G2700 GIAC Certified ISO-2700 Specialist Practice Test Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC G2700 GIAC Certified ISO-2700 Specialist Practice Test certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
You work as an Information Security Manager for uCertify Inc. The company has made a contract with a third party software company to make a software program for personal use. You have been assigned the task to share the organization's personal requirements regarding the tool to the third party. Which of the following documents should be first signed by the third party?
Mark works as a Software Developer for TechNet Inc. He has recently been fired, as he was caught doing some illegal work in the organization. Before leaving the organization, he decided to retaliate against the organization. He deleted some of the system files and made some changes in the registry files created by him. Which of the following types of attacks has Mark performed?
Fill in the blank with an appropriate phrase.
_________accord describes the minimum regulatory capital to be allocated by each bank based on its risk profile of assets.
Which of the following is an authentication scheme used by Point to Point Protocol (PPP) servers to validate the identity of remote clients?
Which of the following statements are true about Information Security Management?
Each correct answer represents a complete solution. Choose all that apply.
Mark works as a Network Security Administrator for uCertify Inc. He has been assigned the task of installing a MySQL server. Mark wants to monitor only the data that is directed to or originating from the server and he also wants to monitor running processes, file system access and integrity, and user logins for identifying malicious activities. Which of the following intrusion detection techniques will Mark use to accomplish the task?
Which of the following types of attack can be used to break the best physical and logical security mechanism to gain access to a system?
You work as an Information Security Manager for uCertify Inc. You are working on asset management. You have been assigned the task to secure information labeling and handling within the organization. Which of the following controls of the ISO standard is concerned with information labeling and handling?
You work as a Security Administrator for uCertify Inc. You have been assigned a task to implement information classification levels. You want to put the highly sensitive documents that should only be accessed by few people of the organization. In which of the following information classification levels should you put those documents?
You work as a Project Manager for uCertify Inc. You are working on an asset management plan.
You need to make the documentation on every single process related to asset management.
Which of the following is an example of asset management?
Mark works as a Network Security Administrator for uCertify Inc. An employee of the organization comes to Mark and tells him that a few months ago, the employee had filled an online bank form due to some account related work. Today, when again visiting the site, the employee finds that some of his personal information is still being displayed in the webpage. Which of the following types of cookies should be disabled by Mark to resolve the issue?
Which of the following international information security standards is concerned with anticipating and responding to information security breaches?
David works as the Chief Information Security Officer for uCertify Inc. Which of the following are the responsibilities that should be handled by David?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is the designing phase of the ISMS?
Which of the following is the process of restoring a previous copy of the data to a known point of consistency?
Which of the following is an anomaly where a program, while writing data to a buffer, overruns the buffer's boundary and overwrites adjacent memory?
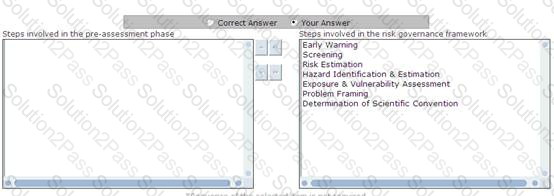
You work as a CRO for uCertify Inc. You and your team are involved in the pre-assessment phase of the risk governance framework. One of your newly joined team member wants to know the steps involved in the pre-assessment phase. Choose and reorder the steps performed in the pre-assessment phase.
Which of the following activities are performed by the 'Do' cycle component of PDCA (plan-docheck- act)?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Security Administrator for uCertify Inc. You found that a person is coming inside the working area. Now, you want to ensure the authenticity of that person. By which of the following factors can you determine the accuracy of the authentication?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is an example of a corrective measure?
