GCED GIAC Certified Enterprise Defender Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC GCED GIAC Certified Enterprise Defender certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
How does data classification help protect against data loss?
Which type of attack could be used to obtain IOS router configuration files without a valid user password?
Which of the following is an operational security control that is used as a prevention mechanism?
Which Unix administration tool is designed to monitor configuration changes to Cisco, Extreme and Foundry infrastructure devices?
When identifying malware, what is a key difference between a Worm and a Bot?
Which of the following is the best way to establish and verify the integrity of a file before copying it during an investigation?
A company estimates a loss of $2,374 per hour in sales if their website goes down. Their webserver hosting site’s documented downtime was 7 hours each quarter over the last two years. Using the information, what can the analyst determine?
Why would an incident handler acquire memory on a system being investigated?
A compromised router is reconfigured by an attacker to redirect SMTP email traffic to the attacker’s server before sending packets on to their intended destinations. Which IP header value would help expose anomalies in the path outbound SMTP/Port 25 traffic takes compared to outbound packets sent to other ports?
Who is ultimately responsible for approving methods and controls that will reduce any potential risk to an organization?
The security team wants to detect connections that can compromise credentials by sending them in plaintext across the wire. Which of the following rules should they enable on their IDS sensor?
How would an attacker use the following configuration settings?
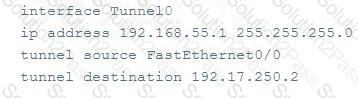
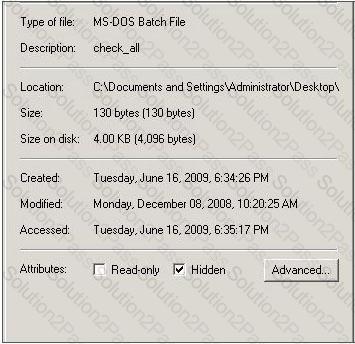
Which command tool can be used to change the read-only or hidden setting of the file in the screenshot?
What attack was indicated when the IDS system picked up the following text coming from the Internet to the web server?
select user, password from user where user= “jdoe” and password= ‘myp@55!’ union select “text”,2 into outfile “/tmp/file1.txt” - - ’
Requiring criminal and financial background checks for new employees is an example of what type of security control?
Which Windows CLI tool can identify the command-line options being passed to a program at startup?
What would a penetration tester expect to access after the following metasploit payload is delivered successfully?
Set PAYLOAD windows / shell / reverse _ tcp
What is needed to be able to use taskkill to end a process on remote system?
Why would the pass action be used in a Snort configuration file?
Which statement below is the MOST accurate about insider threat controls?
