GSEC GIAC Security Essentials Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC GSEC GIAC Security Essentials certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which of the following is the FIRST step in performing an Operational Security (OP5EC) Vulnerabilities Assessment?
When an IIS filename extension is mapped, what does this mean?
What is the most secure way to address an unused Windows service so it cannot be exploited by malware?
How many clients Is a single WSUS server designed to support when the minimum system requirements are met?
What is a characteristic of iOS security?
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. John is working as a root user on the Linux operating system. He is currently working on his C based new traceroute program. Since, many processes are running together on the system, he wants to give the highest priority to the cc command process so that he can test his program, remove bugs, and submit it to the office in time. Which of the following commands will John use to give the highest priority to the cc command process?
What would the following IP tables command do?
IP tables -I INPUT -s 99.23.45.1/32 -j DROP
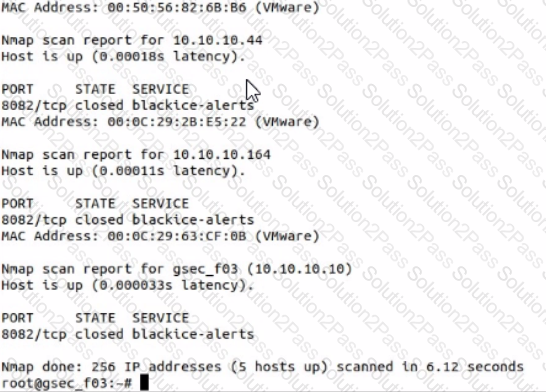
Use nmap to discover a host on the 10.10.10.0/24 network, scanning only port 8082 and using the SYN or Stealth scan approach. Which host has a service called -blackice-alerts"?

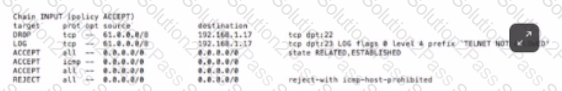
Based on the iptables output below, which type of endpoint security protection has host 192.168.1.17 implemented for incoming traffic on TCP port 22 (SSH) and TCP port 23 (telnet)?
When designing wireless networks, one strategy to consider is implementing security mechanisms at all layers of the OSI model. Which of the following protection mechanisms would protect layer 1?
What is TRUE about Workgroups and Domain Controllers?
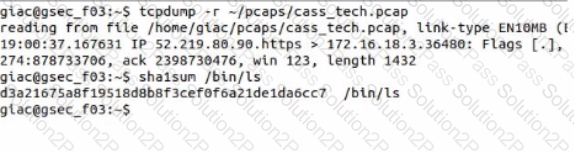
What is the SHA1 hash of the Ale /bin/Is?

Included below is the output from a resource kit utility run against local host.
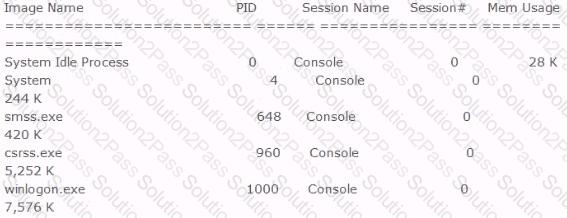
Which command could have produced this output?
Which of the following is a term that refers to unsolicited e-mails sent to a large number of e-mail users?
What is the name of the Windows XP/2003 tool that you can use to schedule commands to be executed on remote systems during off-peak hours?
What is the name of the registry key that is used to manage remote registry share permissions for the whole registry?
What dots Office 365 use natively for authentication?
Which of the following tools is used to query the DNS servers to get detailed information about IP addresses, MX records, and NS servers?
You work as a Network Administrator for McNeil Inc. The company has a Windows Server 2008 network environment. The network is configured as a Windows Active Directory-based single forest domain-based network. The company's management has decided to provide laptops to its sales team members. These laptops are equipped with smart card readers. The laptops will be configured as wireless network clients. You are required to accomplish the following tasks:
The wireless network communication should be secured.
The laptop users should be able to use smart cards for getting authenticated. In order to accomplish the tasks, you take the following steps:
Configure 802.1x and WEP for the wireless connections. Configure the PEAP-MS-CHAP v2 protocol for authentication. What will happen after you have taken these steps?
In a /24 subnet, which of the following is a valid broadcast address?
