GSLC GIAC Security Leadership Certification (GSLC) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC GSLC GIAC Security Leadership Certification (GSLC) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
GSM uses either A5/1 or A5/2 stream cipher for ensuring over-the-air voice privacy. Which of the following cryptographic attacks can be used to break both ciphers?
Which of the following characteristics are related to biometrics?
Each correct answer represents a complete solution. Choose two.
Which of the following methods can be helpful to eliminate social engineering threat?
Each correct answer represents a complete solution. Choose three.
You are concerned about possible hackers doing penetration testing on your network as a prelude to an attack. What would be most helpful to you in finding out if this is occurring?
You are a Web Administrator of Millennium Inc. The company has hosted its Web site within its network. The management wants the company's vendors to be able to connect to the corporate site from their locations through the Internet. As a public network is involved in this process, you are concerned about the security of data transmitted between the vendors and the corporate site. Which of the following can help you?
Mark works as a Network Administrator for NetTech Inc. The company has a Windows Server 2008 domain based network. The network contains four Windows Server 2008 member servers with different roles and 120 Windows Vista client computers. Mark has implemented a Streaming Media Services server on the network. Users complain that they are unable to view the contents when using their Windows Media Players. Mark investigates and finds that the firewall only allows ports 80 and 443 for traffic. Mark wants to ensure that the users can view the contents. What will Mark to do to accomplish the task?
A helpdesk technician received a phone call from an administrator at a remote branch office. The administrator claimed to have forgotten the password for the root account on UNIX servers and asked for it. Although the technician didn't know any administrator at the branch office, the guy sounded really friendly and since he knew the root password himself, he supplied the caller with the password.
What type of attack has just occurred?
You are a project manager who is completing a project for another organization. The project you are managing will have phased deliverables throughout the project. Stakeholders are required to complete scope validation at the end of each phase so that the project can move forward. Your payment requests will also be attached to the approval of each phase so it is important to you, on several levels, that the stakeholders participate in scope validation as soon as they are requested. You have documented the process for reviewing the product acceptance criteria with the stakeholders.
What project document details the product acceptance criteria in all the projects?
These are false reports about non-existent viruses. In these reports, the writer often claims to do impossible things. Due to these false reports, the network administrator shuts down his network, which in turn affects the work of the company. These reports falsely claim to describe an extremely dangerous virus, and declare that the report is issued by a reputed company. These reports are known as __________.
Which of the following techniques is based on a set of criteria that has been acquired in a specific knowledge area or product area?
You work as a Network Administrator for Tech Perfect Inc. The company has a Windows Active Directory-based single domain single forest network. The functional level of the forest is Windows Server 2003. The company has recently provided fifty laptops to its sales team members. You are required to configure an 802.11 wireless network for the laptops. The sales team members must be able to use their data placed at a server in a cabled network. The planned network should be able to handle the threat of unauthorized access and data interception by an unauthorized user. You are also required to prevent the sales team members from communicating directly to one another. Which of the following actions will you take to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He is using a tool to crack the wireless encryption keys. The description of the tool is as follows:
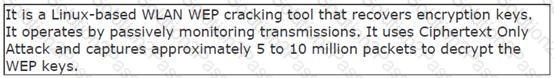
Which of the following tools is John using to crack the wireless encryption keys?
You work as a Network Administrator for PassGuide Inc. You have been assigned a task to provide the right authentications to users. Which method that uses a KDC will you use to accomplish the task?
Your Company is receiving false and abusive e-mails from the e-mail address of your partner company. When you complain, the partner company tells you that they have never sent any such e-mails. Which of the following types of cyber crimes involves this form of network attack?
You work as a Network Administrator for Net World Inc. The company has a Windows Active Directory-based single domain single forest network. The functional level of the forest is Windows Server 2003. A Public Key Infrastructure (PKI) is installed on a server in the domain. You are planning to go on vacation for two weeks. Your team has three assistant administrators. You are required to accomplish the following tasks:
• Delegate the authority to the assistant administrators to issue, approve, and revoke certificates.
