FCSS_EFW_AD-7.4 Fortinet FCSS - Enterprise Firewall 7.4 Administrator Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Fortinet FCSS_EFW_AD-7.4 FCSS - Enterprise Firewall 7.4 Administrator certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Refer to the exhibit, which shows a partial troubleshooting command output.
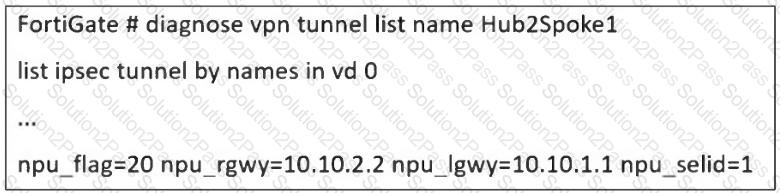
An administrator is extensively using IPsec on FortiGate. Many tunnels show information similar to the output shown in the exhibit.
What can the administrator conclude?
A company's guest internet policy, operating in proxy mode, blocks access to Artificial Intelligence Technology sites using FortiGuard. However, a guest user accessed a page in this category using port 8443.
Which configuration changes are required for FortiGate to analyze HTTPS traffic on nonstandard ports like 8443 when full SSL inspection is active in the guest policy?
Refer to the exhibit, which shows a corporate network and a new remote office network.
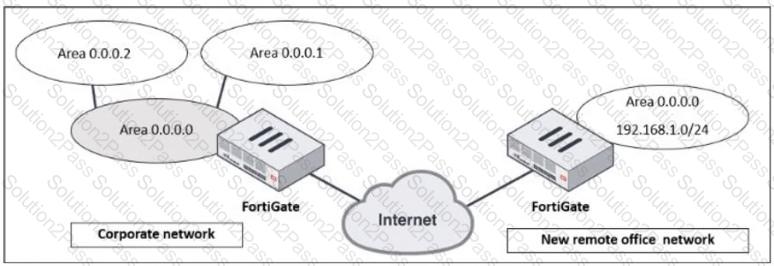
An administrator must integrate the new remote office network with the corporate enterprise network.
What must the administrator do to allow routing between the two networks?
What is the initial step performed by FortiGate when handling the first packets of a session?
An administrator must enable direct communication between multiple spokes in a company's network. Each spoke has more than one internet connection.
The requirement is for the spokes to connect directly without passing through the hub, and for the links to automatically switch to the best available connection.
How can this automatic detection and optimal link utilization between spokes be achieved?
A FortiGate device with UTM profiles is reaching the resource limits, and the administrator expects the traffic in the enterprise network to increase.
The administrator has received an additional FortiGate of the same model.
