NSE7_EFW-7.2 Fortinet NSE 7 - Enterprise Firewall 7.2 Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Fortinet NSE7_EFW-7.2 Fortinet NSE 7 - Enterprise Firewall 7.2 certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
You want to block access to the website ww.eicar.org using a custom IPS signature.
Which custom IPS signature should you configure?
A)
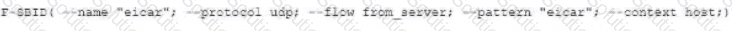
B)

C)
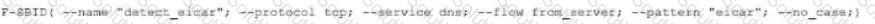
D)

Which two statements about IKE vision 2 are true? (Choose two.)
Exhibit.
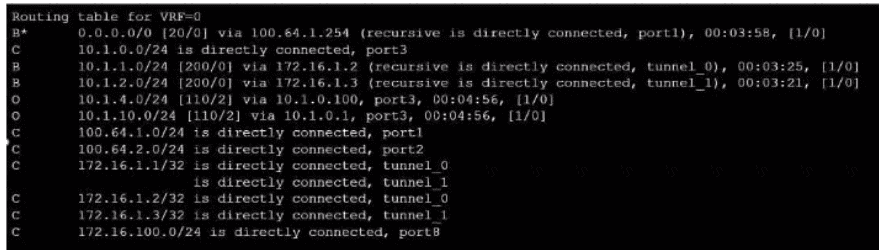
Refer to the exhibit, which shows a partial touting table
What two concisions can you draw from the corresponding FortiGate configuration? (Choose two.)
You want to improve reliability over a lossy IPSec tunnel.
Which combination of IPSec phase 1 parameters should you configure?
Refer to the exhibit.
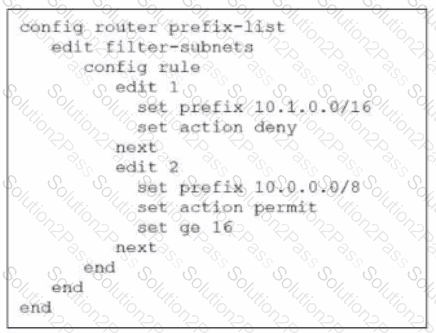
The exhibit shows a prefix list configuration
What can you conclude from the above prefix-list configuration?
Which two statements about the neighbor-group command are true? (Choose two.)
Refer to the exhibit.
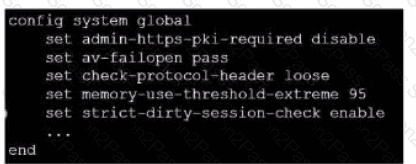
which contains a partial configuration of the global system. What can you conclude from this output?
Which two statements about the BFD parameter in BGP are true? (Choose two.)
Refer to the exhibits, which contain the network topology and BGP configuration for a hub.
Exhibit A.
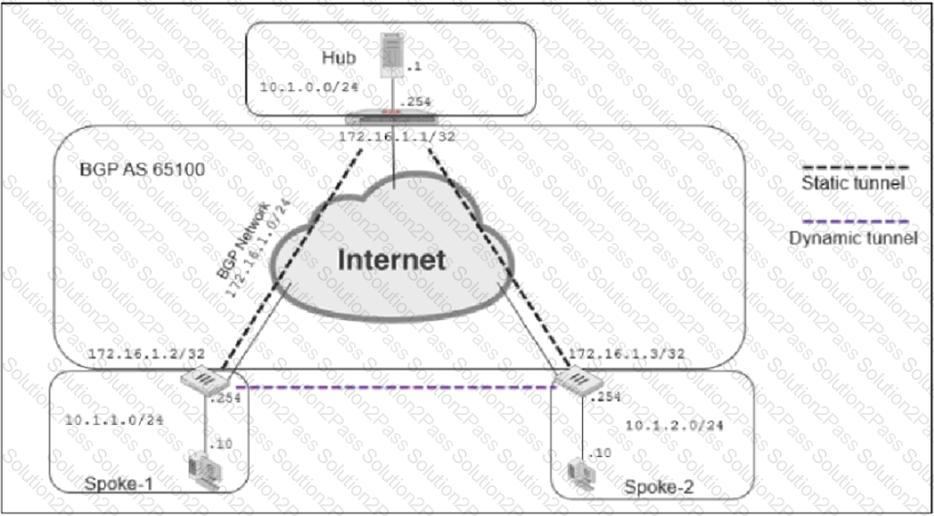
Exhibit B.
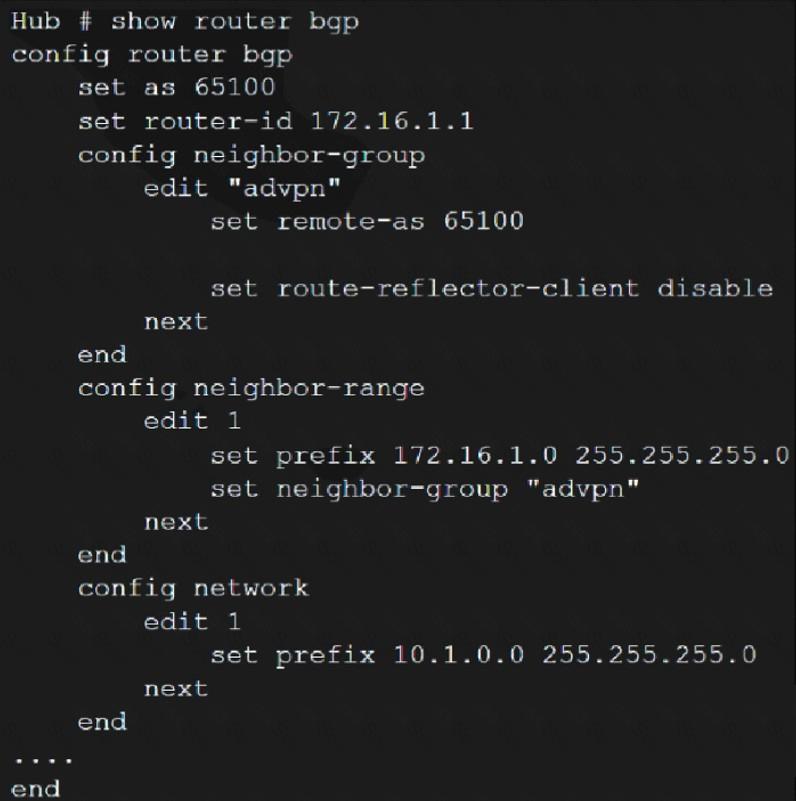
An administrator is trying to configure ADVPN with a hub and spoke VPN setup using iBGP. All the VPNs are up and connected to the hub. The hub is receiving route information from both spokes over iBGP; however the spokes are not receiving route information from each other.
What change must the administrator make to the hub BGP configuration so that the routes learned from one spoke are forwarded to the other spoke?
Refer to the exhibit, which shows a partial routing table.
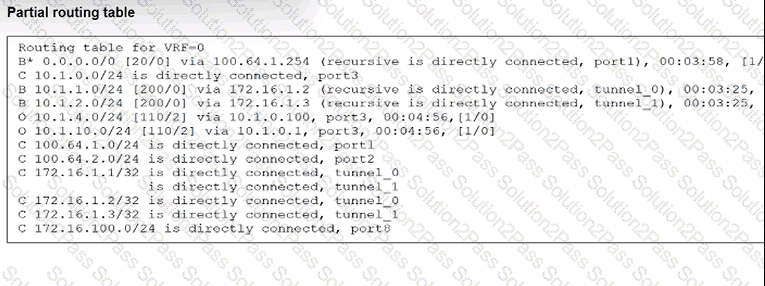
What two conclusions can you draw from the FortiGate output shown in the
exhibit? (Choose two.)
Which, three conditions are required for two FortiGate devices to form an OSPF adjacency? (Choose three.)
Which two statements about the Security fabric are true? (Choose two.)
Refer to the exhibit, which contains a partial configuration of the global system.

