FCSS_EFW_AD-7.6 Fortinet NSE 7 - Enterprise Firewall 7.6 Administrator Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Fortinet FCSS_EFW_AD-7.6 Fortinet NSE 7 - Enterprise Firewall 7.6 Administrator certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Refer to the exhibit, which shows the packet capture output of a three-way handshake between FortiGate and FortiManager Cloud.
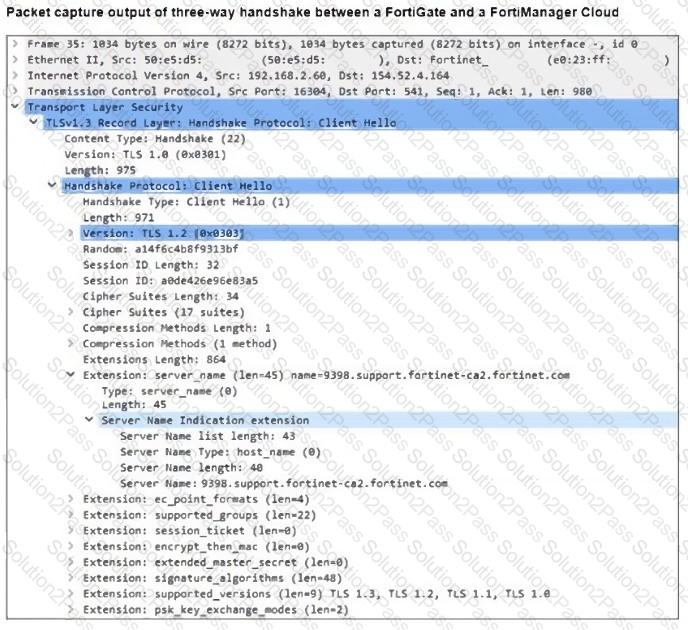
What two conclusions can you draw from the exhibit? (Choose two.)
Refer to the exhibit, which contains the partial output of an OSPF command.
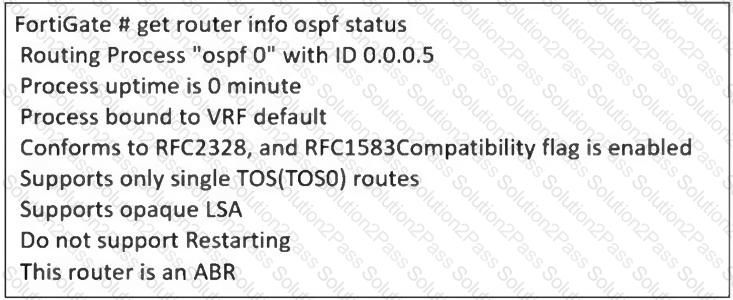
An administrator is checking the OSPF status of a FortiGate device and receives the output shown in the exhibit.
What two conclusions can the administrator draw? (Choose two.)
How will configuring set tcp-mss-sender and set tcp-mss-receiver in a firewall policy affect the size and handling of TCP packets in the network?
An administrator is checking an enterprise network and sees a suspicious packet with the MAC address e0:23:ff:fc:00:86.
What two conclusions can the administrator draw? (Choose two.)
Refer to the exhibit.
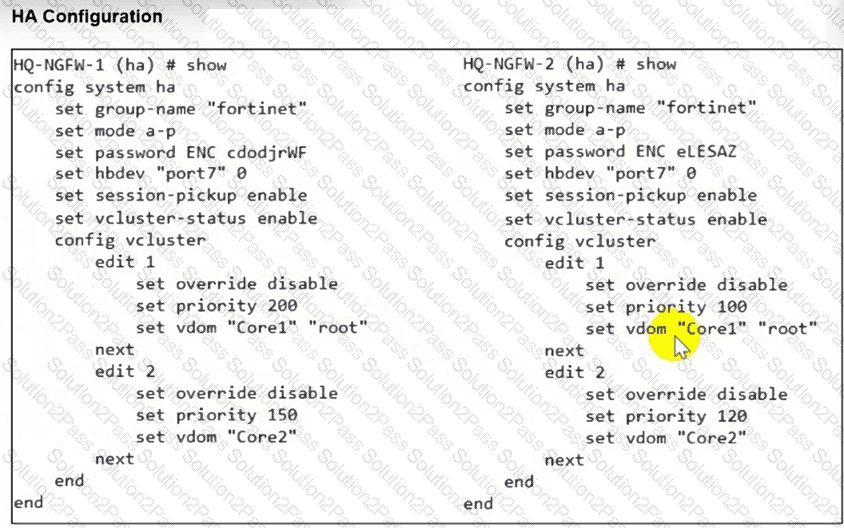
An HA configuration of an active-active (A-A) cluster with the same HA uptime is shown. You want HQ-NGFW-2 to handle the Core2 VDOM traffic. Which modification must you make to achieve this outcome? (Choose one answer)
Refer to the exhibit.
The partial output of an OSPF command is shown. You are checking the OSPF status of a FortiGate device when you receive the output shown in the exhibit. Based on the output, which two statements about FortiGate are correct? (Choose two answers)
What action can be taken on a FortiGate to block traffic using IPS protocol decoders, focusing on network transmission patterns and application signatures?
An administrator must enable direct communication between multiple spokes in a company's network. Each spoke has more than one internet connection.
The requirement is for the spokes to connect directly without passing through the hub, and for the links to automatically switch to the best available connection.
How can this automatic detection and optimal link utilization between spokes be achieved?
