H12-721 Huawei Certified ICT Professional - Constructing Infrastructure of Security Network Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Huawei H12-721 Huawei Certified ICT Professional - Constructing Infrastructure of Security Network certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What is the correct statement about the Eth-trunk function?
Static fingerprint filtering function, different processing methods for different messages, the following statement is correct?
In the hot standby scenario, what is the correct statement about the primary and backup backups?
A network is as follows: The l2tp vpn is established through the VPN Client and the USG (LNS). What are the reasons for the dialup failure?
In the USG firewall, which two commands can be used to view the running status and memory/CPU usage of the device components (main control board, board, fan, power supply, etc.)?
71. Which option is incorrect about the HTTP Flood defense principle?
Which of the following statements is true about L2TP over IPSec VPN?
Using the virtual firewall technology, users on the two VPNs can log in to their private VPNs through the Root VFW on the public network to directly access private network resources. What are the following statements about the characteristics of the VPN multi-instance service provided by the firewall?
Which of the following statements is correct about the IKE main mode and the aggressive mode?
Defense against the cache server The main method of DNS request flood is to use the DNS source authentication technology:
What are the correct descriptions of IPSec and IKE below?
Which of the following security services can a secure multi-instance provide for a virtual firewall?
Which is the correct packet encapsulation order for L2TP over IPSec?
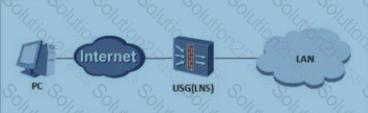
An administrator can view the IPSec status information and Debug information as follows. What is the most likely fault?
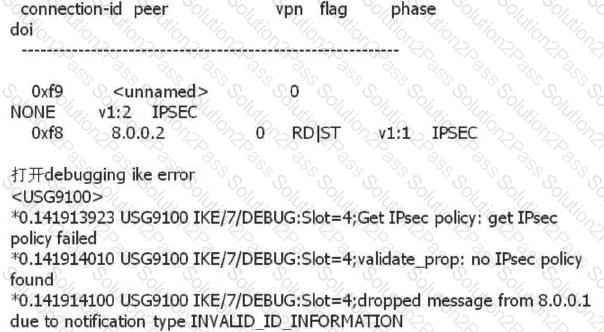
As shown in the following figure, the BFD for OSPF network is as follows: 1. OSPF is running between the three devices: FW_A, FW_B, and FW_C. The neighbors are in the FULL state. The association between BFD and OSPF is complete. BFD is complete. To establish a BFD session, the following instructions are correct?
What are the following attacks that are malformed?
What is the correct statement about the binding of local users to VPN instances?
Which attack method is CC attack?
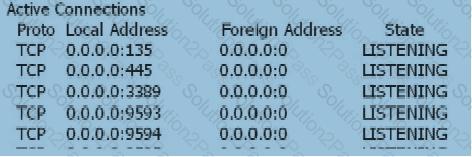
When the user's SSL VPN has been successfully authenticated, the user cannot access the Web-link resource. On the Web server, view the information as follows: netstat -anp tcp With the following information, which of the following statements is correct?
Comparing URPF strict mode and loose mode, which of the following statements is incorrect?
