HCVA0-003 HashiCorp Certified: Vault Associate (003)Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your HashiCorp HCVA0-003 HashiCorp Certified: Vault Associate (003)Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which statement best describes the process of sealing a Vault instance?
Compared to service tokens, batch tokens are ideal for what type of action?
Which of the following statements best describes the difference between static and dynamic credentials in a secrets management system?
What is the result of the following Vault command?
$ vault auth enable kubernetes
Which auth method is ideal for machine-to-machine authentication?
Which of the following auth methods is the best choice for human interaction with Vault (as opposed to machine/system authentication)?
Beyond encryption and decryption of data, which of the following is not a function of the Transit secrets engine?
Which statement most accurately describes how the response wrapping feature functions in Vault?
Which of the following statements are true about HCP Vault Dedicated? (Select three)
You need to write a Vault operator policy and give the users access to perform administrative actions in Vault. What path is used for Vault backend functions?
When Vault is sealed, which are the only two operations available to a Vault administrator? (Select two)
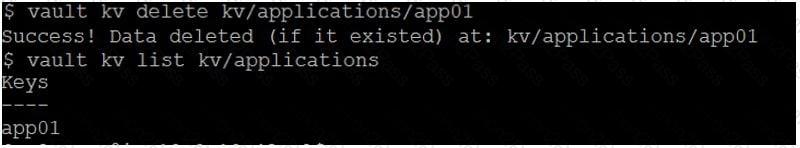
After issuing the command to delete a secret, you run a vault kv list command, but the path to the secret still seems to exist. What command would permanently delete the path from Vault?
Which of the following statements best describes the difference in cluster strategies between self-managed Vault and HashiCorp-managed Vault?
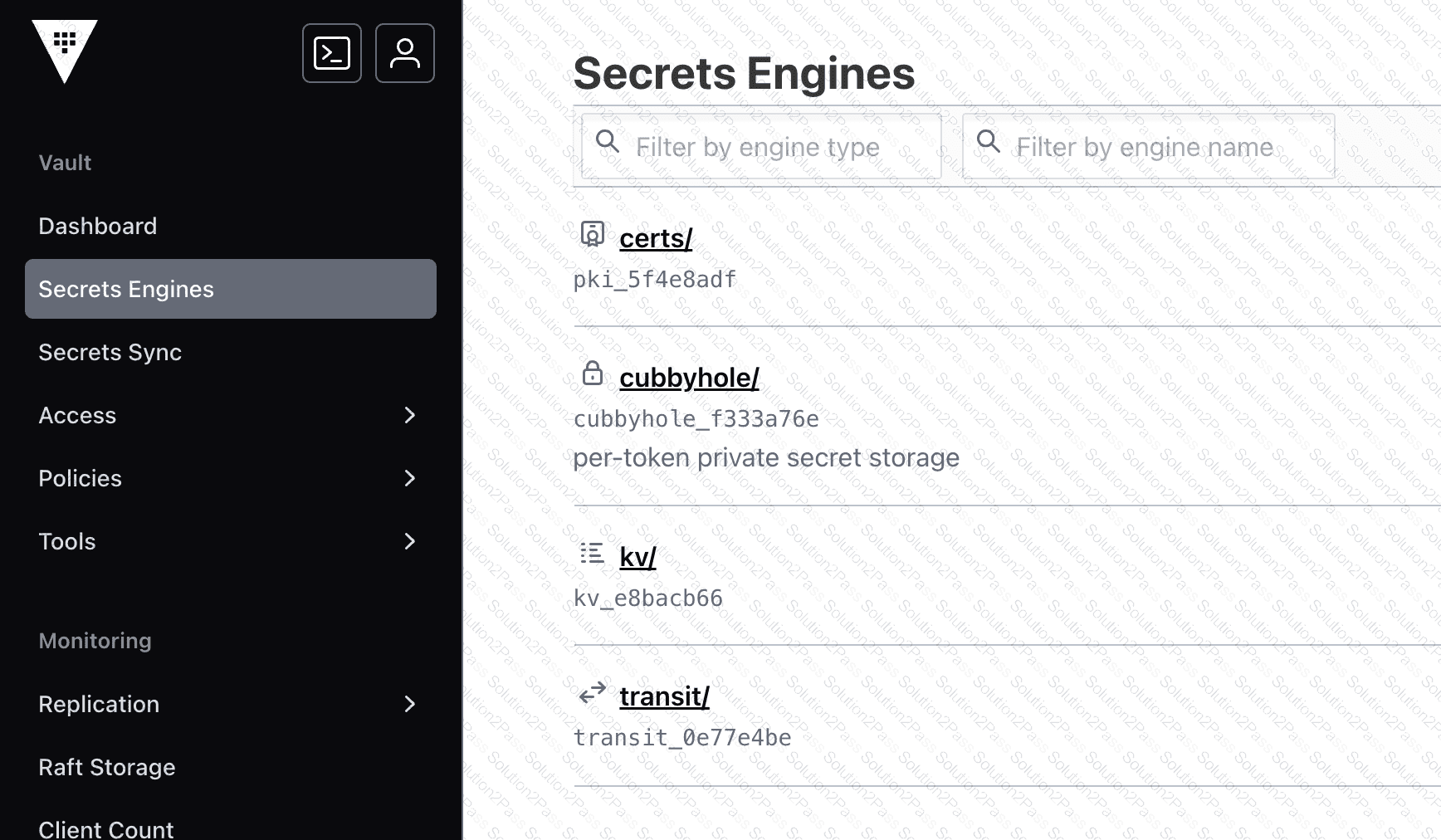
Given the following screenshot, how many secrets engines have been enabled by a Vault user?
According to the screenshot below, what auth method did this client use to log in to Vault?
(Screenshot shows a lease path: auth/userpass/login/student01)
From the options below, select the benefits of using a batch token over a service token (select four).
How does the Vault Secrets Operator (VSO) assist in integrating Kubernetes-based workloads with Vault?
True or False? Once you create a KV v1 secrets engine and place data in it, there is no way to modify the mount to include the features of a KV v2 secrets engine.
From the unseal options listed below, select the options you can use if you're deploying Vault on-premises (select four).
By default, what TCP port does Vault replication use?
