GCIA GIAC GCIA – GIAC Certified Intrusion Analyst Practice Test Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC GCIA GCIA – GIAC Certified Intrusion Analyst Practice Test certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which of the following would allow you to automatically close connections or restart a server or service when a DoS attack is detected?
Which of the following command line tools are available in Helix Live acquisition tool on Windows?
Each correct answer represents a complete solution. Choose all that apply.
Adam works as a Network Administrator for passguide Inc. He wants to prevent the network from
DOS attacks. Which of the following is most useful against DOS attacks?
Which of the following is the correct order of loading system files into the main memory of the system, when the computer is running on Microsoft's Windows XP operating system?
Peter works as a professional Computer Hacking Forensic Investigator for eLaw-Suit law firm. He is working on a case of a cyber crime. Peter knows that the good investigative report should not only communicate the relevant facts, but also present expert opinion. This report should not include the cases in which the expert acted as a lay witness. Which of the following type of witnesses is a lay witness?
Which of the following is a reason to implement security logging on a DNS server?
Maria works as the Chief Security Officer for passguide Inc. She wants to send secret messages to the CEO of the company. To secure these messages, she uses a technique of hiding a secret message within an ordinary message. The technique provides 'security through obscurity'. What technique is Maria using?
Adam, a malicious hacker is running a scan. Statistics of the scan is as follows:
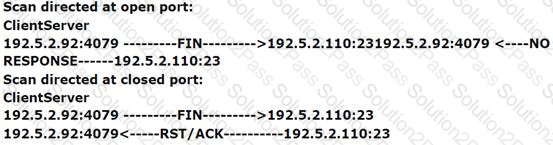
Which of the following types of port scan is Adam running?
You work as a Network Administrator for Tech Perfect Inc. The company has a TCP/IP-based network.
A branch office is connected to the headquarters through a T1 line. Users at the branch office report poor voice quality on the IP phone while communicating with the headquarters. You find that an application, named WorkReport, at the branch office is suffocating bandwidth by sending large packets for file synchronization. You need to improve the voice quality on the IP phone. Which of the following steps will you choose to accomplish this?
Which of the following is the process of categorizing attack alerts produced from an IDS in order to distinguish false positives from actual attacks?
Which of the following are not functions of the SNORT application?
Each correct answer represents a complete solution. Choose two.
Which of the following IPv6 transition technologies is used by the DirectAccess if a user is in a remote location and a public IPv4 address, instead of public IPv6 address, has been assigned to the computer?
Which of the following statements are true about UDP?
Each correct answer represents a complete solution. Choose all that apply.
You work as a technician for Tech Perfect Inc. You are troubleshooting an Internet name resolution issue. You ping your ISP's DNS server address and find that the server is down. You want to continuously ping the DNS address until you have stopped the command. Which of the following commands will you use?
Adam, an expert computer user, doubts that virus named love.exe has attacked his computer. This virus acquires hidden and read-only attributes, so it is difficult to delete it. Adam decides to delete virus file love.exe from the command line. He wants to use del command for this purpose. Which of the following switches will he use with del command to delete hidden and read only-files?
John works as a Security Administrator for NetPerfect Inc. The company uses Windows-based systems. A project has been assigned to John to track malicious hackers and to strengthen the company's security system. John configures a computer system to trick malicious hackers into thinking that it is the company's main server, which in fact is a decoy system to track hackers.
Which system is John using to track the malicious hackers?
Andrew works as an Administrator for a Windows 2000 based network. The network has a primary external DNS server, and a secondary DNS server located on the ISP's UNIX server, in order to provide fault tolerance. Users complain that they are unable to connect to the URL when using the secondary server. What should Andrew do to resolve the problem?
Sandra, an expert computer user, hears five beeps while booting her computer that has AMI BIOS; and after that her computer stops responding. Sandra knows that during booting process POST produces different beep codes for different types of errors. Which of the following errors refers to this POST beep code?
Which of the following is the primary TCP/IP protocol used to transfer text and binary files over the Internet?
John works as a professional Ethical Hacker. He has been assigned a project for testing the security of www.we-are-secure.com. He wants to corrupt an IDS signature database so that performing attacks on the server is made easy and he can observe the flaws in the We-are-secure server. To perform his task, he first of all sends a virus that continuously changes its signature to avoid detection from IDS. Since the new signature of the virus does not match the old signature, which is entered in the IDS signature database, IDS becomes unable to point out the malicious virus. Which of the following IDS evasion attacks is John performing?
An attacker wants to launch an attack on a wired Ethernet. He wants to accomplish the following tasks:
Sniff data frames on a local area network.
Modify the network traffic.
Stop the network traffic frequently.
Which of the following techniques will the attacker use to accomplish the task?
You work as a Computer Hacking Forensic Investigator for SecureNet Inc. You want to investigate Cross-Site Scripting attack on your company's Website. Which of the following methods of investigation can you use to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
Who are the primary victims of smurf attacks on the contemporary Internet system?
An IDS is a group of processes working together in a network. These processes work on different computers and devices across the network. Which of the following processes does an IDS perform?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following types of firewall functions by creating two different communications, one between the client and the firewall, and the other between the firewall and the end server?
What are the advantages of an application layer firewall?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following tools is used to store the contents of a TDB (Trivial Database) file to the standard output when debugging problems with TDB files?
Which of the following are the types of intrusion detection systems?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following types of scan does not open a full TCP connection?
Which of the following types of firewall ensures that the packets are part of the established session?