The IT department discovered during the last network migration that all zero phase selectors in phase 2 IPsec configurations impacted network operations.
What are two valid approaches to prevent this during future migrations? (Choose two.)
An administrator must minimize CPU and RAM use on a FortiGate firewall while also enabling essential security features, such as web filtering and application control for HTTPS traffic.
Which SSL inspection setting helps reduce system load while also enabling security features, such as web filtering and application control for encrypted HTTPS traffic?
An administrator wants to scale the IBGP sessions and optimize the routing table in an IBGP network.
Which parameter should the administrator configure?
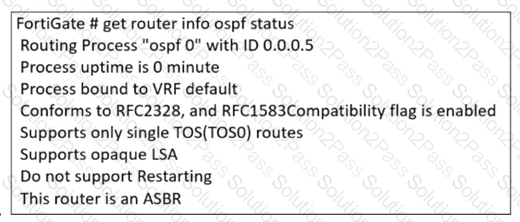
Refer to the exhibit.
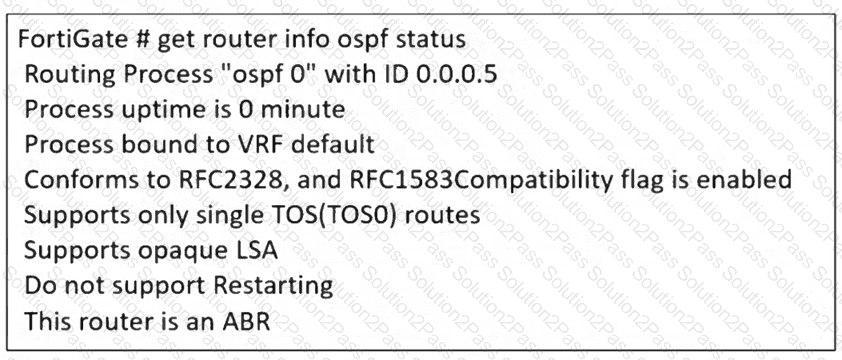
The partial output of an OSPF command is shown. While checking the OSPF status of FortiGate, you receive the output shown in the exhibit. Based on the output, which two statements about FortiGate are correct? (Choose two answers)
Refer to the exhibit.

The routing tables of FortiGate_A and FortiGate_B are shown. FortiGate_A and FortiGate_B are in the same autonomous system.
The administrator wants to dynamically add only route 172.16.1.248/30 on FortiGate_A.
What must the administrator configure?
An administrator is extensively using VXLAN on FortiGate.
Which specialized acceleration hardware does FortiGate need to improve its performance?
Refer to the exhibit, which shows a revision history window in the FortiManager device layer.
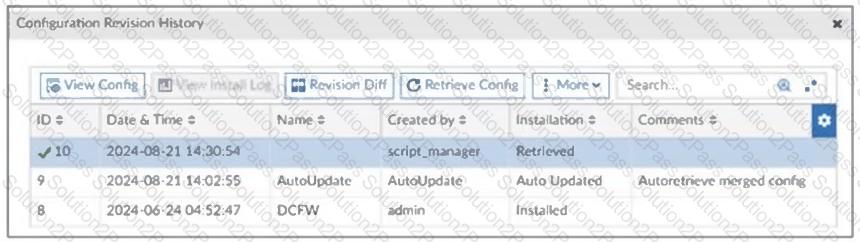
The IT team is trying to identify the administrator responsible for the most recent update in the FortiGate device database.
Which conclusion can you draw about this scenario?
A company that acquired multiple branches across different countries needs to install new FortiGate devices on each of those branches. However, the IT staff lacks sufficient knowledge to implement the initial configuration on the FortiGate devices.
Which three approaches can the company take to successfully deploy advanced initial configurations on remote branches? (Choose three.)
Refer to the exhibit, which shows a command output.

FortiGate_A and FortiGate_B are members of an FGSP cluster in an enterprise network.
While testing the cluster using the ping command, the administrator monitors packet loss and found that the session output on FortiGate_B is as shown in the exhibit.
What could be the cause of this output on FortiGate_B?
A vulnerability scan report has revealed that a user has generated traffic to the website example.com (10.10.10.10) using a weak SSL/TLS version supported by the HTTPS web server.
What can the firewall administrator do to block all outdated SSL/TLS versions on any HTTPS web server to prevent possible attacks on user traffic?
Refer to the exhibit, which shows the HA status of an active-passive cluster.
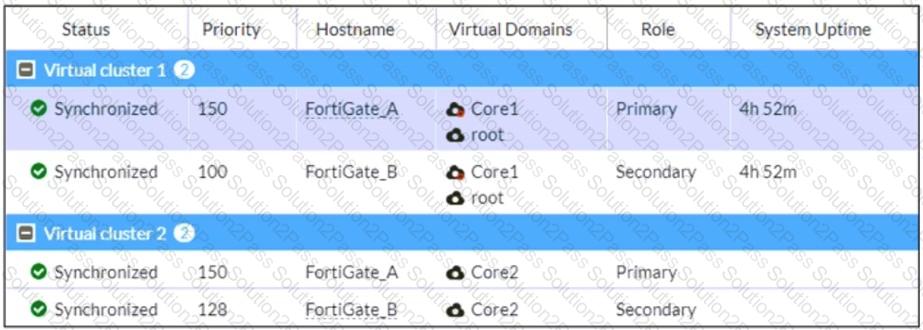
An administrator wants FortiGate_B to handle the Core2 VDOM traffic.
Which modification must the administrator apply to achieve this?
