GASF GIAC Advanced Smartphone Forensics Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC GASF GIAC Advanced Smartphone Forensics certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which file, found natively on most Android devices, will contain location history such as coordinates, physical addresses and timestamps?
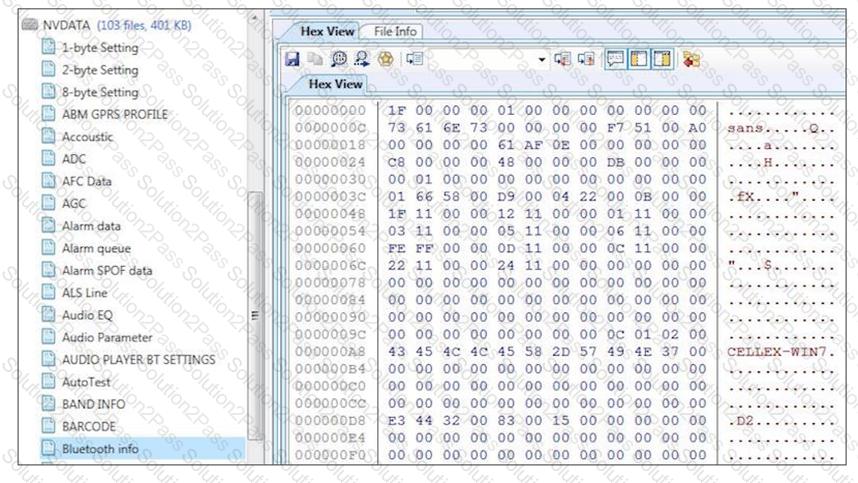
Examine the file, Bluetooth, what is the name of the device being examined?
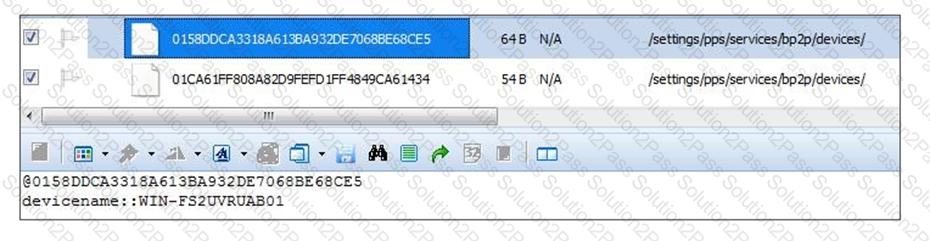
What information can you determine by reviewing the (bp2p) file from a BlackBerry OS10 handset?
Which of the following chipsets is commonly found in knock-off handsets?
Where would an examiner find evidence of an iOS update to device from one version to another?
Cellebrite Physical Analyzer uses Bit Defender to scan for malware by flagging files who have known bad hash values. This is an example of which type of mobile malware detection?
What type of storage does an iOS device use for user data?
Exhibit:
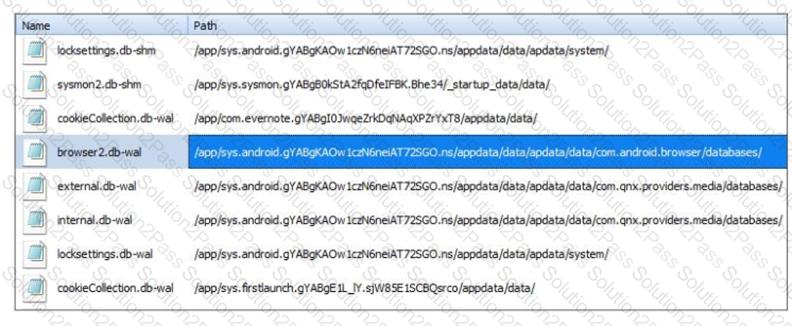
Where can an analyst find data to provide additional artifacts to support the evidence in the highlighted file?
What are the three components that make up the International Mobile Subscriber Identity (IMSI)?
Which file, located on the Android file system, may be examined to correlate files related to external SD cards that were once used in an Android device?
When examining a file system acquisition of an Android device Which artifact must be carved out manually?
You have conducted a keyword search over flash.bin and notice that multiple instances of the same data
appear many times throughout the flash image. What is this an example of?
The jTAG method is designed to acquire data through which of the following?
What is the essential piece of information is most often required in order to decrypt the contents of BlackBerry OS 10 handsets?
