HCVA0-003 HashiCorp Certified: Vault Associate (003)Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your HashiCorp HCVA0-003 HashiCorp Certified: Vault Associate (003)Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
After encrypting data using the Transit secrets engine, you’ve received the following output. Which of the following is true based on the output displayed below?
Key: ciphertext Value: vault:v2:45f9zW6cglbrzCjI0yCyC6DBYtSBSxnMgUn9B5aHcGEit71xefPEmmjMbrk3
What command would have created the token displayed below?
$ vault token lookup hvs.nNeZ2I64ALCxuO7dqQEJGPrO
Key: policies Value: [default dev], num_uses: 5, ttl: 767h59m49s
Key Value
--- -----
accessor mfvaVMFgOcXHIeqlRasroSOn
creation_time 1604610457
creation_ttl 768h
display_name token
entity_id n/a
expire_time 2024-12-07T16:07:37.7540672-05:00
explicit_max_ttl 0s
id hvs.nNeZ2I64ALCxuO7dqQEJGPrO
issue_time 2024-11-05T16:07:37.7540672-05:00
meta
num_uses 5
orphan false
path auth/token/create
policies [default dev]
renewable true
ttl 767h59m49s
type service
Which of the following are accurate statements regarding the use of a KV v2 secrets engine (select three)?
What are the primary benefits of running Vault in a production deployment over dev server mode (select two)?
True or False? When using the Transit secrets engine, setting the min_decryption_version will determine the minimum key length of the data key (i.e., 2048, 4096, etc.).
How can Vault be used to programmatically obtain a generated code for MFA, somewhat similar to Google Authenticator?
A Jenkins server is using the following token to access Vault. Based on the lookup shown below, what type of token is this?$ vault token lookup hvs.FGP1A77Hxa1Sp6Pkp1yURcZB
Key Value
--- -----
accessor RnH8jtgrxBrYanizlyJ7Y8R
creation_time 1604604512
creation_ttl 24h
display_name token
entity_id n/a
expire_time 2025-11-06T14:28:32.8891566-05:00
explicit_max_ttl 0s
id hvs.FGP1A77Hxa1Sp6KRau5eNB
issue_time 2025-11-06T14:28:32.8891566-05:00
meta
num_uses 0
orphan false
path auth/token/create
period 24h
policies [admin default]
renewable true
ttl 23h59m50s
type service
Jason has enabled the userpass auth method at the path users/. What path would Jason and other Vault operators use to interact with this new auth method?
Running the second command in the GUI CLI will succeed.
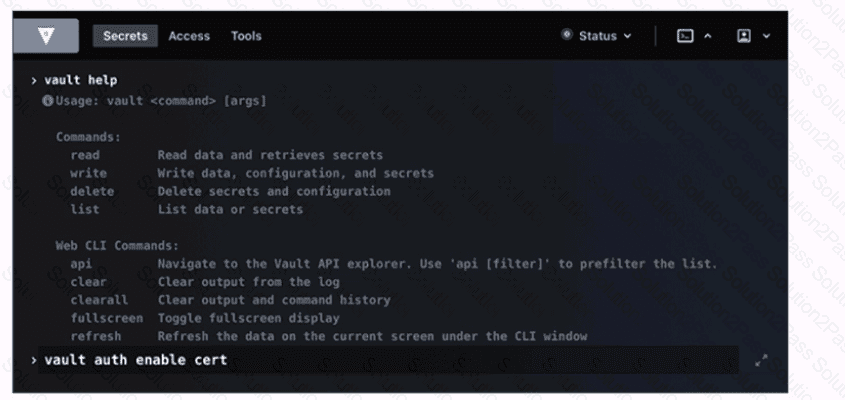
Your organization has an initiative to reduce and ultimately remove the use of long lived X.509 certificates. Which secrets engine will best support this use case?
When using Integrated Storage, which of the following should you do to recover from possible data loss?
Which of the following describes the Vault's auth method component?
