GPEN GIAC Penetration Tester Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC GPEN GIAC Penetration Tester certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which of the following is a method of gathering user names from a Linux system?
All of the following are advantages of using the Metasploitpriv module for dumping hashes from a local Windows machine EXCEPT:
When sniffing wireless frames, the interface mode plays a key role in successfully collecting traffic. Which of the mode or modes are best used for sniffing wireless traffic?
What is the purpose of the following command?
C:\>wmic /node:[target IP] /user:[admin-user]
/password:[password] process call create [command]
Identify the network activity shown below;

You are pen testing a Windows system remotely via a raw netcat shell. You want to quickly change directories to where the Windows operating system resides, what command could you use?
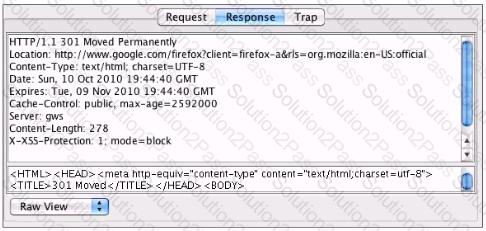
You've been asked to test a non-transparent proxy lo make sure it is working. After confirming the browser is correctly pointed at the proxy, you try to browse a web site. The browser indicates it is "loading" but never displays any part the page. Checking the proxy, you see a valid request in the proxy from your browser. Checking the response to the proxy, you see the results displayed in the accompanying screenshot. Which of the following answers is the most likely reason the browser hasn't displayed the page yet?
ACME corporation has decided to setup wireless (IEEE 802.11) network in it's sales branch at Tokyo and found that channels 1, 6, 9,11 are in use by the neighboring offices. Which is the best channel they can use?
Which Metasploit payload includes simple upload and download functionality for moving files to and from compromised systems?
What problem occurs when executing the following command from within a netcat raw shell? sudo cat /etc/shadow
Raw netcat shells and telnet terminals share which characteristic?
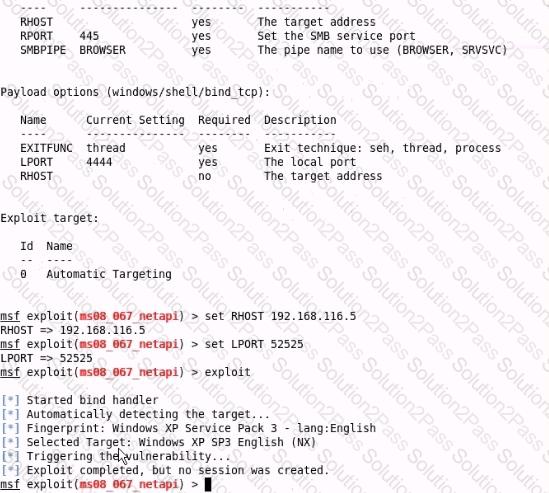
Analyze the screenshot below. What type of vulnerability is being attacked?
What is the purpose of die following command:
nc.exe -I -p 2222 -e cmd.exe
What is the main difference between LAN MAN and NTLMv1 challenge/responses?
You are performing a wireless penetration lest and are currently looking for rogue access points in one of their large facilities. You need to select an antenna that you can setup in a building and monitor the area for several days to see if any access points are turned on during the duration of the test. What type of antenna will you be selecting for this task?
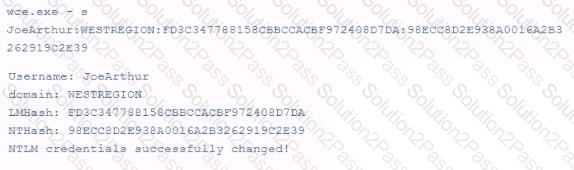
A pen tester is able to pull credential information from memory on a Windows system. Based on the command and output below, what advantage does this technique give a penetration tester when trying to access another windows system on the network?
Which of the following modes describes a wireless interface that is configured to passively grab wireless frames from one wireless channel and pass them to the operating system?
You've been contracted by the owner of a secure facility to try and break into their office in the middle of the night. Your client requested photographs of any sensitive information found as proof of your accomplishments. The job you've been hired to perform is an example of what practice?
John works as a Professional Ethical Hacker for we-are-secure Inc. The company is using a Wireless network. John has been assigned the work to check the security of WLAN of we-aresecure.
For this, he tries to capture the traffic, however, he does not find a good traffic to analyze data. He has already discovered the network using the ettercap tool. Which of the following tools can he use to generate traffic so that he can crack the Wep keys and enter into the network?
Which of the following password cracking tools can work on the Unix and Linux environment?
