G2700 GIAC Certified ISO-2700 Specialist Practice Test Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC G2700 GIAC Certified ISO-2700 Specialist Practice Test certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which of the following are features of protocol and spectrum analyzers?
Each correct answer represents a complete solution. Choose all that apply.
Business Continuity Planning (BCP) determines the risks to the organizational processes and creates policies, plans, and procedures in order to minimize the impact of those risks. What are the different steps in the Business Continuity Planning process?
Each correct answer represents a part of the solution. Choose all that apply.
Which of the following standards was made in 1995 by the joint initiative of the Department of Trade and Industry in the United Kingdom and leading UK private-sector businesses?
Which of the following operations are performed by the Identity Management Process?
Each correct answer represents a complete solution. Choose all that apply.
John works as an IT Technician for uCertify Inc. One morning, John receives an e-mail from the company's Manager asking him to provide his logon ID and password, but the company policy restricts users from disclosing their logon IDs and passwords. Which type of possible attack is this?
Which of the following is a technical measure?
You work as a Security Administrator for uCertify Inc. You have been assigned the task to verify the identity of the employees recruited in your organization. Which of the following components of security deals with an employee's verification in the organization?
You work as the Human Resource Manager for uCertify Inc. You need to recruit some candidates for the marketing department of the organization. Which of the following should be defined to the new employees of the organization before they have joined?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following controls are administrative in nature?
The disciplined and structured process, that integrates information security and risk management activities into the System Development Life Cycle, is provided by the risk management framework.
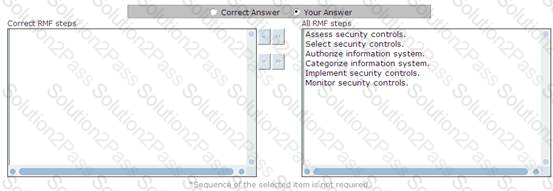
Choose the appropriate RMF steps.
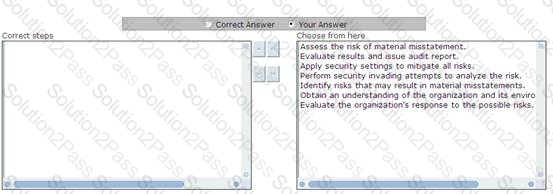
Choose and reorder the appropriate steps that you will take to perform auditing.
Which of the following information security standards deals with the protection of the computer facilities?
Which of the following states that a user should never be given more privileges than are required to carry out a task?
You work as an Information Security Manager for uCertify Inc. You have been assigned the task to create the documentation on control A.7.2 of the ISO standard. Which of the following is the chief concern of control A.7.2?
Which of the following phases of the PDCA model is the monitoring and controlling phase of the Information Security Management System (ISMS)?
Mark works as a Security Administrator for uCertify Inc. For the last few days, he is getting an error message, i.e., 'Remove the Boot.ini file because it is harmful for operating system'. When Mark reads about the Boot.ini file, he finds that it is a system file that is used to load the operating system on a computer. Which of the following types of virus has attacked Mark's computer?
Rick works as a Computer Forensic Investigator for BlueWells Inc. He has been informed that some confidential information is being leaked out by an employee of the company. Rick suspects that someone is sending the information through email. He checks the emails sent by some employees to other networks. Rick finds out that Sam, an employee of the Sales department, is continuously sending text files that contain special symbols, graphics, and signs. Rick suspects that Sam is using the Steganography technique to send data in a disguised form. Which of the following techniques is Sam using?
Each correct answer represents a part of the solution. Choose all that apply.
Which of the following are the basics of Business Continuity Management?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is also known as the 'Code for Information Security'?
Which of the following is a Restrict Anonymous registry value that allows users with explicit anonymous permissions?
