GICSP GIAC Global Industrial Cyber Security Professional (GICSP) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC GICSP Global Industrial Cyber Security Professional (GICSP) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
For application-aware firewalls filtering traffic between trust zones, which of the following policies should be applied to a packet that doesn't match an existing rule?
What kind of data could be found on a historian?
Martin is writing a document that describes in general terms how to secure embedded operating systems. The document includes issues that are specific to embedded devices vs desktop and laptop operating systems. However, it does not call out specific flavors and versions of embedded operating systems. Which type of document is Martin writing?
What approach can an organization use to make sure that high consequence, low probability risks are considered during risk analysis?
A keyed lock on a facility's back door is an example of which type of control?
Which of the following is part of the Respond function of the NIST CSF (cybersecurity framework)?
What is a recommended practice for securing historians and databases whose purpose is to feed data back into the control processes?
What mechanism could help defeat an attacker's attempt to hide evidence of his/her actions on the target system?
An attacker writes a program that enters a large number of characters into the password field of a website, followed by a command. The website gave him administrative access, even though he did not use a valid username or password.
What is the name of this attack?
Which of the following is located in user mode of a typical realtime OS, but in kernel mode of a typical standard OS?
According to the DHS suggested patch decision tree, what should the next step be if there is a vulnerability with an available patch, but without an available workaround?
A brewer uses a local HMI to communicate with a controller that opens a pump to move the workfrom the boil kettle to the fermentor. What level of the Purdue model would the controller be considered?
Based on the following diagram, how many Active Directory domains should be created for this network?

An organization wants to use Active Directory to manage systems within its Business and Control system networks. Which of the following is the recommended security practice?
What are the last four digits of the hash created when using openssl with the md5 digest on -/GlAC/film?
Which type of process is described below?

An attacker crafts an email that will send a user to the following site if they click a link in the message. What else is necessary for this type of attack to work?
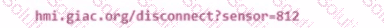
Which of the following devices would indicate an enforcement boundary?
What do the following protocols have in common?

Which resource includes a standardized categorization of common software vulnerabilities?
