H12-721 Huawei Certified ICT Professional - Constructing Infrastructure of Security Network Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Huawei H12-721 Huawei Certified ICT Professional - Constructing Infrastructure of Security Network certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
In the firewall DDoS attack defense technology, the Anti-DDoS device adopts seven layers of defense technology, and the description based on session defense is correct?
SSL works at the application layer and encrypts specific applications. Which layer does IPSec work on and provides transparent encryption protection for this layer and above?
When an IPSec VPN is set up on both ends of the firewall, the security ACL rules of both ends are mirrored.
What are the correct statements about the IP address scanning attack and prevention principles?
The firewall device defends against the SYN Flood attack by using the technology of source legality verification. The device receives the SYN packet and sends the SYN-ACK probe packet to the source IP address host in the SYN packet. If the host exists, it will Which message is sent?
The following are traffic-type attacks.
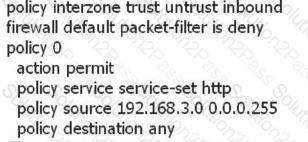
The PC A in the Trust zone is 192.168.3.1. You cannot access the Internet server in the Untrust zone. The configuration between the Trust zone and the Untrust zone is as follows. What are the most likely causes of the following faults?
Which of the following statements is true for virtual service technology?
The server health check mechanism is enabled on the USG firewall of an enterprise to detect the running status of the back-end real server (the three servers are Server A, Server B, and Server C). When the USG fails to receive the response from Server B multiple times. When the message is received, Server B will be disabled and the traffic will be distributed to other servers according to the configured policy.
The dual-system hot backup load balancing service interface works at Layer 3, and the upstream and downstream routers are connected to each other. The two USG devices are active and standby. Therefore, both the hrp track master and the hrp track slave must be configured on the morning service interface.
The load balancing function is configured on the USG firewall for three FTP servers. The IP addresses and weights of the three physical servers are 10.1.13/24 (weight 16); 10.1.1.4/24 (weight 32); 10.1.1.5 /24 (weight 16), and the virtual server address is 202.152.26.123/24. A PC with the host address of 202.152.26.3/24 initiates access to the FTP server. Run the display firewall session table command on the firewall to check the configuration. Which of the following conditions indicates that the load balancing function is successfully implemented?
When using the SSL VPN client to start the network extension, the prompt "Connection gateway failed", what are the possible reasons for the failure?
For IP-MAC address binding, packets with matching IP and MAC address will enter the next processing flow of the firewall. Packets that do not match IP and MAC address will be discarded.
When configuring the USG hot standby, (assuming the backup group number is 1), the configuration command of the virtual address is correct?
Which of the following does the virtual firewall technical feature not include?
If the IPSec policy is configured in the policy template and sub-policy mode, the firewall applies the policy template first and then applies the sub-policy.
The following figure shows the L2TP over IPSec application scenario. The client uses the pre-shared-key command to perform IPSec authentication. How should the IPSec security policy be configured on the LNS?
The ACK flood attack is defended by the load check. The principle is that the cleaning device checks the payload of the ACK packet. If the payloads are all consistent (if the payload content is all 1), the packet is discarded.
The administrator can create vfw1 and vfw2 on the root firewall to provide secure multi-instance services for enterprise A and enterprise B, and configure secure forwarding policies between security zones of vfw1 and vfw2.
DDoS is an abnormal packet that an attacker sends a small amount of non-traffic traffic to the attack target (usually a server, such as DNS or WEB) through the network, so that the attacked server resolves the packet when the system crashes or the system is busy.
