GPEN GIAC Penetration Tester Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC GPEN GIAC Penetration Tester certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which of the following enables an inventor to legally enforce his right to exclude others from using his invention?
Adam works as a professional Computer Hacking Forensic Investigator. He works with the local police. A project has been assigned to him to investigate an iPod, which was seized from a student of the high school. It is suspected that the explicit child pornography contents are stored in the iPod. Adam wants to investigate the iPod extensively. Which of the following operating systems will Adam use to carry out his investigations in more extensive and elaborate manner?
The employees of CCN Inc. require remote access to the company's proxy servers. In order to provide solid wireless security, the company uses LEAP as the authentication protocol. Which of the following is supported by the LEAP protocol?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following wireless security standards supported by Windows Vista provides the highest level of security?
Which of the following are the countermeasures against WEP cracking?
Each correct answer represents a part of the solution. Choose all that apply.
Which of the following is an open source Web scanner?
Which of the following tasks is NOT performed by antiviruses?
Which of the following is a web ripping tool?
Which of the following is NOT a Back orifice plug-in?
When attempting to crack a password using Rainbow Tables, what is the output of the reduction function?
You have compromised a Windows XP system and Injected the Meterpreter payload into the lsass process. While looking over the system you notice that there is a popular password management program on the system. When you attempt to access the file that contains the password you find it is locked. Further investigation reveals that it is locked by the passmgr process. How can you use the Meterpreter to get access to this file?
Which of the following is the JavaScript variable used to store a cookie?
What section of the penetration test or ethical hacking engagement final report is used to detail and prioritize the results of your testing?
While performing an assessment on a banking site, you discover the following link:
hnps://mybank.com/xfer.aspMer_toMaccount_number]&amount-[dollars]
Assuming authenticated banking users can be lured to your web site, which crafted html tag may be used to launch a XSRF attack?
In the screen shot below, which selections would you need click in order to intercept and alter all http traffic passing through OWASP ZAP?
You have been contracted to perform a black box pen test against the Internet facing servers for a company. They want to know, with a high level of confidence, if their servers are vulnerable to external attacks. Your contract states that you can use all tools available to you to pen test the systems. What course of action would you use to generate a report with the lowest false positive rate?
Which of the following is the feature that separates the use of Rainbow Tables from other applications such as Cain or John the Ripper?
Which of the following best explains why you would warn to clear browser slate (history. cache, and cookies) between examinations of web servers when you've been trapping and altering values with a non-transparent proxy?
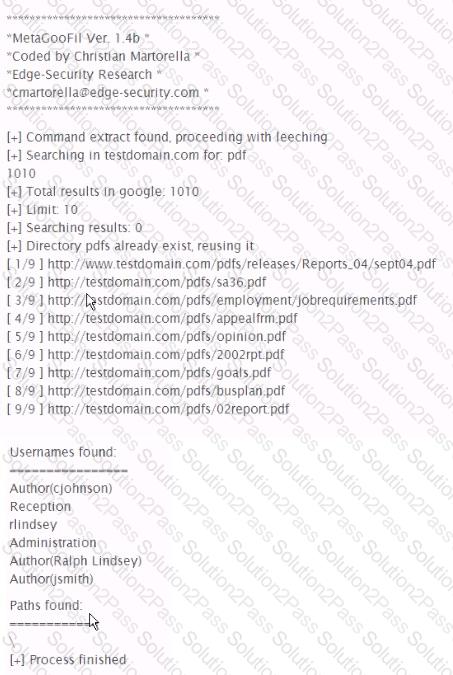
Analyze the command output below. What information can the tester infer directly from the Information shown?
You are conducting a penetration test for a private company located in Canada. The scope extends to all internal-facing hosts controlled by the company. You have gathered necessary hold-harmless and non-disclosure agreements. Which action by your group can incur criminal liability under Criminal Code of Canada Sections 184 and 542 CC 184?
