GCCC GIAC Critical Controls Certification (GCCC) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC GCCC GIAC Critical Controls Certification (GCCC) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which of the following is a reliable way to test backed up data?
As part of a scheduled network discovery scan, what function should the automated scanning tool perform?
An administrator looking at a web application’s log file found login attempts by the same host over several seconds. Each user ID was attempted with three different passwords. The event took place over 5 seconds.
ROOT
TEST
ADMIN
SQL
USER
NAGIOSGUEST
What is the most likely source of this event?
Why is it important to enable event log storage on a system immediately after it is installed?
According to attack lifecycle models, what is the attacker’s first step in compromising an organization?
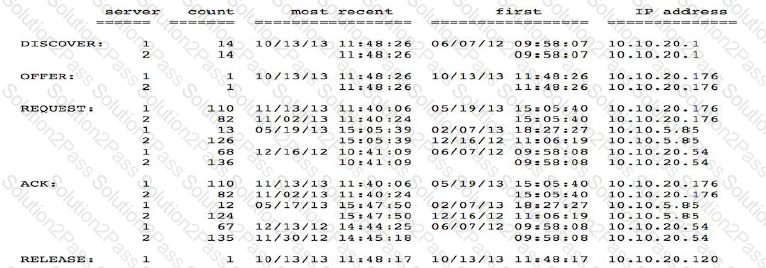
DHCP logging output in the screenshot would be used for which of the following?
What is the first step suggested before implementing any single CIS Control?
During a security audit which test should result in a source packet failing to reach its intended destination?
Which of the following archiving methods would maximize log integrity?
What is the relationship between a service and its associated port?
Below is a screenshot from a deployed next-generation firewall. These configuration settings would be a defensive measure for which CIS Control?
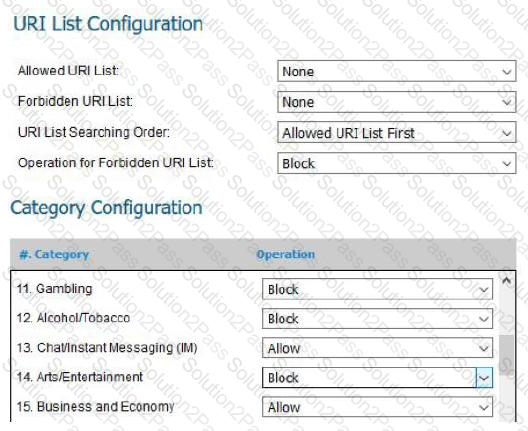
Which of the following baselines is considered necessary to implement the Boundary Defense CIS Control?
An organization has implemented a policy to continually detect and remove malware from its network. Which of the following is a detective control needed for this?
An Internet retailer's database was recently exploited by a foreign criminal organization via a remote attack. The initial exploit resulted in immediate root-level access. What could have been done to prevent this level of access being given to the intruder upon successful exploitation?
Which of the following is necessary to automate a control for Inventory and Control of Hardware Assets?
An attacker is able to successfully access a web application as root using ‘ or 1 = 1 . as the password. The successful access
indicates a failure of what process?
Beta corporation is doing a core evaluation of its centralized logging capabilities. The security staff suspects that the central server has several log files over the past few weeks that have had their contents changed. Given this concern, and the need to keep archived logs for log correction applications, what is the most appropriate next steps?
Of the options shown below, what is the first step in protecting network devices?
What is a recommended defense for the CIS Control for Application Software Security?
John is implementing a commercial backup solution for his organization. Which of the following steps should be on the configuration checklist?
