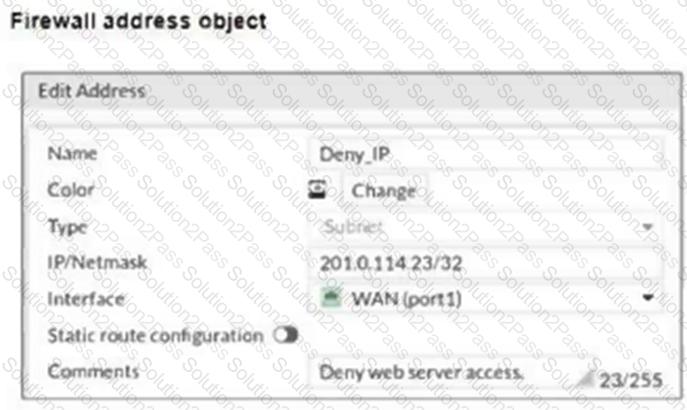
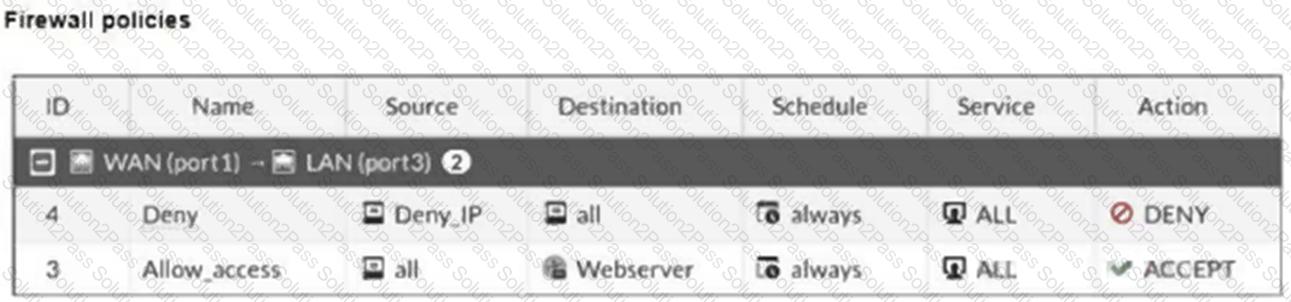
The exhibits show a diagram of a FortiGate device connected to the network, and the firewall configuration.
An administrator created a Deny policy with default settings to deny Webserver access for Remote-User2.
The policy should work such that Remote-User1 must be able to access the Webserver while preventing Remote-User2 from accessing the Webserver.
Which two configuration changes can the administrator make to the policy to deny Webserver access for Remote-User2? (Choose two.)
FortiGuard categories can be overridden and defined in different categories. To create a web rating override for the example.com home page the override must be configured using a specific syntax.
Which two syntaxes are correct to configure a web rating override for the home page? (Choose two.)