• The solution must involve least administrative burden.
Which of the following steps will you take to accomplish the tasks?
Which of the following evidences are the collection of facts that, when considered together, can be used to infer a conclusion about the malicious activity/person?
Which type of virus is able to alter its own code to avoid being detected by anti-virus software?
Which of the following processes is described in the statement below?
"It is the process of implementing risk response plans, tracking identified risks, monitoring residual risk, identifying new risks, and evaluating risk process effectiveness throughout the project."
This is a Windows-based tool that is used for the detection of wireless LANs using the IEEE 802.11a, 802.11b, and 802.11g standards. The main features of these tools are as follows:
• It displays the signal strength of a wireless network, MAC address, SSID, channel details, etc.
• It is commonly used for the following purposes:
a. War driving
b. Detecting unauthorized access points
c. Detecting causes of interference on a WLAN
d. WEP ICV error tracking
e. Making Graphs and Alarms on 802.11 Data, including Signal Strength
This tool is known as __________.
You are working on your computer system with Linux Operating system. After working for a few hours, the hard disk goes to the inactive state (sleep). You try to restart the system and check the power circuits. You later discover that the hard disk has crashed. Which of the following precaution methods should you apply to keep your computer safe from such issues?
Victor works as a professional Ethical Hacker for SecureEnet Inc. He wants to scan the wireless network of the company. He uses a tool that is a free open-source utility for network exploration.
The tool uses raw IP packets to determine the following:
• What ports are open on our network systems
• What hosts are available on the network
• Identify unauthorized wireless access points
• What services (application name and version) those hosts are offering
• What operating systems (and OS versions) they are running
• What type of packet filters/firewalls are in use
Which of the following tools is Victor using?
A sequence number is a 32-bit number ranging from 1 to 4,294,967,295. When data is sent over the network, it is broken into fragments (packets) at the source and reassembled at the destination system. Each packet contains a sequence number that is used by the destination system to reassemble the data packets in the correct order. The Initial Sequence Number of your computer is 24171311 at login time. You connect your computer to a computer having the IP address 210.213.23.21. This whole process takes three seconds. What will the value of the Initial Sequence Number be at this moment?
An Active Attack is a type of steganography attack in which the attacker changes the carrier during the communication process. Which of the following techniques is used for smoothing the transition and controlling contrast on the hard edges, where there is significant color transition?
Which of the following attacks is any form of cryptanalysis where the attacker can observe the operation of a cipher under several different keys whose values are initially unknown, but where some mathematical relationship connecting the keys is known to the attacker?
You have been hired as a project manager for a project. The initial project planning predicts a benefitcost ratio (BCR) of the project as 3.5. What does this figure mean?
Internet Protocol Security (IPSec) provides data protection during network communication. Which of the following tasks can be performed by IPSec?
Each correct answer represents a complete solution. Choose all that apply.
You are the project manager of the Workstation Improvement Project for your organization. This project will replace 925 workstations with new computers for your company's employees. Mark Jones, the sales manager, has requested that your project add 250 laptops as part of this project as his employees do not have workstations as they travel as part of the sales process. Mark insists that his department in the company can pay for the cost of the laptops. All of the following are components that will be affected by this change request except for which one?
You work as a Network Administrator for Infonet Inc. The company has a Windows Server 2008 domain-based network. The network has three Windows Server 2008 member servers and 150 Windows Vista client computers. The network contains a Windows Server 2008 Core computer named SERVER1 with NTFS file system. SERVER1 has a 802.11 wireless LAN adapter. The Wireless LAN Service is installed on SERVER1. You want to know about the 802.11 wireless LAN interface information, network information, and wireless settings on the system on SERVER1.
Which of the following commands will you use to accomplish the task?
Which of the following terms describes the statement given below?
"It is a service on a computer system (usually a server) that delays incoming connections for as long as possible. The technique was developed as a defense against a computer worm, and the idea is that network abuses, such as spamming or broad scanning, are less effective if they take too long."
Which of the following firewalls inspects the actual contents of packets?