What can you conclude from the output?
Which FortiGate in a Security I auric sends togs to FortiAnalyzer?
Refer to the exhibit, which contains a partial OSPF configuration.
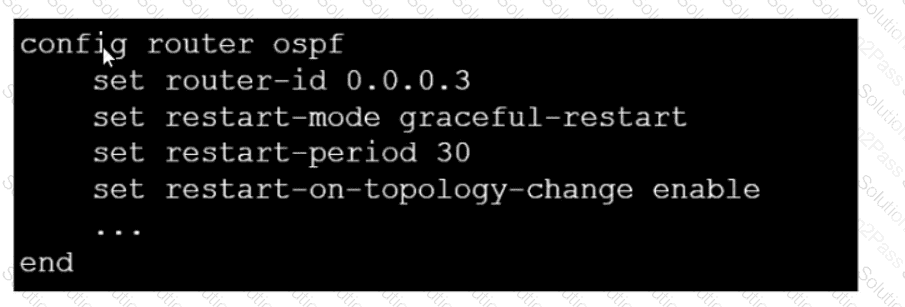
What can you conclude from this output?
Exhibit.
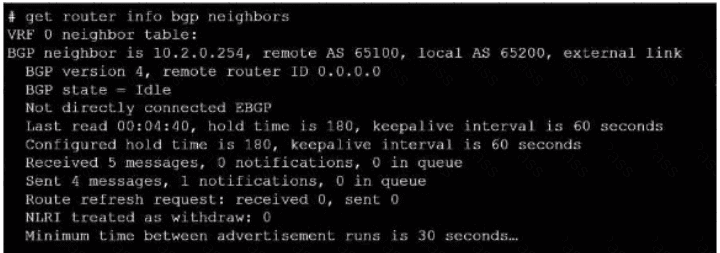
Refer to the exhibit, which provides information on BGP neighbors.
Which can you conclude from this command output?
What are two functions of automation stitches? (Choose two.)
An administrator configured the following command on FortiGate
config router ospf
sec reszart-mode graceful-restart
Which two statements correctly describe the result of the above command? (Choose two.)
Which configuration can be used to reduce the number of BGP sessions in on IBGP network?
Exhibit.
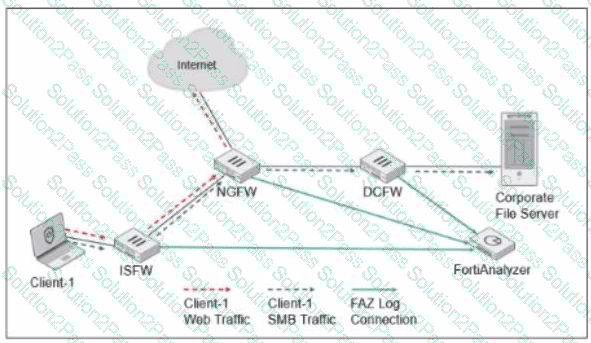
ISFW is installed in the access layer NGFW is performing SNAT and web tittering DCFW is running IPS Which two statements are true regarding the Security Fabric logging? (Choose two.)