Refer to the exhibits, which show the firewall policy and the security profile for Facebook.
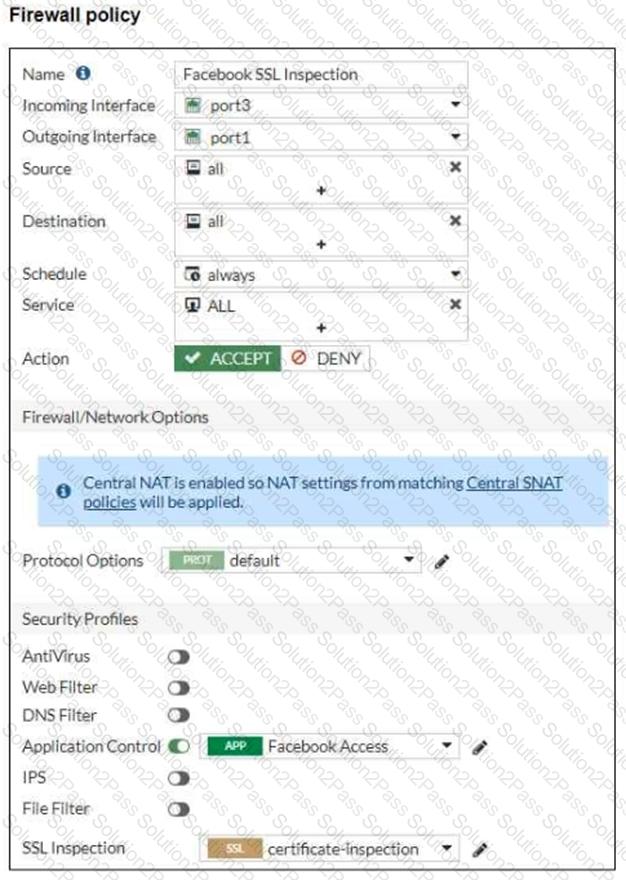
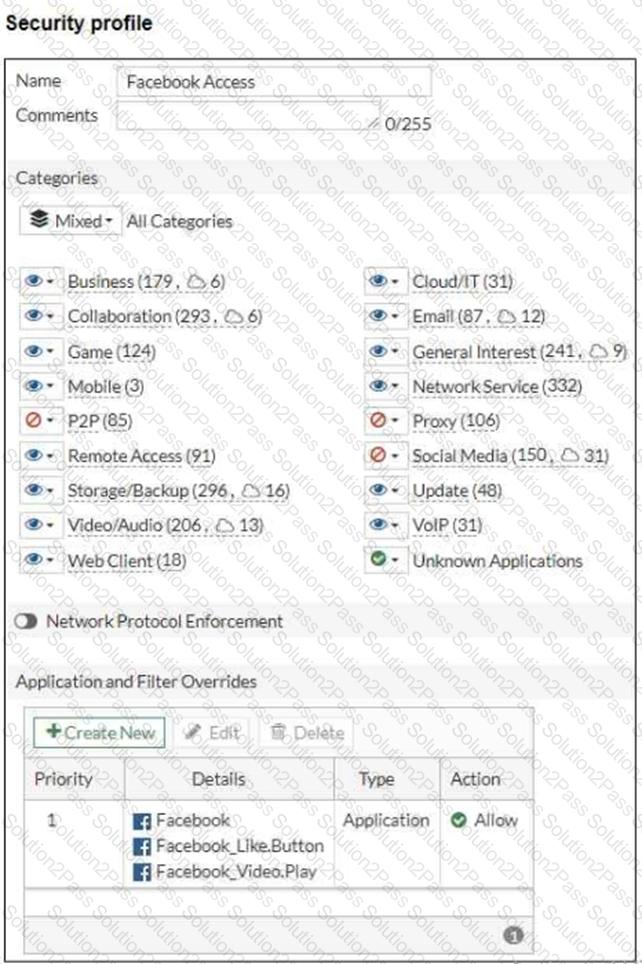
Users are given access to the Facebook web application. They can play video content hosted on Facebook but they are unable to leave reactions on videos or other types of posts.
Which part of the configuration must you change to resolve the issue?
Which two statements explain antivirus scanning modes? (Choose two.)
Refer to the exhibit.
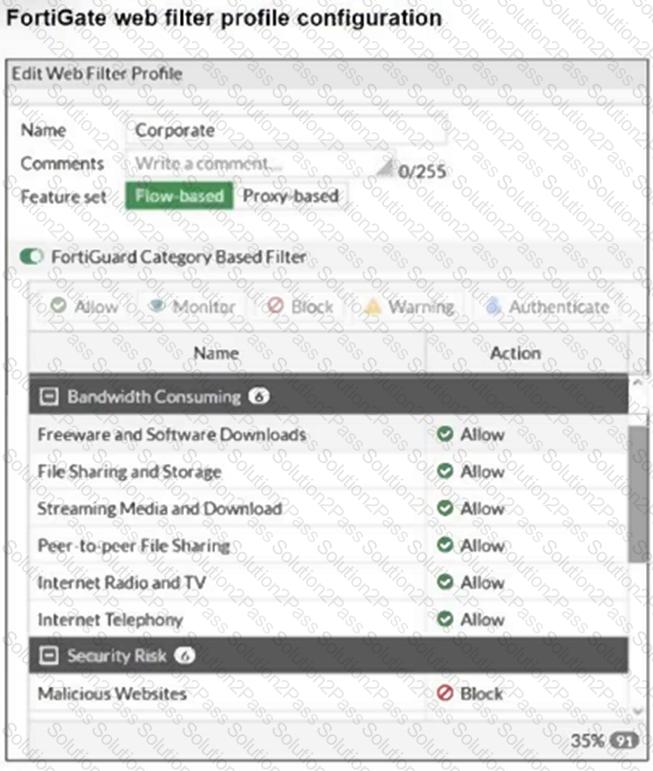
The exhibit shows theFortiGuard Category Based Filtersection of a corporate web filter profile.
An administrator must block access todownload.com, which belongs to theFreeware and Software Downloadscategory. The administrator must also allow other websites in the same category.
What are two solutions for satisfying the requirement? (Choose two.)
