H12-722_V3.0 Huawei HCIP-Security-CSSN V3.0 Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Huawei H12-722_V3.0 HCIP-Security-CSSN V3.0 certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What content can be filtered by the content filtering technology of Huawei USG6000 products? (multiple choice)
Huawei USG6000 products can scan and process certain file transfer protocols for viruses, but which of the following protocols is not included?
Which of the following are typical intrusions? "Multiple choice)
SQI Server2005 may not be properly installed, which of the following may be the possible reasons?
With the continuous development of the network and the rapid development of applications, companies are making users more and more frequently start to transfer files on the network.
Virus threats are becoming more and more serious. Only by rejecting the virus outside the network can data security and system stability be guaranteed. So, which of the following are
What harm might be caused by illness? (multiple choices)
Regarding the sequence of the mail transmission process, which of the following is correct?
1. The sender PC sends the mail to the designated SMTP Server.
2. The sender SMTP Server encapsulates the mail information in an SMTP message and sends it to the receiver SMTP Server according to the destination address of the mail
3. The sender SMTP Server encapsulates the mail information in an SMTP message according to the destination address of the mail and sends it to the receiver POP3/MAP Senver
4. The recipient sends an email.
Which of the following options is not a special message attack?
In the Huawei USG6000 product, after creating or modifying the security configuration file, the configuration content will not take effect immediately: you need to click the "Prompt" in the upper right corner of the interface.
"Hand in" to activate.
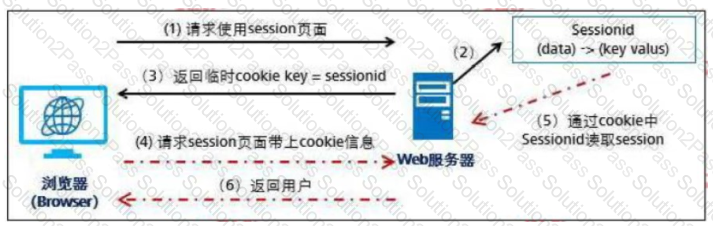
The process of a browser carrying a cookie to request resources from a server is shown in the following figure. Which of the following steps contains SessionID information in the message?
For compressed files, the virus detection system can directly detect them.
Which of the following options are correct for the configuration description of the management center ATIC? (multiple choice)
Attacks on the Web can be divided into three types of attacks on the client, server, or communication channel.
Which of the following options are common behavioral characteristics of viruses? (multiple choices)
Which of the following elements does PDCA include? (Choose 3 answers)
Which of the following options belong to the keyword matching mode? (multiple choice)
The administrator of a certain enterprise wants employees of Yangzhi to visit the shopping website during working hours. So a URL filtering configuration file is configured to divide the predefined
The shopping website in the category is selected as blocked. But employee A can still use the company's network to shop online during lunch break. Then what are the following possible reasons
some?
Which of the following is the correct configuration idea for the anti-virus strategy?
1. Load the feature library
2. Configure security policy and reference AV Profile
3. Apply and activate the license
4. Configure AV Profile
5. Submit
URL filtering technology can perform URL access control on users according to different time objects and address objects to achieve precise management of users.
The purpose of the Internet behavior.
