GSLC GIAC Security Leadership Certification (GSLC) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC GSLC GIAC Security Leadership Certification (GSLC) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
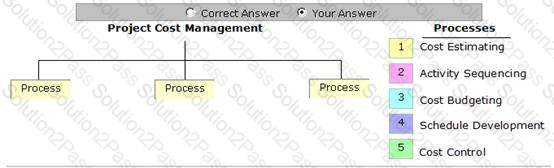
Place the processes that are grouped under the Project Cost Management Knowledge Area in the image below.

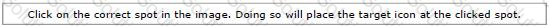
You work as a Security manager for Caterxiss Inc. The headquarters of your company is connected to the branch office in another state and a service partner in the same state. The network of the company is being attacked from the connected networks. You decide to analyze and then prevent the corporate headquarters network from these attacks using a Snort IDS.
What is the most appropriate spot on the network where you should set up an Intrusion detection system (IDS)?
Which of the following are outputs of the Direct and Manage Project Execution process?
Each correct answer represents a complete solution. Choose all that apply.
Mark works as a Network Administrator for We-are-secure Inc. He finds that the We-are-secure server has been infected with a virus. He presents to the company a report that describes the symptoms of the virus. A summary of the report is given below:
This virus has a dual payload, as the first payload of the virus changes the first megabyte of the hard drive to zero. Due to this, the contents of the partition tables are deleted and the computer hangs.
The second payload replaces the code of the flash BIOS with garbage values. This virus spreads under the Portable Executable File Format under Windows 95, Windows 98, and Windows ME.
Which of the following viruses has the symptoms as the one described above?
Which of the following functions can you use to mitigate a command injection attack?
Each correct answer represents a complete solution. Choose all that apply.
Your company network has been infected with a virus. You have cleaned all PCs, workstations, and servers. However your network still keeps getting re-infected with the same virus. Which of the following could NOT be a cause for this?
Each correct answer represents a complete solution. Choose two.
Which of the following attacks does Management Frame Protection help to mitigate?
Each correct answer represents a complete solution. Choose two.
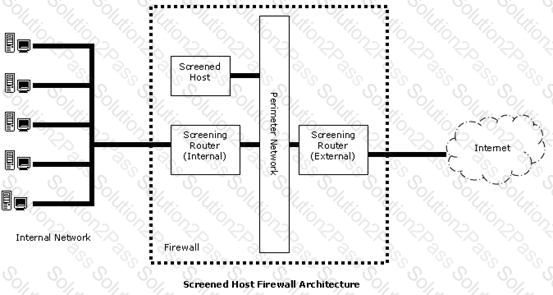
In the image of the Screened Host Firewall Architecture given below, select the element that is commonly known as the access router.
Which of the following types of attacks occurs when an attacker successfully inserts an intermediary software or program between two communicating hosts?
You are writing the change management plan for your upcoming project. You want to address mistakes that could happen during the execution of the project. Your change management plan requires the project team to correct any errors that deviate from the project scope as an error is technically an unapproved scope change. What else should you address in regard to errors in project team execution?
You work as a Network Administrator for Infosec Inc. Nowadays, you are facing an unauthorized access in your Wi-Fi network. Therefore, you analyze a log that has been recorded by your favorite sniffer, Ethereal. You are able to discover the cause of the unauthorized access after noticing the following string in the log file:
(Wlan.fc.type_subtype eq 32 and llc.oui eq 0x00601d and llc.pid eq 0x0001)
When you find All your 802.11b are belong to us as the payload string, you are convinced about which tool is being used for the unauthorized access. Which of the following tools have you ascertained?
Which of the following protocols provides mail forwarding and information storing features?
Victor works as a professional Ethical Hacker for SecureNet Inc. He wants to use the Steganographic file system method to encrypt and hide some secret information. Which of the following disk spaces will he use to store this secret information?
Each correct answer represents a complete solution. Choose all that apply.
You are responsible for the security computers in college labs. Since a number of students have significant computer skills, you wish to make security impossible to breach through normal operating system based means. Furthermore, you want to have the security require a password that must be entered before the operating system even loads. What will you do to accomplish the task?
Which of the following processes is described in the statement below?
"This is the process of numerically analyzing the effect of identified risks on overall project objectives."
Which of the following statements are true about an application-level gateway?
Each correct answer represents a complete solution. Choose all that apply.
PassGuide Research and Training Center is developing its new network model. Which of the following protocols should be implemented in the new network? (Click the Exhibit button on the toolbar to see the case study.) Each correct answer represents a complete solution. Choose two.
John is a malicious attacker. He illegally accesses the server of We-are-secure Inc. He then places a backdoor in the We-are-secure server and alters its log files. Which of the following steps of malicious hacking includes altering the server log files?
You are working in a functional organization and are managing the IHH Project. Your project will likely last for six months and has a budget constraint of $1,876,000. You'll be dealing with a functional manager to manage costs and resources in the project. Who will have authority over assigning the project team members to activities?
PsPasswd is a tool used by network administrators to change an account password on the local or remote system. Which of the following are the command syntaxes used by the PsPasswd tool?
Each correct answer represents a complete solution. Choose all that apply.
Maria works as a Risk Analysis Manager for Gentech Inc. She starts a new IT project. Which of the following phases of her project development process is most suitable for including risk analysis?
Which of the following is an example of penetration testing?
The Project Scope Management knowledge area focuses on which of the following processes?
Each correct answer represents a complete solution. Choose all that apply.
In which of the following social engineering attacks does an attacker first damage any part of the target's equipment and then advertise himself as an authorized person who can help fix the problem.
Which of the following wireless security standards supported by Windows Vista provides the highest level of security?
Which of the following encryption modes are possible in WEP?
Each correct answer represents a complete solution. Choose all that apply.
You are the project manager of the HQQ Project for your company. You are working with your project stakeholders to discuss the risks in the project that can adversely affect the project objectives. You are discussing the possibilities of causes for an identified risk event in your project. Your stakeholder is confused on the difference between causes and risk events. Which of the following is NOT an example of a cause for a project risk?
Which of the following are the automated tools that are used to perform penetration testing?
Each correct answer represents a complete solution. Choose two.
Which of the following types of authentication is generally used for public Internet Web sites?
Which of the following methods will allow data to be sent on the Internet in a secure format?