Use this screenshot to answer the question below:
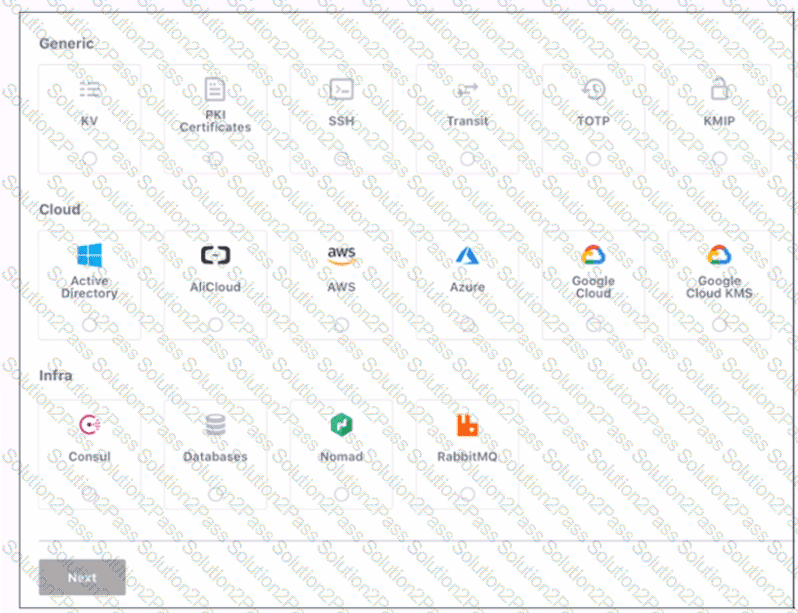
When are you shown these options in the GUI?
The Vault encryption key is stored in Vault's backend storage.
An organization wants to authenticate an AWS EC2 virtual machine with Vault to access a dynamic database secret. The only authentication method which they can use in this case is AWS.
Which of the following statements describe the CLI command below?
S vault login -method-1dap username-mitche11h
The following three policies exist in Vault. What do these policies allow an organization to do?

What environment variable overrides the CLI's default Vault server address?
Use this screenshot to answer the question below:
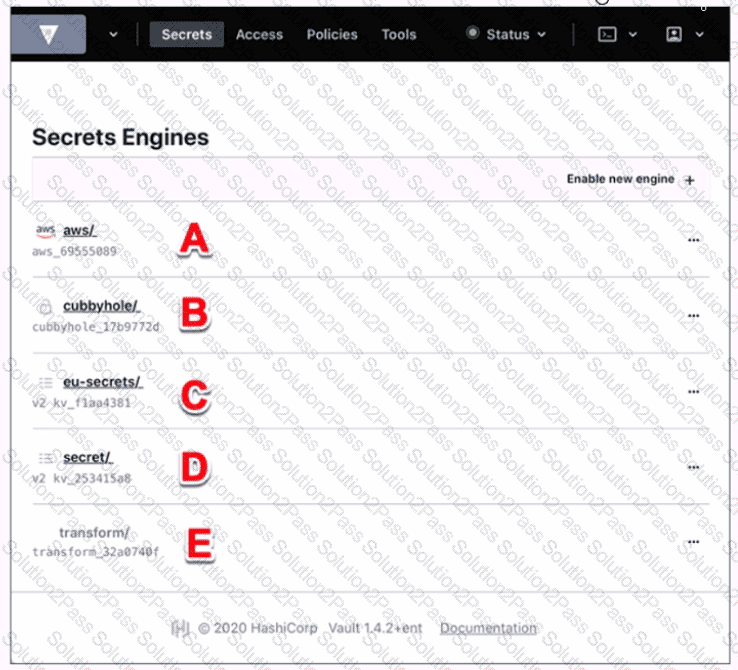
Where on this page would you click to view a secret located at secret/my-secret?
A user issues the following cURL command to encrypt data using the transit engine and the Vault AP:
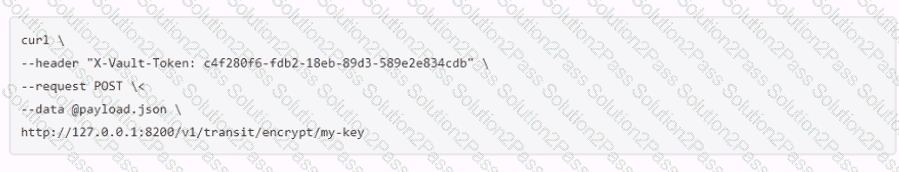
Which payload.json file has the correct contents?
 A white background with black text
AI-generated content may be incorrect.
A white background with black text
AI-generated content may be incorrect.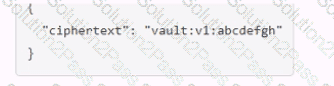 A white background with black text
AI-generated content may be incorrect.
A white background with black text
AI-generated content may be incorrect.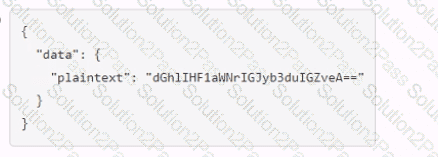 A white background with black text
AI-generated content may be incorrect.
A white background with black text
AI-generated content may be incorrect.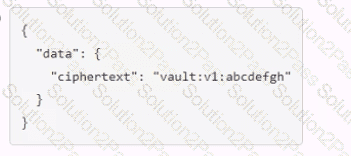 A computer code with black text
AI-generated content may be incorrect.
A computer code with black text
AI-generated content may be incorrect.