NSE7_SSE_AD-25 Fortinet NSE 7 - FortiSASE 25 Enterprise Administrator Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Fortinet NSE7_SSE_AD-25 Fortinet NSE 7 - FortiSASE 25 Enterprise Administrator certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which two statements about FortiSASE Geofencing with regional compliance are true? (Choose two answers)
Which two settings are automatically pushed from FortiSASE to FortiClient in a new FortiSASE deployment with default settings? (Choose two answers)
A Fortinet customer is considering integrating FortiManager with FortiSASE. What are two prerequisites they should consider? (Choose two answers)
Which information does FortiSASE use to bring network lockdown into effect on an endpoint? (Choose one answer)
What is the purpose of security posture tagging in ZTNA? (Choose one answer)
When viewing the daily summary report generated by FortiSASE. the administrator notices that the report contains very little data. What is a possible explanation for this almost empty report?
What are two benefits of deploying secure private access (SPA) with SD-WAN? (Choose two answers)
How does FortiSASE hide user information when viewing and analyzing logs?
During FortiSASE provisioning, how many security points of presence (POPs) need to be configured by the FortiSASE administrator?
What can be configured on FortiSASE as an additional layer of security for FortiClient registration? (Choose one answer)
Which two statements about the Hub Selection Method in FortiSASE Secure Private Access (SPA) are correct? (Choose two answers)
Refer to the exhibits.

A FortiSASE administrator has configured FortiSASE as a spoke to a FortiGate hub. The tunnel is up to the FortiGate hub. However, the remote FortiClient is not able to access the web server hosted behind the FortiGate hub. What is the reason for the access failure? (Choose one answer)
An administrator must restrict endpoints from certain countries from connecting to FortiSASE. Which configuration can achieve this? (Choose one answer)
You are designing a new network for Company X and one of the new cybersecurity policy requirements is that all remote user endpoints must always be connected and protected Which FortiSASE component facilitates this always-on security measure?
To complete their day-to-day operations, remote users require access to a TCP-based application that is hosted on a private web server. Which FortiSASE deployment use case provides the most efficient and secure method for meeting the remote users' requirements?
Refer to the exhibits.
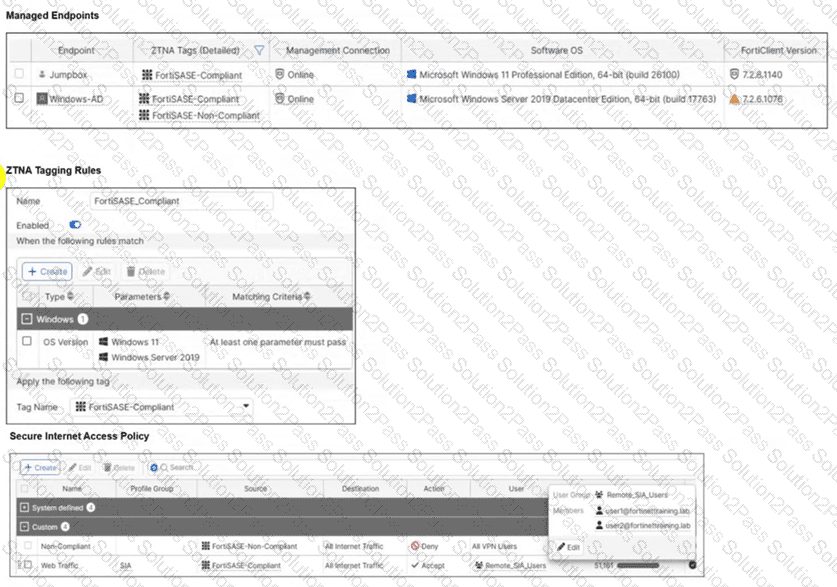
Jumpbox and Windows-AD are endpoints from the same remote location. Jumpbox can access the internet through FortiSASE, while Windows-AD can no longer access the internet. Based on the information in the exhibits, which reason explains the outage on Windows-AD? (Choose one answer)
Which secure internet access (SIA) use case minimizes individual workstation or device setup, because you do not need to install FortiClient on endpoints or configure explicit web proxy settings on web browser-based end points?
A FortiSASE administrator is configuring a Secure Private Access (SPA) solution to share endpoint information with a corporate FortiGate.
Which three configuration actions will achieve this solution? (Choose three.)
Refer to the exhibit.
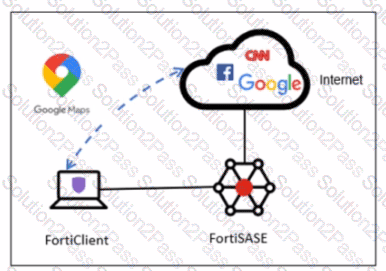
An organization must inspect all the endpoint internet traffic on FortiSASE, and exclude Google Maps traffic from the FortiSASE tunnel and redirect it to the endpoint physical interface.
Which configuration must you apply to achieve this requirement? (Choose one answer)
What are two advantages of using zero-trust tags? (Choose two.)
