GPEN GIAC Penetration Tester Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC GPEN GIAC Penetration Tester certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
You want to create a binary log file using tcpdump. Which of the following commands will you use?
You are concerned about war driving bringing hackers attention to your wireless network. What is the most basic step you can take to mitigate this risk?
You have obtained the hash below from the /etc/shadow file. What are you able to discern simply by looking at this hash?
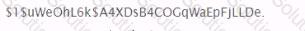
You work as a Penetration Tester for the Infosec Inc. Your company takes the projects of security auditing. Recently, your company has assigned you a project to test the security of the we-aresecure. com Website. The we-are-secure.com Web server is using Linux operating system. When you port scanned the we-are-secure.com Web server, you got that TCP port 23, 25, and 53 are open. When you tried to telnet to port 23, you got a blank screen in response. When you tried to type the dir, copy, date, del, etc. commands you got only blank spaces or underscores symbols on the screen. What may be the reason of such unwanted situation?
You are sending a file to an FTP server. The file will be broken into several pieces of information packets (segments) and will be sent to the server. The file will again be reassembled and reconstructed once the packets reach the FTP server. Which of the following information should be used to maintain the correct order of information packets during the reconstruction of the file?
Adam works as a professional Computer Hacking Forensic Investigator. He wants to investigate a suspicious email that is sent using a Microsoft Exchange server. Which of the following files will he review to accomplish the task?
Each correct answer represents a part of the solution. Choose all that apply.
You run the rdisk /s command to retrieve the backup SAM file on a computer. Where should you go on the computer to find the file?
Which of the following tools uses exploits to break into remote operating systems?
Which of the following tools can be used as a Linux vulnerability scanner that is capable of identifying operating systems and network services?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following tools is an automated tool that is used to implement SQL injections and to retrieve data from Web server databases?
John works as an Ethical Hacker for uCertify Inc. He wants to find out the ports that are open in uCertify's server using a port scanner. However, he does not want to establish a full TCP connection. Which of the following scanning techniques will he use to accomplish this task?
You execute the following netcat command:
c:\target\nc -1 -p 53 -d -e cmd.exe
What action do you want to perform by issuing the above command?
This is a Windows-based tool that is used for the detection of wireless LANs using the IEEE 802.11a, 802.11b, and 802.11g standards. The main features of these tools are as follows:
It displays the signal strength of a wireless network, MAC address, SSID, channel details, etc.
It is commonly used for the following purposes:
a. War driving
b. Detecting unauthorized access points
c. Detecting causes of interference on a WLAN
d. WEP ICV error tracking
e. Making Graphs and Alarms on 802.11 Data, including Signal Strength
This tool is known as __________.
You want to search the Apache Web server having version 2.0 using google hacking. Which of the following search queries will you use?
You work as a professional Ethical Hacker. You are assigned a project to perform blackhat testing on www.we-are-secure.com. You visit the office of we-are-secure.com as an air-condition mechanic. You claim that someone from the office called you saying that there is some fault in the air-conditioner of the server room. After some inquiries/arguments, the Security Administrator allows you to repair the air-conditioner of the server room.
When you get into the room, you found the server is Linux-based. You press the reboot button of the server after inserting knoppix Live CD in the CD drive of the server. Now, the server promptly boots backup into Knoppix. You mount the root partition of the server after replacing the root password in the /etc/shadow file with a known password hash and salt. Further, you copy the netcat tool on the server and install its startup files to create a reverse tunnel and move a shell to a remote server whenever the server is restarted. You simply restart the server, pull out the Knoppix Live CD from the server, and inform that the air-conditioner is working properly.
After completing this attack process, you create a security auditing report in which you mention various threats such as social engineering threat, boot from Live CD, etc. and suggest the countermeasures to stop booting from the external media and retrieving sensitive data. Which of the following steps have you suggested to stop booting from the external media and retrieving sensitive data with regard to the above scenario?
Each correct answer represents a complete solution. Choose two.
