NSE7_CDS_AR-7.6 Fortinet NSE 7 - Public Cloud Security 7.6.4 Architect Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Fortinet NSE7_CDS_AR-7.6 Fortinet NSE 7 - Public Cloud Security 7.6.4 Architect certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Refer to the exhibit.

Which FortiCNP policy type generated the finding shown in the exhibit? (Choose one answer)
You are investigating an attack path for a top risky host. You notice that the Common Vulnerability Scoring System (CVSS) and the vulnerability impact scores are very high. However, the attack path severity for the top risky host itself is low. Which two pieces of contextualized information can help you understand why? (Choose two answers)
In an SD-WAN TGW Connect topology, which three initial steps are mandatory when routing traffic from a spoke VPC to a security VPC through a Transit Gateway? (Choose three.)
Which statement about Transit Gateway (TGW) in Amazon Web Services (AWS) is true?
Refer to the exhibit.

You are troubleshooting a Microsoft Azure SDN connector issue on your FortiGate VM in Azure.
Which command can you use to examine details about API calls sent by the connector?
The cloud administration team is reviewing an AWS deployment that was done using CloudFormation.
The deployment includes six FortiGate instances that required custom configuration changes after being deployed. The team notices that unwanted traffic is reaching some of the FortiGate instances because the template is missing a security group.
To resolve this issue, the team decides to update the JSON template with the missing security group and then apply the updated template directly, without using a change set.
What is the result of following this approach?
An administrator implements FortiWeb ingress controller to protect containerized web applications in an AWS Elastic Kubernetes Service (EKS) cluster.

What can you conclude about the topology shown in FortiView?
Refer to the exhibit.
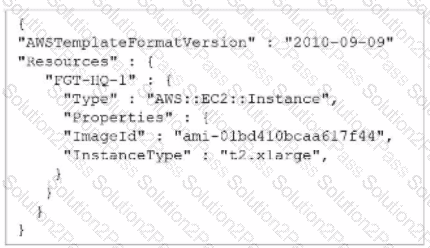
A senior administrator in a multinational organization needs to include a comment in the template shown in the exhibit to ensure that administrators from other regions change the Amazon Machine Image (AMI) ID to one that is valid in their location.
How can the administrator add the required comment in that section of the file?
An organization is deploying FortiDevSec to enhance security for containerized applications, and they need to ensure containers are monitored for suspicious behavior at runtime.
Which FortiDevSec feature is best for detecting runtime threats?
Refer to the exhibit.
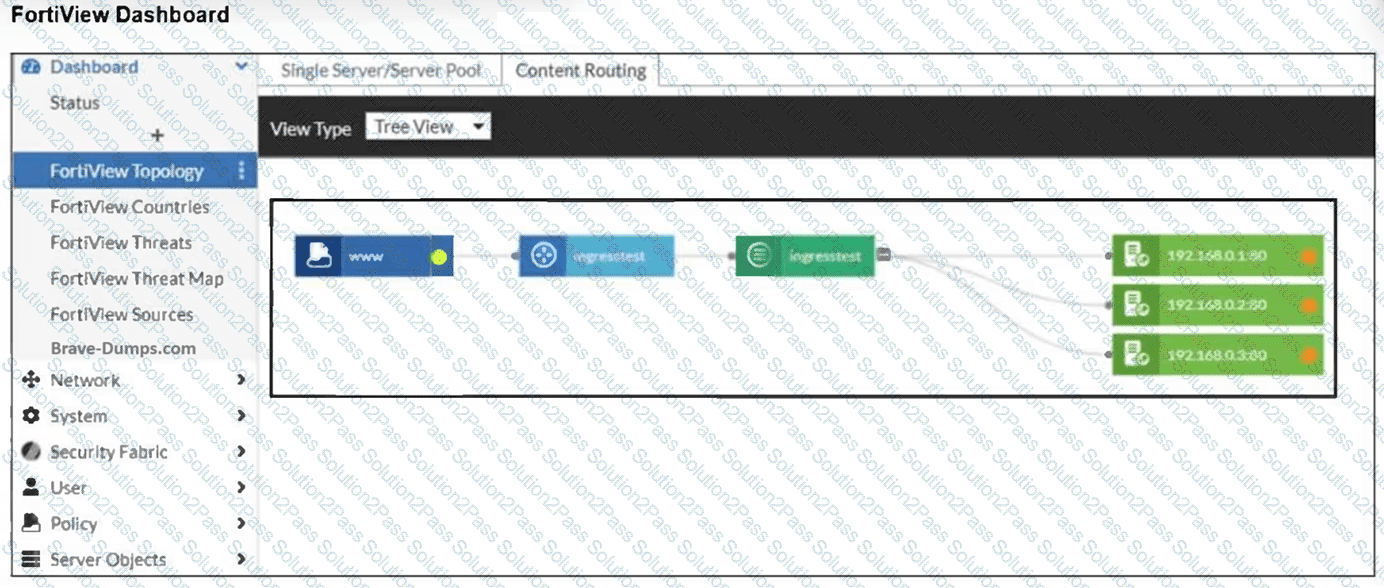
An administrator installed a FortiWeb ingress controller to protect a containerized web application. What is the reason for the status shown in FortiView? (Choose one answer)
You need a solution to safeguard public cloud-hosted web applications from the OWASP Top 10 vulnerabilities. The solution must support the same region in which your applications reside, with minimum traffic cost.
Which solution meets the requirements?
You have deployed a FortiGate HA cluster in Azure using a gateway load balancer for traffic inspection. However, traffic is not being routed correctly through the firewalls.
What can be the cause of the issue?
Refer to the exhibit.

You are managing an active-passive FortiGate HA cluster in AWS that was deployed using CloudFormation. You have created a change set to examine the effects of some proposed changes to the current infrastructure. The exhibit shows some sections of the change set.
What will happen if you apply these changes?
Your administrator instructed you to deploy an Azure vWAN solution to create a connection between the main company site and branch sites to the other company VNETs. What is the best connection solution available between your company headquarters, branch sites, and the Azure vWAN hub? (Choose one answer)
What is the main advantage of using SD-WAN Transit Gateway Connect over traditional SD-WAN?
Refer to the exhibit.

After the initial Terraform configuration in Microsoft Azure, the terraform plan command is run.
Which two statements about running the terraform plan command are true? (Choose two.)
