GSEC GIAC Security Essentials Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC GSEC GIAC Security Essentials certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
The TTL can be found in which protocol header?
Which of the following is NOT typically used to mitigate the war dialing threat?
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. John is working as a root user on the Linux operating system. He wants to change the modified date and time of the file private.txt to 11 Nov 2009 02:59:58 am. Which of the following commands will John use to accomplish his task?
Each correct answer represents a complete solution. Choose all that apply.
The Windows 'tracert' begins by sending what type of packet to the destination host?
You work as a Network Administrator for Rick International. The company has a TCP/IP-based network. A user named Kevin wants to set an SSH terminal at home to connect to the company's network. You have to configure your company's router for it. By default, which of the following standard ports does the SSH protocol use for connection?
Which of the following protocols are used to provide secure communication between a client and a server over the Internet?
Each correct answer represents a part of the solution. Choose two.
A security analyst has entered the following rule to detect malicious web traffic:
alert tcp any -> 192.168.1.0/24 SO (msg: Attempted SQL Injection!"; sld:20000O01;)
How can this rule be changed to reduce false positives?
What Windows log should be checked to troubleshoot a Windows service that is falling to start?
You work as a Network Administrator for NetTech Inc. To ensure the security of files, you encrypt data files using Encrypting File System (EFS).
You want to make a backup copy of the files and maintain security settings. You can backup the files either to a network share or a floppy disk. What will you do to accomplish this?
What technical control provides the most critical layer of defense if an intruder is able to bypass all physical security controls and obtain tapes containing critical data?
Fill in the blank with the correct answer to complete the statement below.
The permission is the minimum required permission that is necessary for a user to enter a directory and list its contents.
A Windows administrator wants to automate local and remote management tasks in Active Directory. Which tool is most appropriate for this?
A new data center is being built where customer credit information will be processed and stored. Which of the following actions will help maintain the confidentiality of the data?
Which of the following statements about Microsoft's VPN client software is FALSE?
Which of the following is an advantage of an Intrusion Detection System?
Which of the following statements about Secure Sockets Layer (SSL) are true? Each correct answer represents a complete solution. Choose two.
Which of the following is a private, RFC 1918 compliant IP address that would be assigned to a DHCP scope on a private LAN?
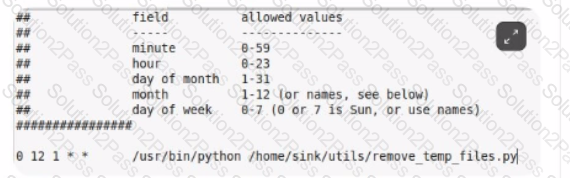
Analyze the file below. When will the program /home/sink/utils/remove temp hies.py run?
Which of the following tools is used to configure, control, and query the TCP/IP network interface parameters?
Which of the following protocols describes the operation of security In H.323?
