GSEC GIAC Security Essentials Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC GSEC GIAC Security Essentials certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What is a limitation of deploying HIPS on a workstation?
You work as a Network Administrator for Tech Perfect Inc. The company has a Linux-based network. You want to kill a process running on a Linux server. Which of the following commands will you use to know the process identification number (PID) of the process?
You are the security director for an off-shore banking site. From a business perspective, what is a major factor to consider before running your new vulnerability scanner against the company's business systems?
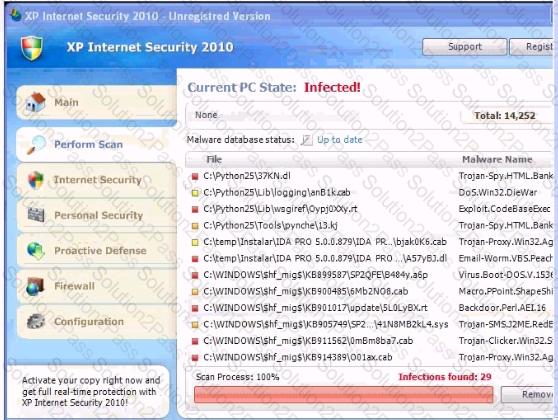
Analyze the screenshot below. What is the purpose of this message?
Which of the following applications would be BEST implemented with UDP instead of TCP?
If an attacker compromised a host on a site's internal network and wanted to trick other machines into using that host as the default gateway, which type of attack would he use?
To be considered a strong algorithm, an encryption algorithm must be which of the following?
On an NTFS file system, what will happen when a conflict exists between Allow and Deny permissions?
Which of the following commands is used to change file access permissions in Linux?
Which of the following activities would take place during the containment phase?
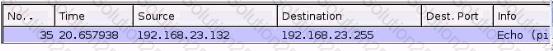
You are examining a packet capture session in Wire shark and see the packet shown in the accompanying image. Based on what you see, what is the appropriate protection against this type of attempted attack?
Many IIS servers connect to Microsoft SQL databases. Which of the following statements about SQL server security is TRUE?
Which of the following best describes the level of risk associated with using proprietary crypto algorithms.?
Which of the following groups represents the most likely source of an asset loss through the inappropriate use of computers?
Which of the following are advantages of Network Intrusion Detection Systems (NIDS)?
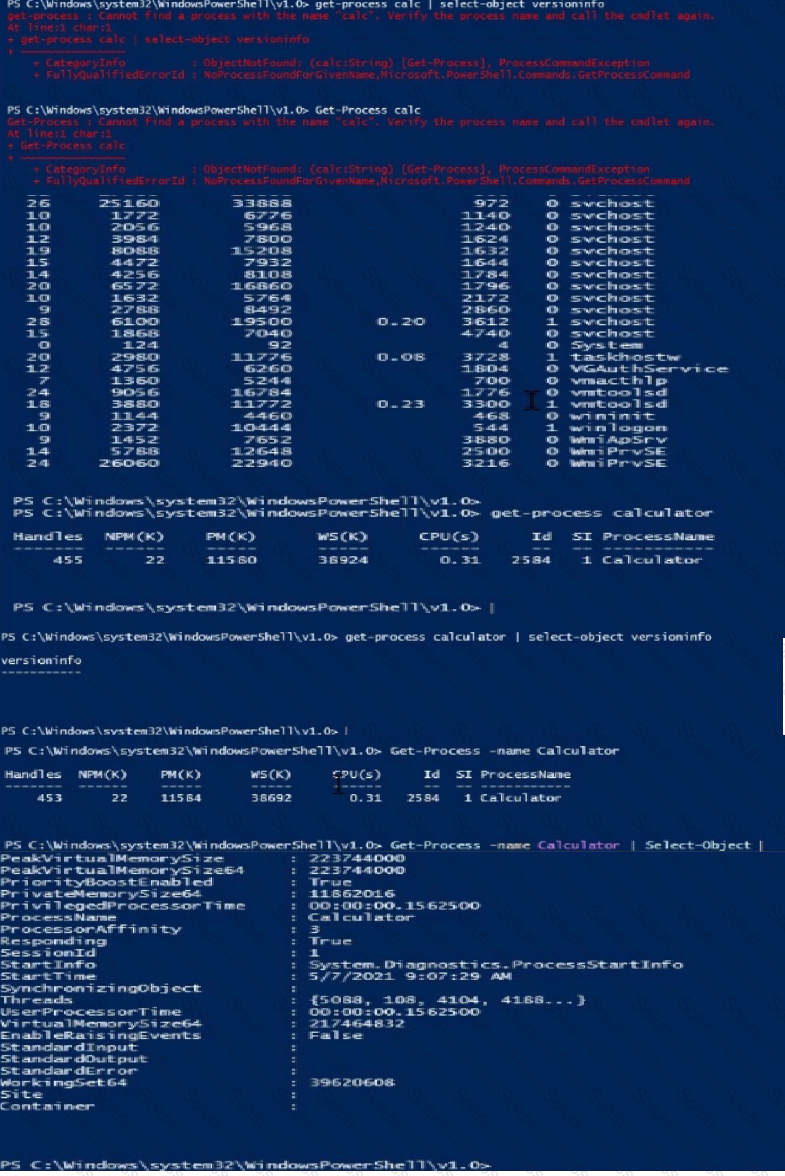
Launch Calculator (calc.exe). Using PowerShell, retrieve the Calculator Process Information. What is the value of the File Version property?
Hint: The process name of Calculator is calculator

Mark works as a Network Administrator for NetTech Inc. The company has a Windows 2003 domain- based network. The network contains ten Windows 2003 member servers, 150 Windows XP Professional client computers. According to the company's security policy, Mark needs to check whether all the computers in the network have all available security updates and shared folders. He also needs to check the file system type on each computer's hard disk. Mark installs and runs MBSACLI.EXE with the appropriate switches on a server. Which of the following tasks will he accomplish?
What is SSL primarily used to protect you against?
What type of attack can be performed against a wireless network using the tool Kismet?
What technique makes it difficult for attackers to predict the memory address space location for code execution?