Which two protocols should the administrator use to integrate the additional FortiGate device into this enterprise network? (Choose two.)
Refer to the exhibits.
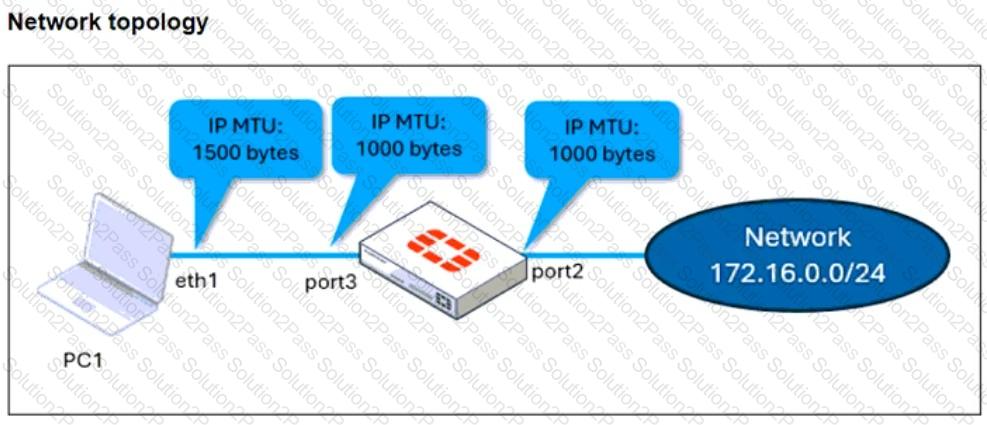
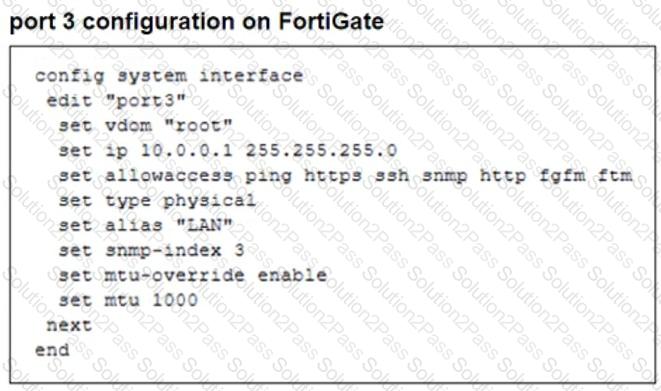
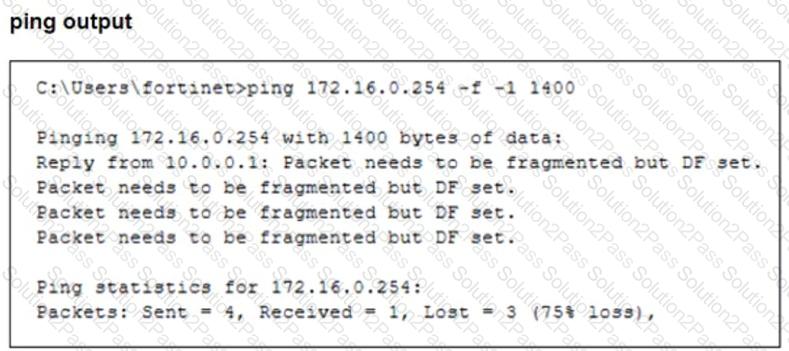
The configuration of a user's Windows PC, which has a default MTU of 1500 bytes, along with FortiGate interfaces set to an MTU of1000bytes, and the results of PC1 pinging server172.16.0.254are shown.
Why is the user in Windows PC1 unable to ping server172.16.0.254and is seeing the message:Packet needs to be fragmented but DF set?
Refer to the exhibits.
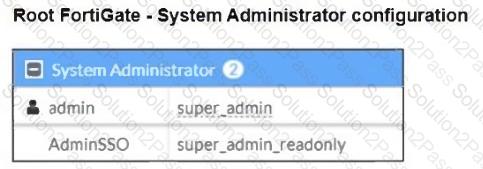
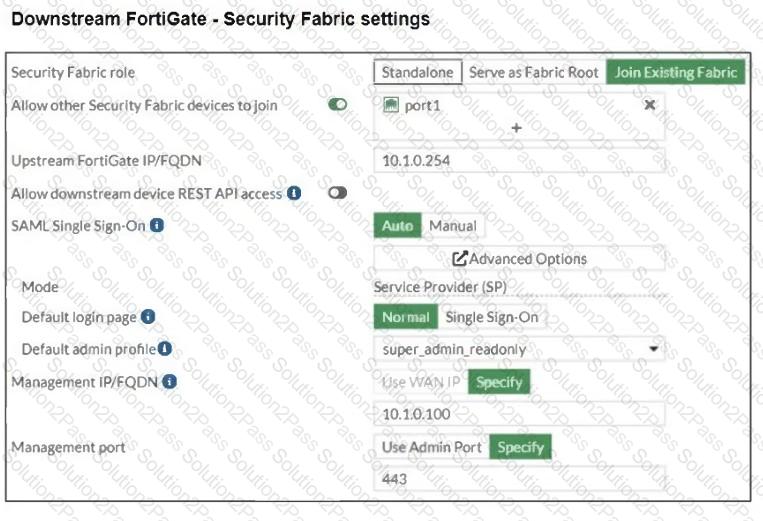
The Administrators section of a root FortiGate device and the Security Fabric Settings section of a downstream FortiGate device are shown.
When prompted to sign in with Security Fabric in the downstream FortiGate device, a user enters the AdminSSO credentials.
What is the next status for the user?
An administrator is designing an ADVPN network for a large enterprise with spokes that have varying numbers of internet links. They want to avoid a high number of routes and peer connections at the hub.
Which method should be used to simplify routing and peer management?
How will configuring set tcp-mss-sender and set tcp-mss-receiver in a firewall policy affect the size and handling of TCP packets in the network?
A company that acquired multiple branches across different countries needs to install new FortiGate devices on each of those branches. However, the IT staff lacks sufficient knowledge to implement the initial configuration on the FortiGate devices.
Which three approaches can the company take to successfully deploy advanced initial configurations on remote branches? (Choose three.)
Refer to the exhibit, which shows a partial enterprise network.