When examining the iOS device shown below the tool indicates that there are 4 chat messages recovered from the device.
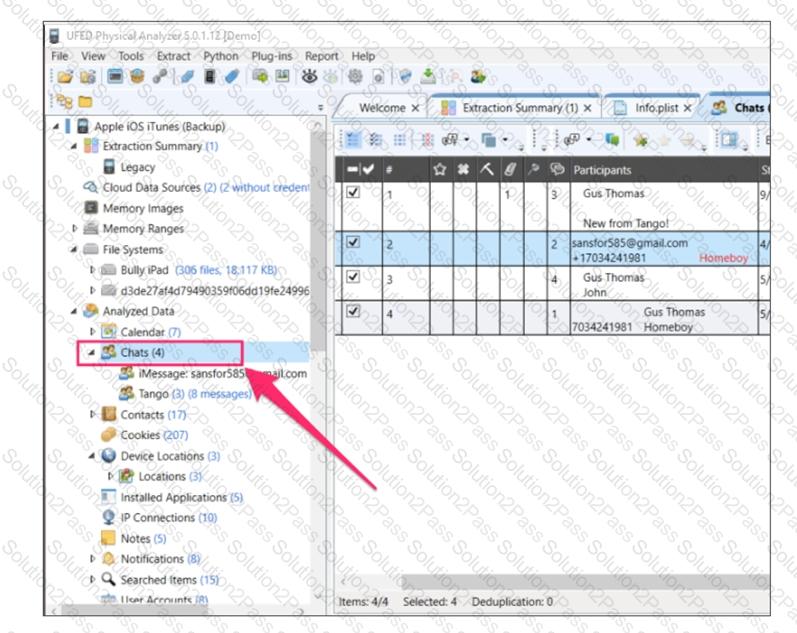
Which of the following locations may contain additional chat information?
While analysis in BlackBerry application list it appears that no third-party applications were installed on the device. Which other file may provide you with additional information on applications that were accessed with the handset?
Which artifact must be carved out manually when examining a file system acquisition of an Android device?
Review the sample database.
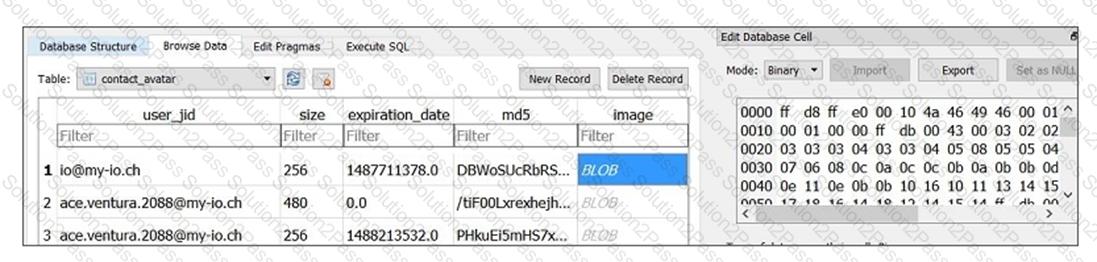
What is the BLOB column storing for this particular database table?
Which of the following is of most concern when attempting to root an Android device such as Google Glass
when conducting a forensic acquisition?
The files pictured below from a BlackBerry OS10 file system have a unique file extension.
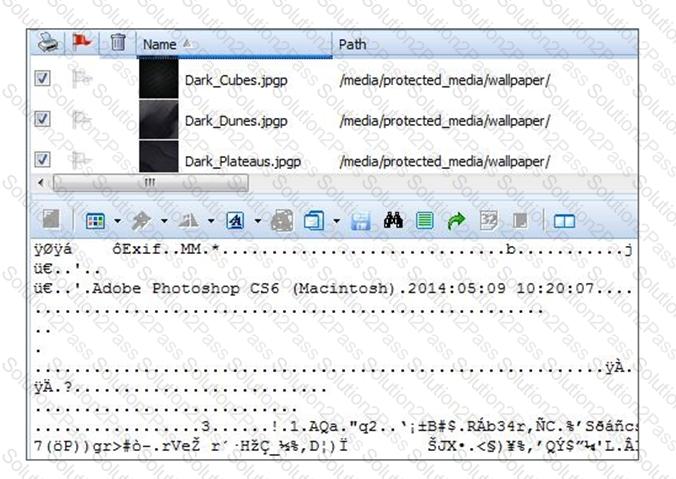
What can be concluded about these files?