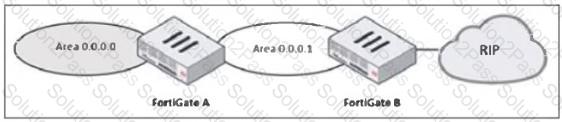
An administrator would like the area 0.0.0.0 to detect the external network.
What must the administrator configure?
An administrator configured the FortiGate devices in an enterprise network to join the Fortinet Security Fabric. The administrator has a list of IP addresses that must be blocked by the data center firewall. This list is updated daily.
How can the administrator automate a firewall policy with the daily updated list?
An administrator needs to install an IPS profile without triggering false positives that can impact applications and cause problems with the user's normal traffic flow.
Which action can the administrator take to prevent false positives on IPS analysis?
Refer to the exhibit, which shows a hub and spokes deployment.
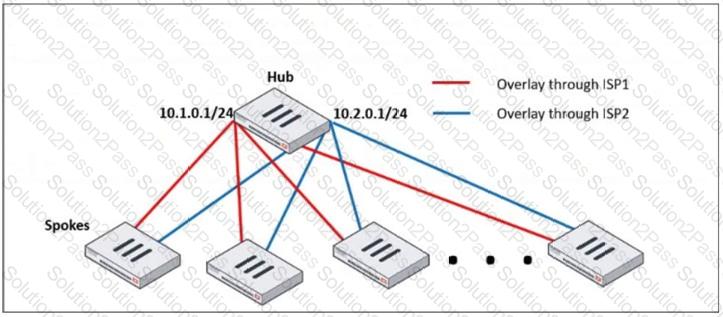
An administrator is deploying several spokes, including the BGP configuration for the spokes to connect to the hub.
Which two commands allow the administrator to minimize the configuration? (Choose two.)
An administrator is extensively using VXLAN on FortiGate.
Which specialized acceleration hardware does FortiGate need to improve its performance?
Refer to the exhibit, which shows an enterprise network connected to an internet service provider.
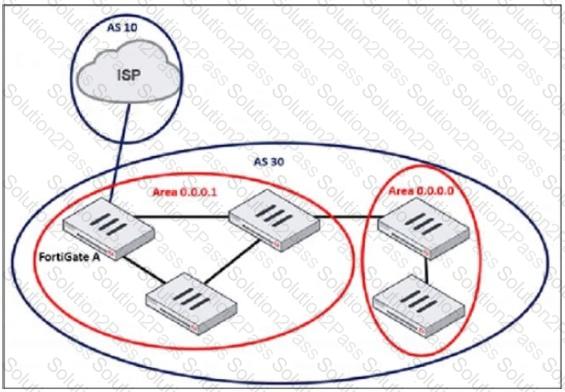
The administrator must configure the BGP section of FortiGate A to give internet access to the enterprise network.
Which command must the administrator use to establish a connection with the internet service provider?
 FGSP allowssession-aware load balancingbetween multiple FortiGate units without requiring them to be in an HA (High Availability) cluster.
FGSP allowssession-aware load balancingbetween multiple FortiGate units without requiring them to be in an HA (High Availability) cluster. Withexternal load balancers, incoming traffic isevenly distributedacross multiple FortiGate devices.
Withexternal load balancers, incoming traffic isevenly distributedacross multiple FortiGate devices. This approach is useful forscaling outtraffic handling capacity while ensuring that sessions remainsynchronizedbetween firewalls.
This approach is useful forscaling outtraffic handling capacity while ensuring that sessions remainsynchronizedbetween firewalls. FGSP is effectivewhen stateful failover is requiredbut without the constraints of traditional HA.
FGSP is effectivewhen stateful failover is requiredbut without the constraints of traditional HA. FGCPactive-active modeenables multiple FortiGate devices toshare traffic loads, increasing throughput and efficiency.
FGCPactive-active modeenables multiple FortiGate devices toshare traffic loads, increasing throughput and efficiency. Active-active mode is suitable forbalancing UTM processingacross multiple FortiGates, making it ideal whenresource limits are a concern.
Active-active mode is suitable forbalancing UTM processingacross multiple FortiGates, making it ideal whenresource limits are a concern. Usingswitchesensures redundancy and avoids single points of failure in the network.
Usingswitchesensures redundancy and avoids single points of failure in the network. This mode is commonly used inenterprise networkswhere bothscalability and redundancyare required.
This mode is commonly used inenterprise networkswhere bothscalability and redundancyare required.